
The State of Atlassian Threat Landscape – 2024 In Review
The year 2024 was full of incidents, hacker attacks, and security flaws that were used in the wild. Were there any incidents related to the Atlassian ecosystem? Outages? Security flaws? We’ve decided to analyze it.
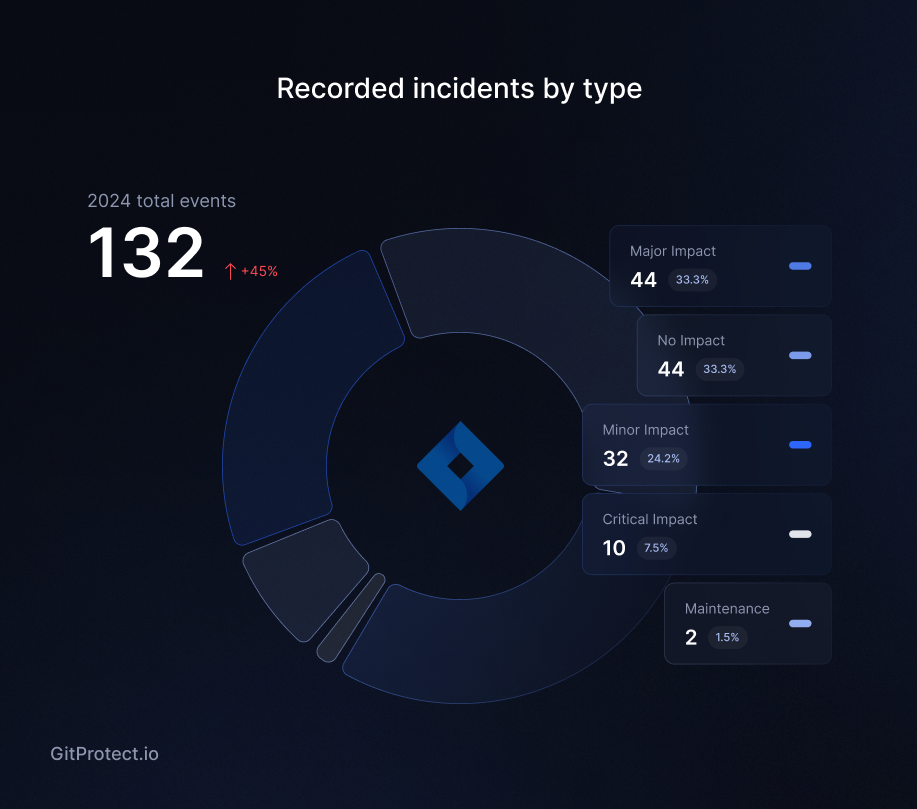
In comparison to the previous year, the number of incidents in Jira grew by 44%, and when we compare it to 2022 the percentage is even higher – 63% – in 2022 there were reported 59 incidents, in 2023 – 75, and in 2024 their number grew to 132 incidents.
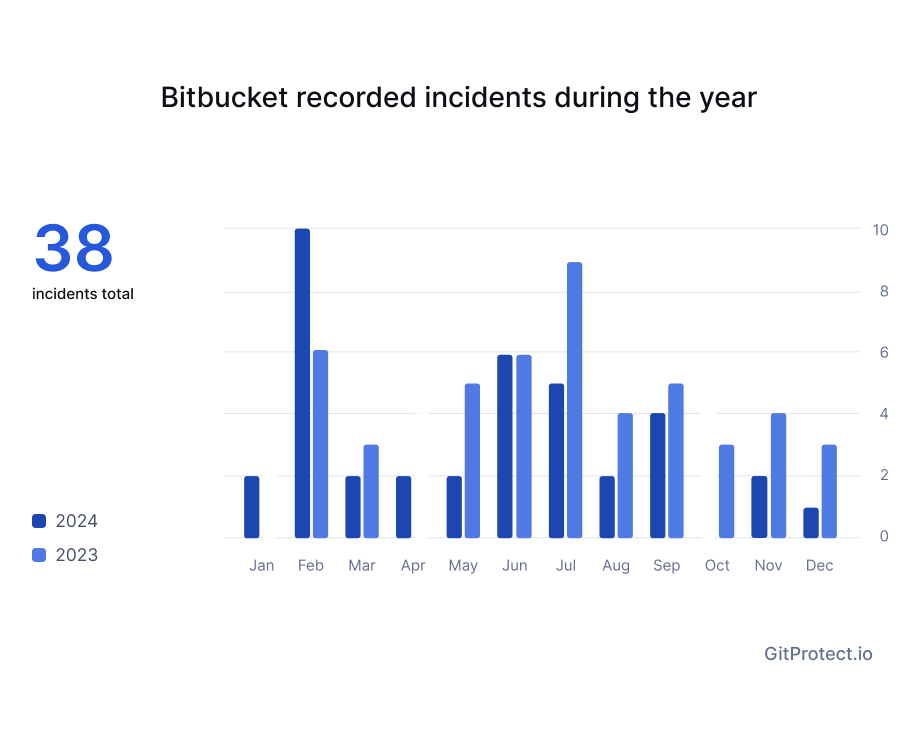
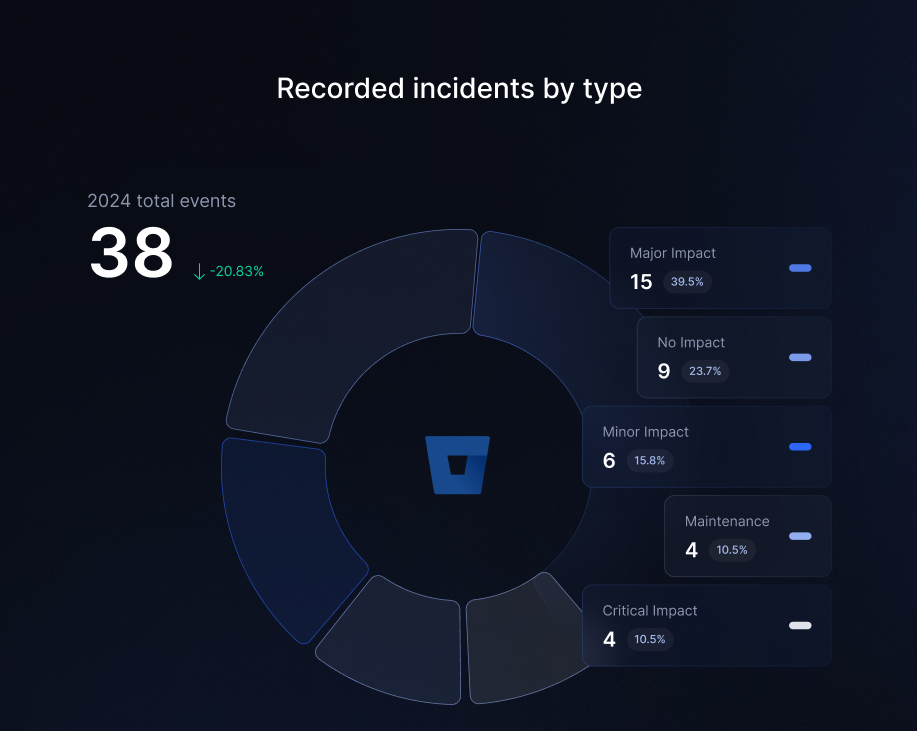
When it comes to Bitbucket, in 2024 there were 38 incidents reported, where we can see a 20% decrease compared to 2023 with 48 incidents reported.
Well, let’s dive into the topic and see which cybersecurity incidents that happened in 2024 were mentioning Atlassian products…
DECEMBER
Atlassian Status info for Bitbucket – 1 incident
⌛ Total time of incidents to last – 44 minutes
Atlassian Status for Jira – 11 incidents
⌛ Total time of incidents to last – 81 hours 22 minutes
In December, Bitbucket users might face a 44-minute incident that involved issues with attachments in Git LFS. There was a degradation of performance in viewing previews, downloading, and uploading large files.
When it comes to Jira, Atlassian faced 11 incidents, totaling more than 81 hours of degraded performance. Among them, several service disruptions affected Jira, Confluence, and JSM. Also, there were failures in Automation rules, the “Send Web Request” action, degraded AI features, and problems with Jira loading, comments, and attachments.
North Korean hackers target software developers in their malware campaign
A North Korean hacking campaign, “Contagious Interview,” aimed at software developers through fake job postings to deploy malware such as BeaverTail and OtterCookie.
The OtterCookie malware, introduced in September 2023, is delivered via loaders infecting Node.js projects, npm packages, or files built as Qt or Electron applications hosted on platforms like Bitbucket and GitHub. These loaders execute malicious JavaScript code, enabling data theft, including cryptocurrency keys, documents, and clipboard content.
OtterCookie establishes secure links to command-and-control servers and supports reconnaissance and infiltration commands, facilitating deeper attacks.
Atlassian’s Bitbucket, frequently used in these infection chains, highlights the need for vigilance in software supply chain security among developers.
NOVEMBER
Atlassian Status info for Bitbucket – 2 incidents
⌛ Total time of incidents to last – 9 h 54 min
Atlassian Status info for Jira, JWM, JSM – 14 incidents
⌛ Total time of incidents to last – 193 hours 34 minutes
Atlassian reported multiple incidents and maintenance activities affecting its products in November. Bitbucket experienced over 2 hours of degraded performance due to a missing reCAPTCHA token preventing user invitations.
Jira, Jira Work Management, and Jira Service Management were impacted by 14 incidents, resulting in a total disruption time of more than 193 hours, including a 68-hour automation issue.
Schneider Electric’s 400K rows of data are stolen in a dev platform breach
Schneider Electric confirmed a breach involving its internal project tracking platform hosted in an isolated environment. The threat actor, known as “Grep,” claims to have accessed the company’s Jira server using exposed credentials and stole 40GB of data, including 400K rows of user information, 75K unique email addresses, and other critical project data. The stolen information reportedly includes details about projects, issues, and plugins, and the attackers have demanded $125,000 to prevent data leakage.
Schneider Electric stated that its products and services remain unaffected and that its Global Incident Response team is actively investigating the incident. The attackers, part of a newly formed hacking group named Hellcat, initially sought to extort the company but have also hinted at developing ransomware for future attacks. This follows a previous breach earlier in 2023 when Schneider Electric’s “Sustainability Business” division was targeted in a Cactus ransomware attack.
Atlassian patches security flaws in Bitbucket, Jira, Confluence, and other tools
In November Atlassian addressed and patched 20 security flaws in its products, including a high-severity vulnerability to prevent potential DoS states and code execution attacks. Such flaws can often be exploited without authentication using crafted signatures or HTTP/2 requests, although detailed exploitation methods have not been disclosed.
Admins are urged to promptly install secure versions, as there are no current reports of active exploitation but also no Indicators of Compromise (IoCs) provided to detect attacks.
Protected versions include updates for Bitbucket, Confluence, Jira, Jira Service Management, Bamboo, Crowd, and Sourcetree for macOS and Windows.
OCTOBER
Atlassian Status info for Bitbucket – No incidents reported for this time
Atlassian Status info for Jira, JWM, JSM – 19 incidents
⌛ Total time of incidents to last – 428 h 44 min
In October, there were no reported incidents for Bitbucket. Hovewer there were some for Jira, JWM, and JSM. The tools were affected by 19 incidents, resulting in a total disruption time of over 425 hours.
Major issues included migration failures, automation rule disruptions, and degraded performance in user management and project access. Other problems involved delays in development information syncing and intermittent errors impacting user functionality.
Atlassian addresses 6 high-severity vulnerabilities in Bitbucket, Jira, and Confluence
In its October security bulletin, Atlassian reported patching 6 high-severity vulnerabilities across Bitbucket, Confluence, and Jira Service Management Data Center and Server products. These include CVE-2024-21147 with a CVSS score of 7.4, a Java Runtime Environment flaw leading to unauthorized access in Bitbucket, and multiple issues in Confluence, such as Moment.js library vulnerabilities, an XSS bug, and an Apache Commons Configuration flaw.
Jira Service Management updates addressed CVE-2024-7254 with a CVSS score of 7.5, a Protobuf buffer overflow that could disrupt service availability.
While none of these vulnerabilities were known to have been exploited in the wild, Atlassian urged users to apply the updates promptly.
Cisco’s data breach – confirmed
On October 14th, 2024, a hacker, known as IntelBroker, announced that he managed to breach Cisco and steal some company’s data, including Jira tickets, GitHub and SonarQube projects, source code, confidential documents, etc.
Cisco’s investigation determined its systems were not breached; instead, the data was accessed from a public-facing DevHub environment containing customer resources like scripts and source code. Cisco has found no evidence of sensitive personal or financial data being compromised but is continuing its investigation.
In response, the company has disabled public access to the affected website.
SEPTEMBER
Atlassian Status info for Bitbucket – 4 incidents
⌛ Total time of incidents to last – 4 hours 25 minutes
Atlassian Status info for Jira, JWM, JSM – 19 incidents
⌛ Total time of incidents to last – 72 hours 55 minutes
Atlassian experienced 23 incidents in total for Bitbucket, Jira, JSM, and JWM. Four incidents happened in Bitbucket’s infrastructure, totaling around 3 hours of their occurrence, including issues involving reCAPTCHA errors during signup and performance degradation.
The number of incidents impacting Jira, JWM, and JSM was 19, which lasted in total almost 73 hours. There were some issues with workflow provisioning, asset loading, automation rules, and email replies creating new tickets instead of comments.
Six high-severity Atlassian security flaws are patched
September brought 6 patches for high-severity vulnerabilities in the Atlassian ecosystem. The service provider addressed security flaws in Bitbucket, Jira, Jira Service Management, Confluence, BambooCrowd, and Sourcetree, which could allow attackers to create DoS states or execute malicious code. Exploits may involve prepared signatures or special HTTP/2 requests and, in some cases, may not require authentication.
Although there were no reports of active exploitation in the wild, Admins were urged to apply the updates promptly to secure their systems.
AUGUST
Atlassian Status info for Bitbucket – 2 incidents
⌛ Total time of incidents to last – 2 hours 20 minutes
Atlassian Status info for Jira, JWM, JSM – 15 incidents
⌛ Total time of incidents to last – 313 hours 2 minutes
In August, Atlassian reported 3 incidents in Bitbucket lasting in total of 3+ hours, and 15 incidents in Jira, JWM, and JSM that lasted for over 310 hours.
The issues ranged from login timeouts and functionality degradation in workflows, backlogs, and assets in Jira to degraded performance with the Bitbucket website.
JULY
Atlassian Status info for Bitbucket – 5 incidents
⌛ Total time of incidents to last – 38 hours 09 minutes
Atlassian Status info for Jira, JWM, JSM – 5 incidents
⌛ Total time of incidents to last – 29 hours 33 minutes
Atlassian reported 5 incidents for Bitbucket in July, totaling over 14 hours of effect, with two major incidents causing around 30 minutes of downtime and around 90 minutes of Bitbucket pipeline disruption.
Regarding Jira, JWM, and JSM, Atlassian had to deal with 5 incidents as well which resulted in over 29 hours of effect. The incidents included degraded performance in services and SLA data loss.
Hackers exploit critical Atlassian flaw to connect servers in mining networks
According to cybersecurity researchers from Trend Micro, hackers could actively exploit a critical vulnerability, tracked as CVE-2023-22527 with a CVSS score of 10 (out of 10!), in Atlassian’s Confluence Data Center and Server products.
The security flaw allows Remote Code Execution (RCE) and poses serious risks to affected systems. The vulnerability, present in older versions, has been actively used by threat actors for crypto-jacking, with a surge in attacks observed from June to July 2024.
Attackers deploy sophisticated scripts to disable security measures, spread via SSH, and establish unauthorized cryptocurrency mining, compromising system integrity and resources.
Cybersecurity experts recommend immediately updating Confluence to mitigate the vulnerability and prevent further exploitation.
JUNE
Atlassian Status info for Bitbucket – 6 incidents
⌛ Total time of incidents to last – 6 hours 04 minutes
Atlassian Status info for Jira, JWM, JSM – 6 incidents
⌛ Total time of incidents to last – 226 hours 26 minutes
In June, Atlassian reported 6 incidents for Bitbucket, which lasted in total for over 50 hours. The incidents included degradation in the work of pipelines and error responses across the product.
As for Jira, JWM, and JSM, there were also 6 incidents recorded, totaling over 226 hours of disruptions. Among the cases that Atlassian was dealing with were slow performance, issues with the option to copy production data to sandbox, etc.
Club Penguin fans stole 2.5 GB of internal corporate data in Disney Confluence server breach
Club Penguin fans exploited Disney’s Confluence server to access old internal game data but inadvertently stole 2.5 GB of sensitive corporate information, including developer tools, internal infrastructure, advertising plans, and business documentation.
Source: Bleeping Computer – SENSEI character sheet from leaked documents
“Lot more files here including internal api endpoints and credentials for things like S3 buckets,” is reported in the BleepingComputer article.
The breach occurred using previously exposed credentials and included internal API endpoints, S3 bucket credentials, and links to developer resources, potentially increasing Disney’s exposure to further attacks.
Atlassian’s Confluence platform, central to Disney’s documentation, was the target of the breach, highlighting the risks of improperly secured or outdated credentials in enterprise environments. While the initial focus of the attackers was nostalgic Club Penguin data, the newer data with information from 2024 was also circulating on DIscord.
A hacker claims to have breached Apple
A threat actor known as IntelBroker claims to have leaked internal Apple code in a data breach in June 2024, targeting tools used within Apple’s corporate network, including AppleConnect-SSO.
Source: Heise Online
The leaked data, analyzed by cybersecurity firm AHCTS, contains proprietary plugins and configurations for integrating Apple’s authentication systems with Atlassian Jira and Confluence, posing significant cybersecurity risks but not affecting end-user products or services.
MAY
Atlassian Status info for Bitbucket – 2 incidents
⌛ Total time of incidents to last – 3 hours 13 minutes
Atlassian Status info for Jira, JWM, JSM – 10 incidents
⌛ Total time of incidents to last – 485 hours 56 minutes
In May, Atlassian reported 2 incidents for Bitbucket, resulting in 3 hours and 13 minutes of degraded performance in Git LFS operations and Bitbucket pipelines, and 10 incidents occurred in Jira services, totaling over 485 hours of partial disruptions, primarily driven by scheduled infrastructure maintenance in Brazil that caused extended outages for Free edition users.
Hackers use authentication secrets leaked as plaintext in Atlassian Bitbucket artifact objects in their malicious activity
Threat actors exploited plaintext AWS authentication secrets exposed in Atlassian Bitbucket artifact objects to breach accounts. A cyber security firm, Mandiant, discovered this vulnerability while investigating AWS access abuse, revealing that sensitive data, such as secured variables, could unintentionally appear in artifact files during CI/CD processes.
Despite Bitbucket’s design to store secured variables in encrypted form, developers may unknowingly export these secrets as plaintext to artifact files via commands like printenv. If these artifacts are stored in public repositories, attackers can access and misuse the plaintext secrets.
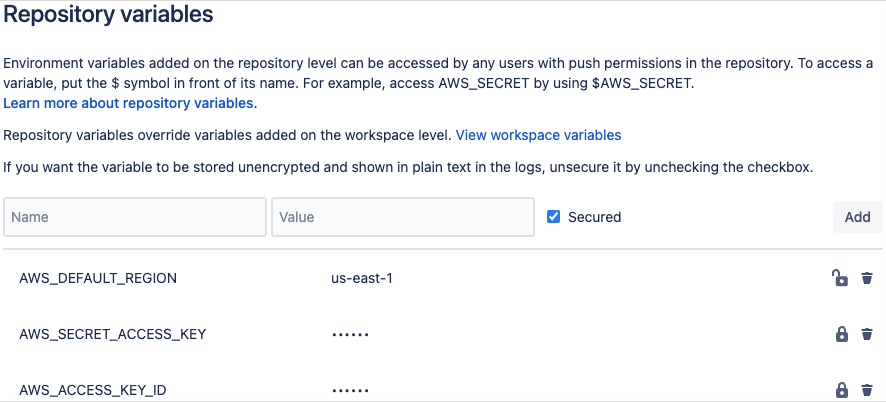
Source: Bleeping Computer – How to store variables secured in Bitbucket
Mandiant noted that this often occurs when developers misconfigure pipeline scripts or use artifacts for debugging without considering security implications.
To mitigate these risks, developers should use dedicated secret management tools, carefully review artifact content, and implement code scanning to detect and remove sensitive data before deployment.
Bleeping Computer / The Cyber Express
APRIL
Atlassian Status info for Bitbucket – 2 incidents
⌛ Total time of incidents to last – 10 hours 15 minutes
Atlassian Status info for Jira, JWM, JSM – 5 incidents
⌛ Total time of incidents to last – 13 hours 48 min
Two incidents were reported in Bitbucket in April. There were issues with Admin portal feature access and pipelines, totaling over 8 hours of lasting incidents.
Jira services experienced issues for over 13 hours in total – there were 5 incidents, including intermittent errors with linking issues in the issue view, scheduled maintenance, and interruptions with installing apps on user’s instances.
Critical Atlassian flaw allows Linux variant of cerber ransomware deployment
Threat actors exploit CVE-2023-22518, with the CVSS score of 9.1 out of 10 maximum, in the wild. This critical vulnerability in Atlassian Confluence servers, to deploy the Cerber ransomware variant. The vulnerability allows attackers to reset Confluence, create an admin account, and take control of the system, leading to potential full compromise.
Using this access, attackers can install the Effluence web shell plugin to execute commands and deploy the ransomware payload, which encrypts files with a .L0CK3D extension and drops ransom notes without exfiltrating data. Cerber’s primary payload, written in C++, acts as a loader for other malware retrieved from a command-and-control server, highlighting a rare but sophisticated use of pure C++ in modern ransomware.
The attack’s efficacy is often limited, as the ransomware typically only encrypts Confluence-specific data, which may be backed up in well-configured systems. This limitation reduces the likelihood of victims paying ransom. Which highlights the importance of having a reliable backup provider, like GitProtect.io.
The rise of Cerber coincides with the emergence of other ransomware families and variants exploiting leaked source codes, such as LockBit, to create customized threats. Security researchers emphasize the importance of strong security measures, regular patching, and fostering a cybersecurity-aware culture to mitigate such evolving threats.
MARCH
Atlassian Status info for Bitbucket – 2 incidents
⌛ Total time of incidents to last – 28 minutes
Atlassian Status info for Jira, JWM, JSM – 7 incidents
⌛ Total time of incidents to last – 24 hours 35 minutes
In March, Atlassian reported 2 incidents for Bitbucket, including issues with Admin portal feature access and the Cloud service degradation that lasted for over an hour.
In Jira services, there were reported 7 incidents that resulted in over 24 hours of issues. The incidents included the impossibility of scheduling data residency migrations, issues with creating issues and transitions, etc.
FEBRUARY
Atlassian Status info for Bitbucket – 10 incidents
⌛ Total time of incidents to last – 130 hours 52 minutes
Atlassian Status info for Jira, JWM, JSM – 15 incidents
⌛ Total time of incidents to last – 128 hours 58 minutes
Atlassian reported 10 incidents for Bitbucket and 15 incidents for Jira services in February 2024.
Bitbucket experienced in total of 22+ hours of service issues, including service disruptions, fails in user searches, pipelines stuck in a pending state, and some authentication errors.
Jira, JSM, and JWM saw around 129 hours of issues, which included issues with automation and connecting apps, SLA issues, 503 errors, and service disruptions.
Cloudflare data breach due to auth token stolen in Okta attack
The bad actor managed to breach Cloudflare’s internal Atlassian server and access the company’s Jira bug database, Bitbucket source code management system, and Confluence wiki.
The attacker initially gained access to the company’s systems on November 14, 2023, using credentials stolen during an earlier Okta breach and later established persistence using the ScriptRunner plugin.
“They then returned on November 22 and established persistent access to our Atlassian server using ScriptRunner for Jira, gained access to our source code management system (which uses Atlassian Bitbucket), and tried, unsuccessfully, to access a console server that had access to the data center that Cloudflare had not yet put into production in São Paulo, Brazil,” explained Cloudflare.
Once the activity on November 23 was detected, Cloudflare cut off the hacker’s access by November 24 and began a detailed forensic investigation on November 26. Remediation included rotating over 5K production credentials, reimaging nearly 4,900 systems, segmenting test environments, and ensuring the security of a São Paulo data center targeted during the breach, which was unsuccessful.
Despite the extensive measures, Cloudflare confirmed no customer data, systems, or global network configurations were affected. The attackers appeared focused on gathering information about Cloudflare’s network architecture and security to establish a deeper foothold.
Bleeping Computer / The Hacker News / Dark Reading
JANUARY
Atlassian Status info for Bitbucket – 2 incidents
⌛ Total time of incidents to last – 1 hour
Atlassian Status info for Jira, JWM, JSM – 7 incidents
⌛ Total time of incidents to last – 135 hours 26 minutes
In January, Atlassian reported 2 incidents for Bitbucket, totaling 5 hours of impact, including performance degradation in Forge app invocations and an outage in Atlassian Intelligence functionality.
For Jira, JWM, and JSM, there were 7 incidents leading to over 135 hours of lasting incidents, including issues in sandbox sites, SCIM provisioning syncs, and webhook functionality, among others.
The most noticeable incident that affected Jira users was an outage that occurred on January 15th and lasted for over 3 hours.
The error message that users may see on Jira panels and widgets
On the Jira Status page, Atlassian explained the incident was triggered by “a scheduled database upgrade within the central service that supports the Atlassian Marketplace.”
Source: Bleeping Computer – HTTP 503 error message that customers might see when accessing Jira Cloud services
Takeaway
In 2024, Bitbucket reported 38 incidents of different impact (critical issues, major impact, minor impact, no impact and maintanance), which lasted in total for over 200 hours, while Jira services, including Jira Software, Jira Service Management, and Jira Work Management, experienced in total of 132 incidents that lasted for about 2131 hours… which makes around 266 working days!
Cybercriminals are becoming more aggressive in their attacks, and we can see it not only in the example of Atlassian but also in GitHub, GitLab, and Azure DevOps. It means that organizations should take security more seriously and implement security mechanisms to make sure that their infrastructure as well as data is safe.
Such measures may include in-time updates, implementation of the least privilege principle, and backup of critical DevOps and project management data.
GitProtect is a professional backup and DR tool for DevOps that can assist organizations in building backup and Disaster Recovery strategies, ensuring security, data availability, and compliance with strightened security protocols.
[FREE TRIAL] Ensure compliant GitLab backup and recovery with a 14-day trial🚀
[CUSTOM DEMO] Let’s talk about how backup & DR software for GitLab can help you mitigate the risks






