
Minimize Risk, Maximize Control. The Role of Least Privilege Access Control
No principle is more frequently praised yet ignored than the principle of least privilege in cybersecurity. It’s the equivalent of locking your server room but handing everyone the master key “just in case.” Considering the current threat landscape, which is rife with credential leaks, ransomware, insider incidents, and careless automation, complacency is not only costly but also dangerous. And above all, reckless.
Least privilege access control (LPAC) isn’t merely a best practice. It’s a foundational requirement for securing cloud-native environments and version control systems, such as GitHub or GitLab. That also includes, critically, backup and disaster recovery platforms.
And this is where a well-designed architecture may stand out, not only by enforcing granular permissioning for certain tasks and connected devices, but also by weaving it into the operational DNA of DevOps and backup security.
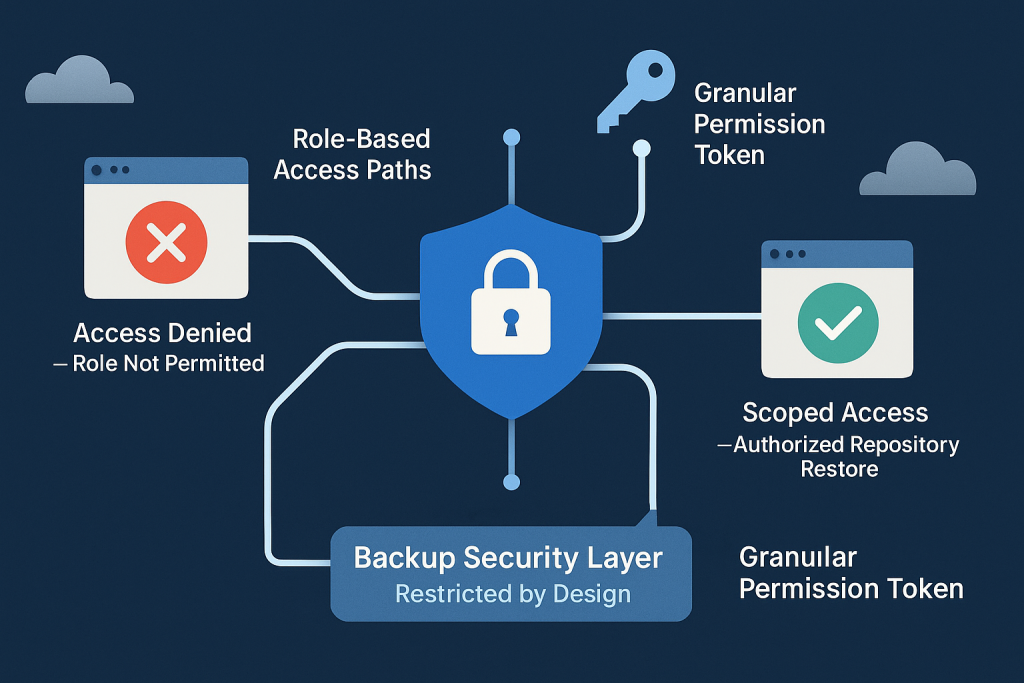
(The graphic is created with the help of AI tools)
Considering the topic, it’s good to acknowledge an uncomfortable truth. Most organizations are unaware of who has access to what, particularly regarding their privileged accounts. Even when they do, they often fail to assess whether those permissions are necessary.
Access sprawl is a silent killer. It rarely trips an alert or raises a flag, until it does (e.g., security breach). Consider the case of Code Spaces, a notorious AWS-based source code hosting service. In 2014, attackers presented the administrative (compromised) credentials and systematically destroyed customer data, access rights, and backups.
Widely considered a trust framework with the user’s role
And what was the root cause? An overprivileged admin role with privilege creep and insufficient segmentation or recovery protection. Within 12 hours, the business ceased to exist.
That was over a decade ago. Today, the stakes are higher. The tooling is more complex, and lateral movement by threat actors is more automated than ever, highlighting the need for a zero-trust approach. In incident after incident – SolarWinds, Uber, LastPass – the pattern is the same. A compromised token or user account opens the door, but it’s the excessive (even administrator) privileges that let attackers have more room to roam, like a burglar with a skeleton key.
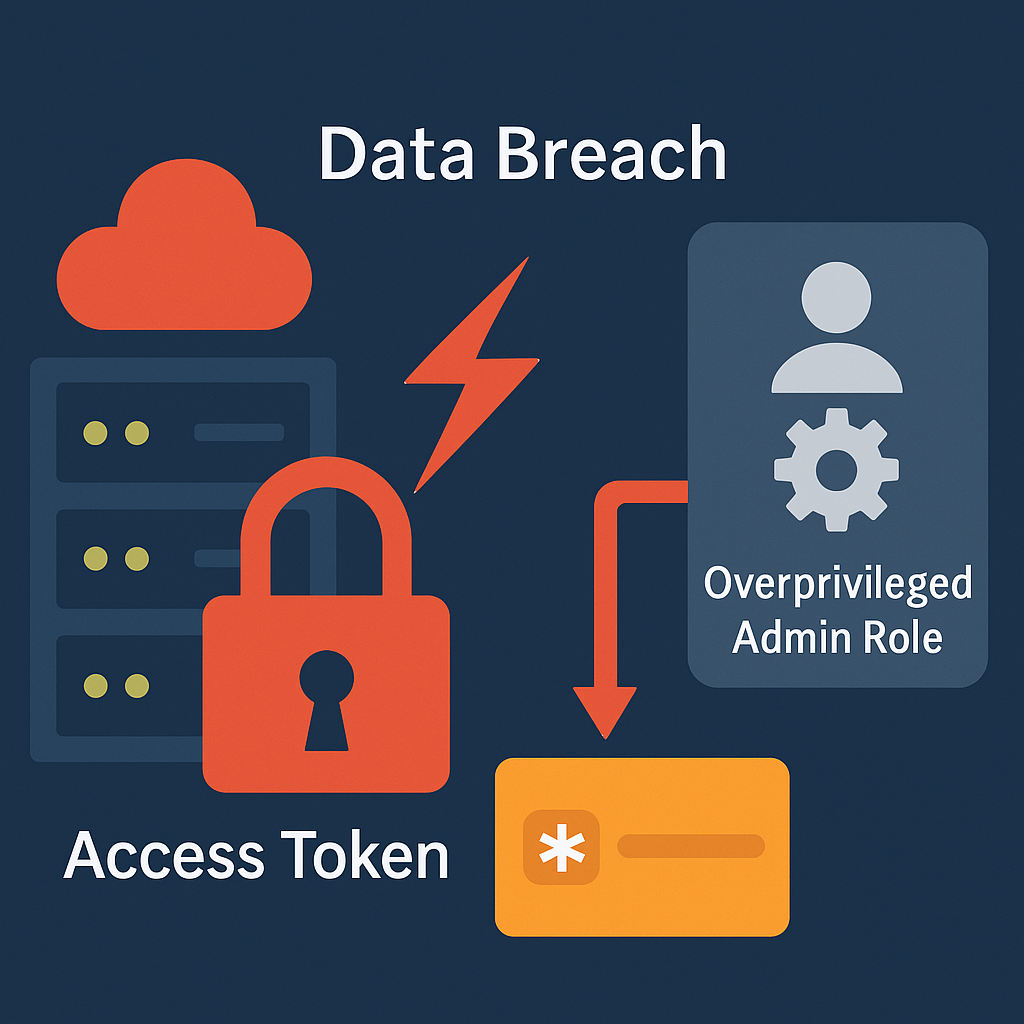
(The graphic is created with the help of AI tools)
GitProtect’s enforcement of least privilege. Architecture, not an afterthought
GitProtect is a proven all-in-one backup and disaster recovery system for 360 cyber resilience. The platform’s model doesn’t treat access control as an optional feature toggle but emphasizes effective access management. It’s embedded into how organizations define, manage, and audit their entire backup posture. That begins with Role-Based Access Control (RBAC), but goes far beyond it.
Every action in GitProtect is gated beyond explicitly defined roles and scopes. That includes:
- System administrator which is the most privileged account. This member of your team can view the settings, restore your DevOps data in case of a failure, create and run backup tasks, and manage data stores and system settings.
- Backup operator who can review the settings inside the application, and create and run backup tasks.
- Restore operator who can both view the settings and restore critical data when there is a need, e.g. test restore.
- Viewer, the least privileged account. This member of your team can only view the settings and monitor the backup performance.
Following the zero-trust framework approach
Crucially, the GitProtect system supports segregation of duties. It allows organizations to separate backup administration from access to backup contents. That means a DevOps engineer might configure backup schedules for GitHub or GitLab projects, but cannot restore or browse repositories unless granted that secondary minimal privilege (he needs to gain access first). That is something even many enterprise backup tools fail to enforce. Not to mention it needs to be regularly reviewed.
Going further, access can be scoped down to individual repos or projects, aligning with principles of blast radius reduction. When a credential is compromised, the potential damage is constrained by design, rather than through reactive mitigation.
(The graphic is created with the help of AI tools)
Mapping technical controls to business impact
IT decision-makers view LPAC as directly translating into operational resilience, audit readiness, and risk-adjusted ROI, which is crucial for effective management.
Consider these three dimensions: insider threat mitigation, compliance/regulatory pressure, and operational error containment.
Insider threat mitigation
By ensuring that no user has more access than necessary, organizations focus on limiting access to mitigate the risk posed by disgruntled employees, third-party contractors, as well as shadow IT setups. GitProtect logs all access and action events, down to restore previews. It gives security teams forensic visibility in minutes, not days.
Compliance and regulatory requirements pressure
Many regulations, such as GDPR, HIPAA, and ISO/IEC 27001, emphasize the importance of minimizing user access to sensitive information. That’s why GitProtect facilitates audit-friendly permission delegation and tracks every role assignment historically. For auditors, this is a source of trust or reliable information. For businesses, it serves as a defense against penalties.
Operational error containment
Human error remains the primary reason for data loss in DevOps pipelines across many organizations. In GitProtect, even if an operator mistakenly tries to delete or overwrite protected data, their permissions (or lack thereof) act as a circuit breaker. Scheduled backup retention policies are immutable for non-admins by default, drastically lowering the risk of accidental sabotage.
The layer most vendors overlook
In many DevOps and SaaS environments, security (with the information security concept) is mistakenly scoped to the primary application layer. Take your GitHub repos or Atlassian projects as an example. But backups are the last line of defense.
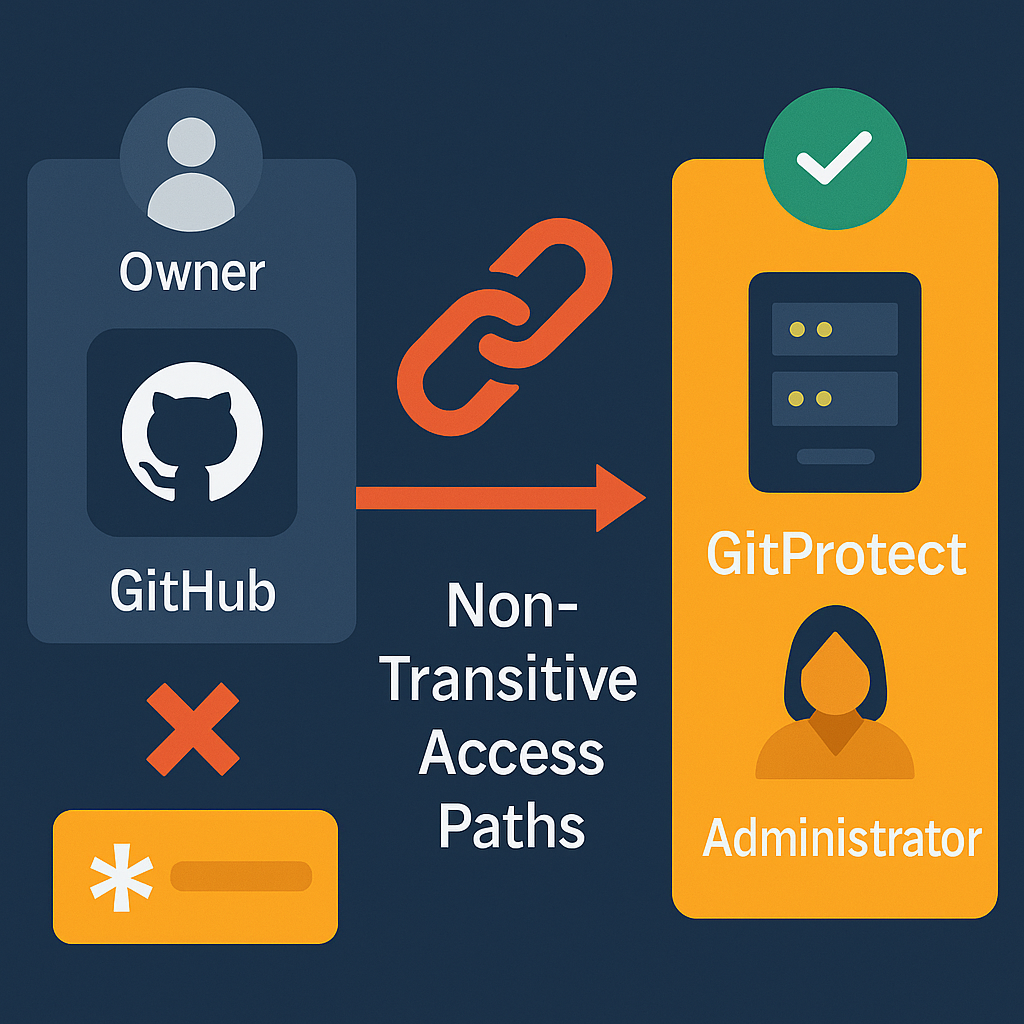
If your backup platform allows broad, unscoped access or stores admin-privileged credentials in plaintext scripts (as we’ve seen), you’ve simply duplicated your attack surface. Now, it has a recovery vector that hackers target. Fortunately, the GitProtect system isolates backup roles from platform roles.
That means that a user with “Owner” status in GitHub doesn’t inherit elevated privileges in GitProtect by default. Access paths are non-transitive. Moreover, every sensitive operation can be paired with multi-factor approval workflows, including just-in-time (JIT) access and administrator dual-consent schemes.
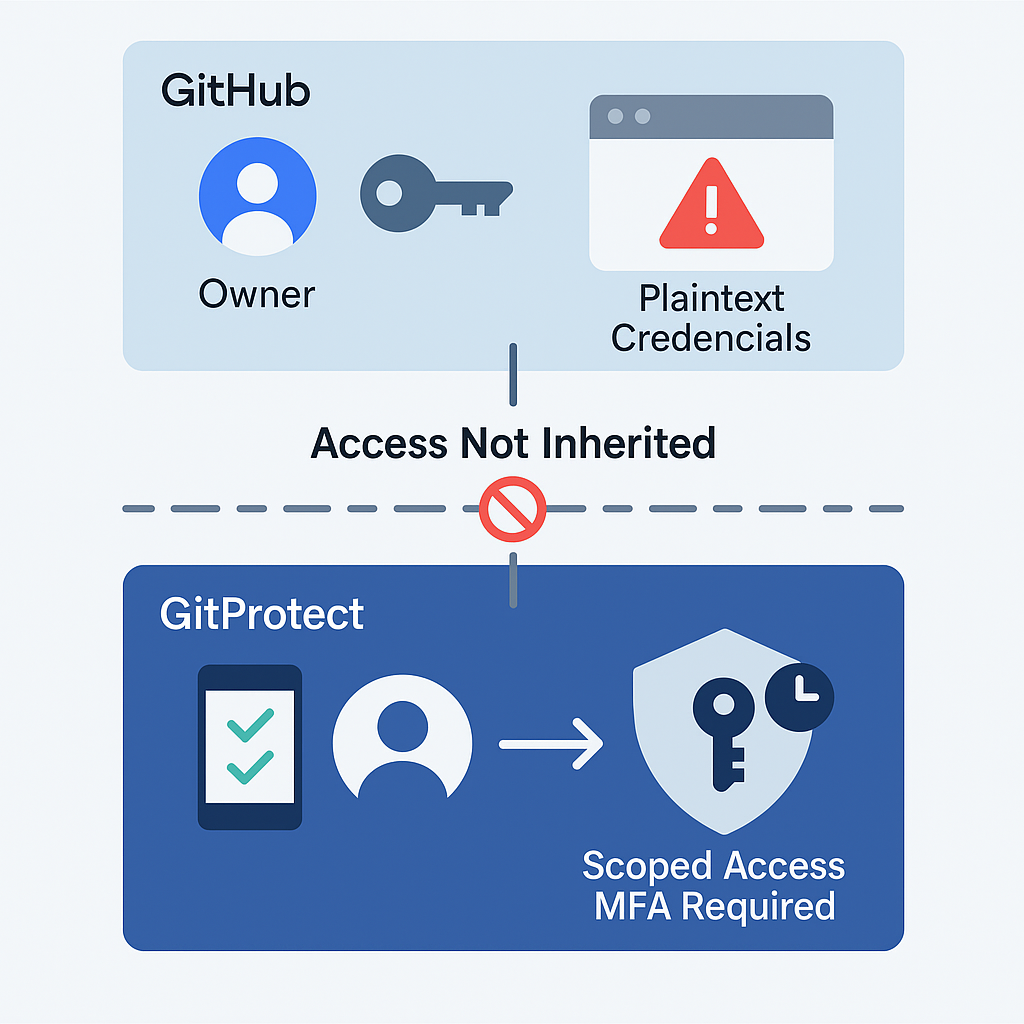
(The graphic is created with the help of AI tools)
Measurable gains with only necessary privileges
The value of least privilege isn’t hypothetical. On the contrary, organizations that apply it consistently experience a measurable difference in how control translates to stability. All the more so when it’s done within the GitProtect platform. When granted access is tightly scoped, internal friction decreases. Fewer permissions mean fewer chances to misconfigure critical components, as well as unintentionally delete protected assets.
Recovery workflows become more predictable. Only authorized individuals can initiate/approve restores and only within clearly defined scopes. This clarity is not limited to improving security posture. That also reduces support noise, strengthens audit readiness, and, of course, simplifies incident response.
Teams stop firefighting access issues. They start operating with confidence, knowing that GitProtect’s permission mode does exactly what it claims:
- prevent overreach
- minimize exposure
- ensure accountability without obstructing operations.
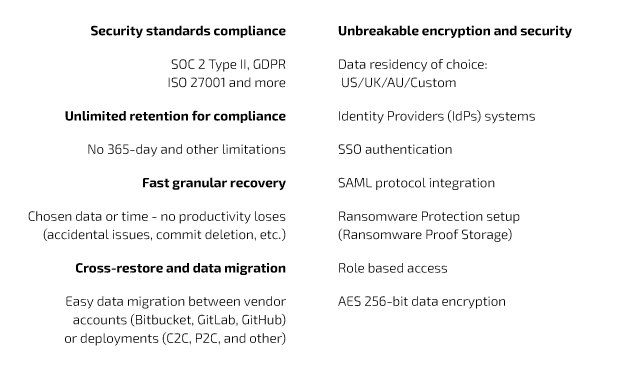
Examples of elements that come with GitProtect capabilities.
In environments where compliance is critical – ISO 27001, SOC 2, and GDPR – this approach helps meet core requirements regarding data access control and traceability. Not through added tools or last-minute reports, but as a function of how GitProtect is designed to operate from the start.
Ultimately, it’s not about restricting users. The goal is to define responsibilities so precisely that nothing gets lost in the chaos.
Conclusion. Backup security is access security (limiting access)
When disaster strikes, it’s not your primary (critical) systems that determine business continuity. It’s your backup. And if anyone – developer, intern, or automation script – can override, modify, or extract your backup assets unchecked, then your organization isn’t resilient. It’s just lucky. Until it isn’t.
In GitProtect, least privilege is enforced with surgical precision. No role is too small to be defined, and no action is too minor to be logged, emphasizing the importance of maintaining a minimum set of permissions. And finally, no permission is granted without intention. Nowadays, as attack surfaces expand and tolerance for risk shrinks, the message is clear.
Minimize access, while maximizing control. Trust nothing (zero trust), but recover everything.






