
A Comprehensive Guide To The NIST Cybersecurity Framework
Businesses are turning to structured cybersecurity approaches like the NIST Cybersecurity Framework (CSF) to protect data from breaches. Especially since the latter’s cost is expected to reach $10.5 million in 2025. The CSF’s core functions (Govern, Identify, Protect, Detect, Respond, Recover) can help mitigate digital risks.
All the more so, that structured approach
- enhances resilience
- protects critical assets
- fosters a proactive cybersecurity culture.
Understanding the NIST Cybersecurity Framework (CSF) 2.0
Developed by the National Institute of Standards and Technology (NIST) in the U.S. Department of Commerce, the tool helps businesses protect their networks and data.
The NIST Cybersecurity Framework (CFS) is a voluntary guide for companies on managing and reducing potential cybersecurity threats. The whole idea is based on core functions.
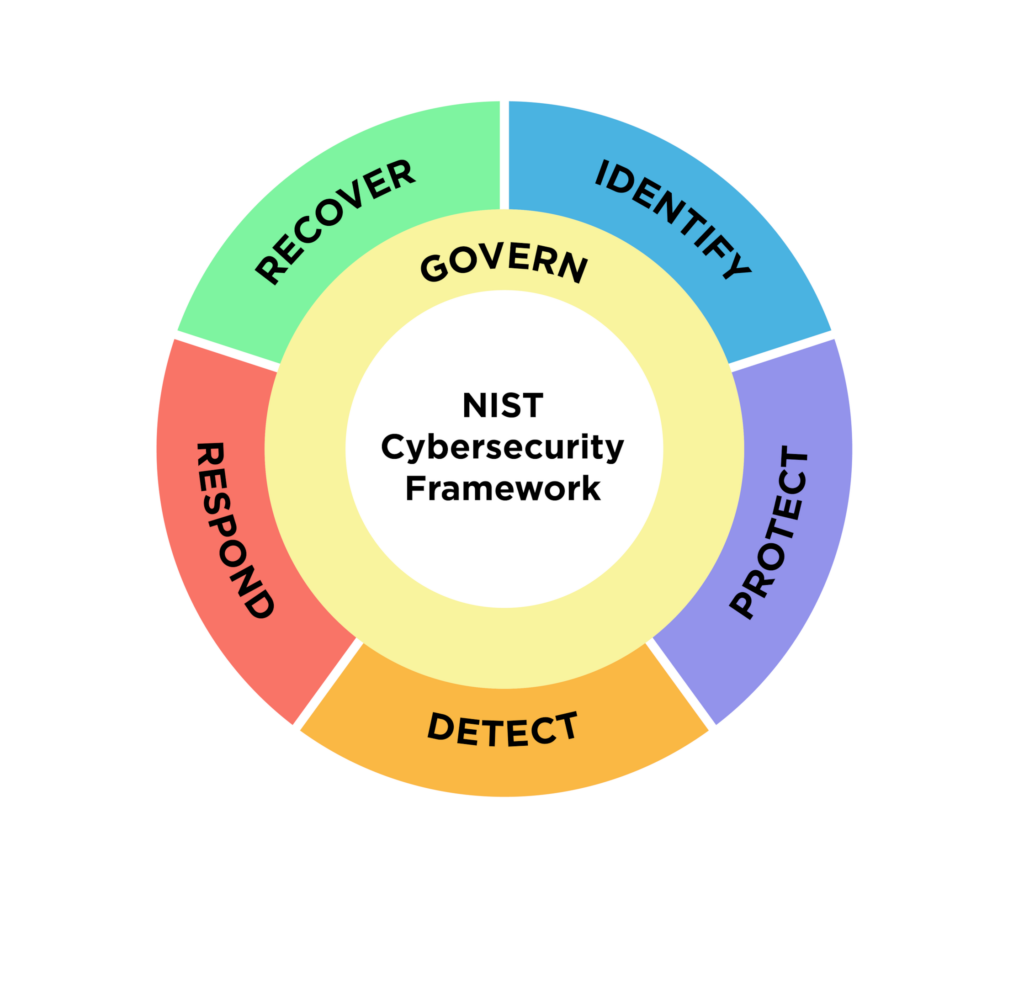
NIST Cybersecurity Framework 2.0. Source: nist.gov
Core functions of the NIST Cybersecurity Framework (CSF) 2.0
Each function guides organizations through different stages of system security, from understanding and mitigating risks to responding to and recovering from incidents. Together, they provide building blocks for cybersecurity strategy.
Identify (ID). Knowing your cybersecurity potential
The Identify function lays the foundation for all cybersecurity activities by helping firms understand their systems, assets, and risks. It helps to develop a (critical) risk management strategy that matches the organization’s unique environment and objectives.
Asset management
It begins with creating a complete inventory of all devices, software, and data critical to your operations and services. That includes everything from laptops and servers to personal (employees’ smartphones), IoT devices, and software applications.
Business environment
Security investments support core business functions when you align cybersecurity activities with your organization’s:
- mission
- business objectives
- regulatory requirements.
Documentation and data flow
It’s vital to understand what type of data (information) your company uses for data security. Knowing where the files are stored and how they’re utilized is also critical. It’s even more important if external partners and contracts are involved.
Protect (PR). Prevention by implementing safeguards
This function aims to develop and implement appropriate safeguards to ensure the security of critical services and limit the impact of potential cybersecurity incidents.
Access control
The approach involves implementing multi-factor authentication (MFA) and role-based access control (RBAC) to manage who is accessing your systems and data securely. It’s crucial to limit access to authorized personnel only.
Data security
It includes sensitive data encryption at rest and in transit. If data is intercepted, it remains inaccessible to unauthorized parties.
Regular integrity checks are also vital. It ensures that only approved changes are introduced to the dataset. The same goes for deleting or destroying data when it’s no longer in use.
Secure configuration
You need to maintain secure configurations for hardware and software assets by:
- enforcing default security settings
- applying updates promptly
- establishing baseline security configurations to minimize vulnerabilities.
Incident response planning
All incident response procedures must be adequately created and updated to guide your teams’ actions during a cyber attack. It’s the only way to prepare for scenarios like ransomware, phishing attacks, or data breaches.
Regular backups
Establish a routine data backup regimen. Utilize automated solutions or built-in backup features. Maintain an offline backup to safeguard against ransomware attacks. Periodically validate backup integrity and restoration capabilities.
Proactive protection strategies allow firms to avoid significant damage in case of potential cybersecurity events.
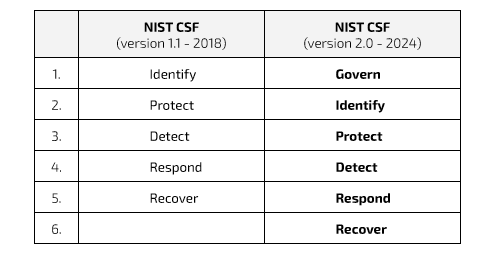
Based on NIST Cybersecurity Framework versions. Source: nist.gov.
Find out how to build a reliable backup strategy for your DevOps environment:
📌 GitHub backup best practices
📌 Bitbucket backup best practices
📌 Azure DevOps backup best practices
📌 GitLab backup best practices
📌 Jira backup best practices
Detect (DE). Real-life digital security threats identification
This element’s main focus is on creating mechanisms to identify cybersecurity issues quickly and accurately. It’s about continuous system monitoring to detect signs of suspicious or unauthorized activity and respond before damage is done.
Continuous monitoring
You can deploy intrusion detection systems (IDS), security information, and event management (SIEM) solutions to monitor network traffic and detect potential threats.
Anomalies and events
Look for unexpected changes in how your system is working or how it’s communicating with other systems. These might be caused by someone trying to get in without permission or doing something without the required permissions.
That is the only way to prevent or avoid severe damage as well as determine the possible impact and scope of unwanted activities.
Security analytics
Use advanced analytics and machine learning algorithms to sift through vast volumes of data and highlight unusual patterns that may indicate cyber threats.
Respond (RS). Lowering the incident’s impact
An adequate and well-coordinated response to a detected cybersecurity incident (or event) ensures your company has developed the protocols to contain the threat and mitigate its impact. They should include:
Incident containment
After an incident is detected, the immediate steps to contain it might involve:
- affected systems isolation
- disconnecting compromised devices
- disabling suspicious user accounts.
Communication
The communication plan includes developing channels to inform internal teams, external partners, and customers about the incident.
In general, incident response communication should be swift and transparent. It must maintain trust while addressing security concerns.
Mitigation strategies
Any strategy you implement should minimize damage and prevent similar incidents in the future. They may include:
- applying patches
- reconfiguring firewalls
- improving access controls.
In short, responding effectively to incidents minimizes their impact on business operations and enhances future preparedness.
NIST Cybersecurity Framework 2.0. Source: nist.gov
Recover (RC). Restoring the operational flow
The approach focuses on restoring any capabilities or services impaired by a cybersecurity event(s). The process involves creating plans and actions that help firms bounce back after an attack. In turn, the company may incorporate improvements into its cybersecurity practices.
Recovery planning
Each established recovery protocol prioritizes the restoration of critical systems and operations. Regular testing of such recovery plans through tabletop exercises improves their effectiveness under real-world conditions.
Of course, a robust backup system is indispensable for efficient recovery. Data restoration can become a long and challenging process without well-planned backup procedures. That includes regular and secure snapshots of vital systems. Additionally, geographically dispersed backups reduce the risk of data loss from localized disasters.
Continuous improvement
Conducting post-incident analysis is crucial anytime an incident occurs to identify and eliminate gaps and weaknesses in the company’s cybersecurity posture.
Such extracted insights provide the foundation for:
- defense improvement
- refining incident response strategies
- strengthening overall cybersecurity governance.
This particular view on recovery allows you to protect normal operations flow better and build resilience for potential cybersecurity events.
Govern. Establish your cybersecurity risk management strategy
The thing is about developing and maintaining a firm’s cybersecurity risk management strategy. It begins with assessing specific cybersecurity needs.
At the same time, it focuses on determining the company’s risk tolerance by evaluating threats and consulting internal stakeholders.
Then, organization-wide risk management policies with regulatory and contractual obligations are created. These policies should be embedded in the company culture and regularly updated.
In each cybersecurity practice, you have to communicate efficiently across all levels. This allows you to receive proper feedback and make adjustments.
A crucial aspect of governance is managing supply chain risks. Ensure that all partners and vendors follow your security rules and are involved in fixing problems (response and recovery efforts).
Continuous oversight supports confidence that the firm is always aware of possible security threats and that all plans for dealing with them are up-to-date. It helps to prevent problems before they happen.
Implementing the NIST Cybersecurity Framework (CSF) 2.0 in the organization
The process requires careful planning, collaboration, and ongoing assessment of your company’s cybersecurity readiness. It’s not a one-time task but a continuous effort.
Implementation starts by assessing and comparing current cybersecurity practices to the CSF’s core functions. That will help you identify gaps and prioritize actions based on your risk tolerance and business objectives. Then, it’s time to conduct forthcoming actions.
Tailoring the framework
At this step, customize the framework to your specific organizational requirements and industry. Various organizations have different risk profiles, so the NIST CFS can be adapted to meet unique requirements, even for improving critical infrastructure cybersecurity.
Engaging stakeholders
Collaboration with internal and external stakeholders—vendors, partners, and regulatory bodies—demands a unified approach to cybersecurity.
Monitoring and adapting
Your security framework must evolve as cybersecurity threats do. That means continuously assessing the effectiveness of digital security measures. Along with it, all policies and technology updates should follow.
Integrating the NIST Cybersecurity Framework into daily operations and processes enhances cybersecurity governance and helps to achieve cybersecurity resilience.
Common challenges and best practices
As with any framework, understanding common vulnerabilities and implementing proven practices helps strengthen defenses against upcoming threats.
Challenges
Resource constraints
Smaller firms may struggle to fully allocate the resources necessary to implement the framework. Especially when it comes to continuous monitoring and incident response, which require ongoing attention and specialized expertise.
Supply chain risk management
Identifying and managing supply chain risks can be difficult when dealing with third-party vendors. Especially when they have less robust cybersecurity practices.
Best practices for managing cybersecurity risks
Start small
Companies should begin by focusing on the Identify and Protect functions, gradually expanding their implementation of the framework over time.
Use automation
Leverage automation tools to streamline processes like monitoring, detection, and incident response, reducing the burden on limited cybersecurity teams.
Continuous improvement
Not being a one-time effort, cybersecurity plans require regular updates and tests to address emerging threats and new vulnerabilities.
DID YOU KNOW?
The GitProtect backup and restore system can help you meet the NIST Cybersecurity Framework regarding Protect and Recover requirements. Using GitProtect.io, you can:
– automate all DevOps stack backups
– connect any storage for replication (!)
– utilize Instant Remediation Center service (backup assurance with notifications, audit-ready SLA reporting, and visual stats)
– rely on unlimited retention for compliance.
Store backup copies of [Assignment: organization-defined critical system software and other security-related information] in a separate facility or in a fire rated container that is not collocated with the operational system.
Source: nist.gov, page 126.
Summary
The NIST Cybersecurity Framework (CSF) provides companies with a comprehensive, flexible approach to managing cybersecurity risks.
By following its core functions – Govern, Protect, Detect, Respond, and Recover – businesses can:
- safeguard their critical assets
- align their security efforts with objectives
- build resilience against upcoming and ever-evolving threats.
Implementing the framework enables firms to take control of their cybersecurity risk and protect against potential attacks. In turn, they will maintain and further develop long-term operational stability.
[FREE TRIAL] Ensure compliant DevOps backup and recovery with a 14-day trial 🚀
[CUSTOM DEMO] Let’s talk about how backup & DR software for DevOps can help you mitigate the risks






