ISO 27k & SOC 2 Type II certified
Ransomware Protection for DevSecOps workflow
Shift left with comprehensive ransomware-proof technologies, and every-scenario-ready Disaster Recovery
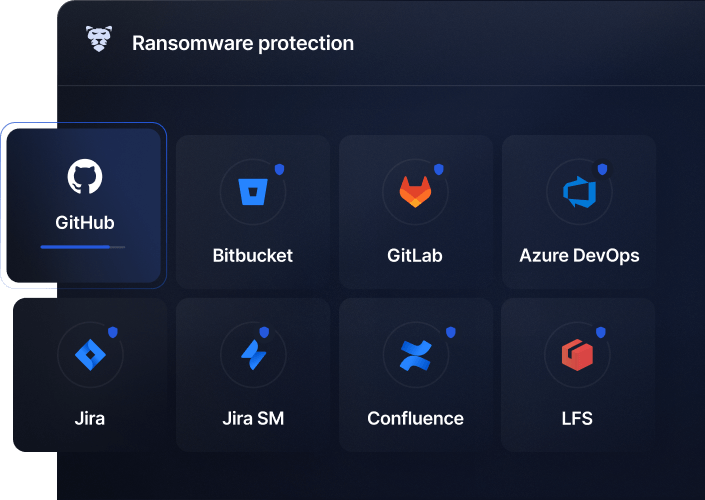
Empower the DevOps team with seamless ransomware-proof workflow
mitigate risks, and scale the security efforts across an organization. Shift left with comprehensive ransomware-proof technologies, every-scenario-ready Disaster Recovery, and best-in-class remediation controls and governance for security teams.
11 sec
This is the time interval ransomware attack attempts happen

92%
of those who paid ransom failed to get all their data back

$1.85M
is the average cost of recovery from the ransomware attack
22 days
is the average downtime period due to a ransomware attack