
Why Immutable Backups Are Essential for Data Security in DevOps
Immutable backups (IB) are a robust defense mechanism against the consequences of cyberattacks. The latter can be considered an “evolving constant,” while DevOps environments closely link development and operations. IT teams adopt CI/CD pipelines and centralized applications utilizing multi-cloud deployment. And that usually translates into a growing attack surface (check 2024 DevOps Threats Unwrapped).
In this context, several threats can compromise the entire environment, causing various unwanted effects, from data breaches to cryptojacking. It’s enough to mention:
- risk related to privileged credentials
- misconfigured cloud resources
- side-channel attacks (often unnoticed)
- supply chain attacks, and more.
The obvious conclusion is that protecting critical data – code repos, application artifacts, and various configuration files – is paramount. This is where immutable backups and (data recovery) become more than handy.
75% of security professionals have observed an increase in cyberattacks over the past year.
Cost of a Data Breach Report 2024, IBM
What are immutable backups
In popular understanding, immutable backups are data copies that cannot be changed, including overwritten or deleted. The information remains intact, thus maintaining its integrity. In other words, it guarantees the files are unchangeable for a predefined retention period.
The above is primarily a must in environments or ecosystems potentially exposed to threats such as:
- ransomware
- accidental data loss
- malicious insider threats.
At the same time, immutable backups help organizations store accurate and uncompromised records in compliance with regulatory requirements and industry standards.
Why decision-makers should prioritize immutable backups for data protection
For decision-makers, immutable backups play a critical role in strengthening data security as one of the vital elements of business continuity. Below are 7 examples of key points:
1. Strong protection against ransomware
Immutable backups are effective against ransomware attacks. Firms can recover their data since the copies cannot be altered or erased, even if attackers encrypt the original files. This allows IT teams to minimize financial losses and operational disruptions.
2. Maintaining data integrity (assurance)
Recoverable data, free from corruption, provides an advantage, enabling businesses to maintain accurate operations. All ventures stay compliant with necessary or mandatory regulations and industry standards.
3. Regulatory compliance and industry standards
Many businesses face stringent legal requirements for data retention and protection. As such, they need solutions that provide secure and unchangeable data archives to facilitate compliance audits and reduce the risk of substantial fines.
4. Faster recovery times
As reliable recovery points, immutable records streamline disaster recovery processes, leading to quicker operation restoration after incidents. That reduces downtime and associated costs. It’s a significant benefit for sectors where any operational pause has substantial financial impacts.
5. Accidental deletion prevention
A solution (IB) eliminates the risk of accidental data loss, which causes critical information to remain retrievable. It’s essential for maintaining business operations and mitigating the impact of potential human errors.
6. Data protection cost-effectiveness
Raising cybercrime costs force firms to invest in cost-effective countermeasures. Immutable backups can be considered a safety tool “shielding” businesses from the costs related to data loss.
7. Forensic analysis facilitation
Immutable copies significantly support accurate forensic analysis in the event of a security breach. The unalterable nature of these backups eliminates the risk of evidence tampering. They enable organizations to:
- thoroughly investigate incidents
- understand attack methods
- enhance their future defenses.
A more technical view on an immutable backup solution
The concept of immutable backups is closely tied to the use of immutable objects within storage systems. The solution utilizes a data structure (entity) where any attempt to change the object’s state results in the creation of a new object instead of an altered original (if a given system allows for such multiplication).
In general, immutable objects are a fundamental concept in many programming paradigms, especially functional programming. Here, the immutability is a key feature for managing state and side effects.
The key characteristics of immutable solution are (among others):
| Unchangeable state | Let’s repeat it again: once an immutable object (backup) is created, its fields cannot be modified. A good example may be the classes “String” and “Integer” in the Java language. They are immutable, so any attempt to modify them will return a new instance with a changed value. The original stays the same. |
| Thread safety | As object alteration is forbidden, multiple threads can access the object without the option of data corruption or race conditions. |
| Memory efficiency | The lack of data alteration possibility can support memory optimization. Memory optimization can involve sharing references among identical objects, which considerably reduces memory overhead. |
| Ease of reasoning | The unchanging nature of immutable objects (backups) simplifies their reasoning and analysis. This makes it easier to foresee their functioning and behavior, including side effect immunity. |
Describing how immutable backups work, we can distinguish core technologies and mechanisms utilized for their creation and maintenance.
69% of decision-makers consider immutable data storage essential to their corporate cybersecurity.94% either already rely on immutable data storage or plan to implement it within the next 12 months, and an additional 2% plan to deploy it within the next three years.
Source: Resilience Forward.
WORM technology
The Write Once, Read Many (WORM) approach is the core principle of managing immutable backups. It ensures that the data stored can only be written once but read multiple times—no unauthorized changes to the backup data are allowed within the retention period.
WORM can be applied across various storage mediums, including:
- tape storage – cost-effective and suitable for long-term data preservation
- disk storage – offers rapid access and recovery times for critical data processes
- cloud storage – scalable and flexible and often integrated with object storage services.
Object locking mechanisms
Immutable backup solutions use object storage with built-in locking features. Such mechanisms allow for the enforcement of retention policies that prevent changes in backup objects until a specified expiration date.
They usually operate in two modes:
Governance mode
It allows users with specific permissions to modify retention settings under strict conditions.
Compliance mode
This one prevents any modifications to locked objects, thus providing adherence to regulatory compliance.
Encryption and access control
Most immutable backup services integrate data encryption and robust access control. The first secure backup data both in transit and at rest. The second utilizes role-based access control, thus limiting interactions with immutable storage for authorized users only.
By creating a cryptographically verifiable chain of custody, immutable backups maintain data’s authenticity and compliance with legal and audit requirements. The feature is vital in preventing disputes and providing reliable recovery from a data loss event.
While the survey data shows IT leaders resoundingly agree that immutability is a cornerstone of cyber security strategy, 31% still did not report it as essential. Here’s the reality: being able to restore quickly from an immutable backup means the difference between a successful and unsuccessful ransomware attack.
Paul Speciale, CMO, Scality, resilienceforward.com
Implementation strategies for immutable backup data protection
Considering immutable backup implementation, the market usually follows two approaches.
Automated retention policies
Automated policies enable consistent enforcement of retention rules. That reduces the risk of accidental policy violations and optimizes the use of backup storage.
Multi-layered backup strategies
Combining immutable backups with more traditional methods enhances overall data protection. While immutable backups protect vital data, conventional solutions may address less critical or temporary datasets.
Challenges and considerations
Of course, immutable backups involve challenges and elements worth considering, like in every technology.
Cost management
Implementing WORM and managing immutable infrastructure can increase expenses compared to traditional backups.
Complexity
Effective deployment needs expertise to configure and maintain backup and recovery systems.
Storage optimization
Planning is necessary to balance storage capacity with performance when handling immutable data.
The most efficient way of implementing and managing immutable backups
If you want to fully automate the backup and recovery process while maintaining full control over the process, it is worth choosing a mature tool that fully supports the needs of DevOps teams.
For example, the every-scenario-ready DevOps Backup and Disaster Recovery tool for 360 cyber resilience, GitProtect.io, focuses on immutable backup data. It’s coupled with advanced features like:
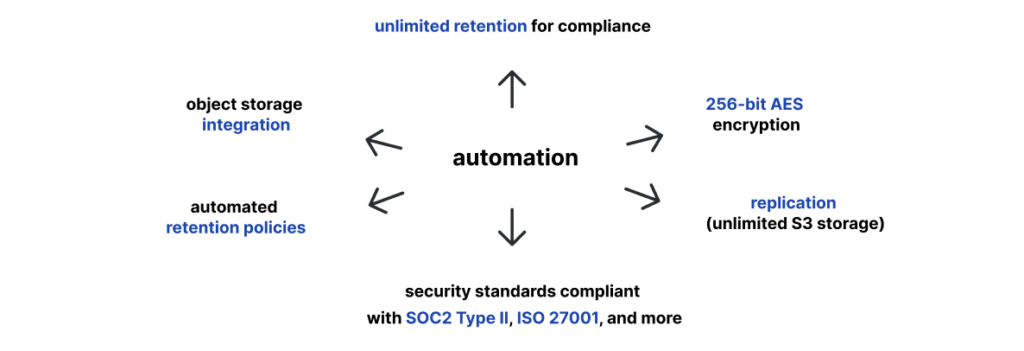
These and many more capabilities make the tool ideal for safeguarding production servers and maintaining business continuity. The solution allows the business to protect against data loss events and provides organizations with the functionality to adapt to evolving cybersecurity threats.
Providing a sound and comprehensive solution for immutable backups in DevOps environments, GitProtect integrates technologies and security measures to safeguard critical data and ensure valuable data integrity and availability.
Among key benefits of GitProtect for immutable backups, your team, department, or business can utilize:
1. Enhanced data integrity and security
GitProtect ensures that backed-up data cannot be altered, deleted, or tampered with once stored.
It allows you to raise Backup Integrity Rate and lower Unauthorized Access Attempts.
2. Regulatory compliance
Automated retention policies for storing undeletable data and audit trails to meet regulatory requirements like GDPR, HIPAA, and CCPA.
This way, you can improve Compliance Audit Pass Rate and Retention Policy Adherence.
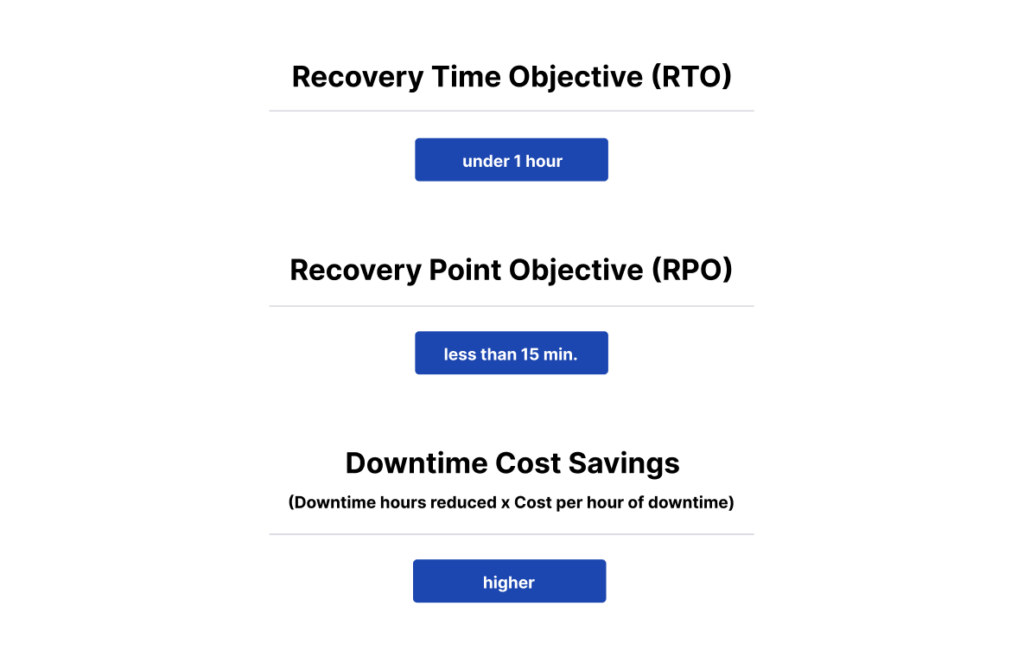
3. Rapid disaster recovery
GitProtect’s volume snapshots and granular recovery enable fast restoration of critical data.
That translates into:
4. Data encryption and access control
Data encryption in transit and at rest and the implementation of role-based access control allow IT teams to increase the success rate of Backup Automation (up to 99.9%) and Pipeline Integration Coverage.
5. Seamless integration with DevOps tools
An automated backup process integrated with CI/CD pipelines gives the opportunity to increase the percentage of backups successfully executed without manual intervention (Backup Automation Success Rate).
The same goes for the percentage of CI/CD pipelines with integrated backup workflows (Pipeline Integration Coverage).
6. Scalability and cost efficiency
The scalable, immutable infrastructure supports growth while optimizing storage costs. It involves optimizing Backup Storage Utilization and dropping Storage Cost Per GB below industry benchmarks.
7. Improved operational resilience
Reliable solution for immutable backups for production servers and critical data positively influences:
- Business Continuity Rate
- Incident Recovery Time (less than 1 hour)
- Data Loss Incident Frequency.
8. Long-term data preservation
GitProtect supports storing immutable data for archival and compliance purposes. That improves Data Retention Compliance and Historical Data Accessibility.
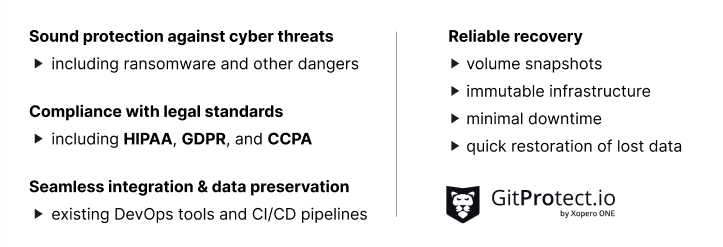
Summary
GitProtect, a robust data protection solution, offers businesses a secure and scalable way to create immutable backups. That ensures data integrity and helps organizations comply with industry regulations.
By streamlining backup processes and integrating seamlessly with existing workflows, GitProtect empowers DevOps teams to enhance operational resilience.
Key performance indicators, such as Recovery Time Objective (RTO), Recovery Point Objective (RPO), and storage utilization, are tracked to demonstrate the effectiveness of data protection investments and their impact on organizational success.
[FREE TRIAL] Ensure compliant DevOps backup and recovery with a 14-day trial 🚀
[CUSTOM DEMO] Let’s talk about how backup & DR software for DevOps can help you mitigate the risks






