Backup Guide For Jira Automation Rules
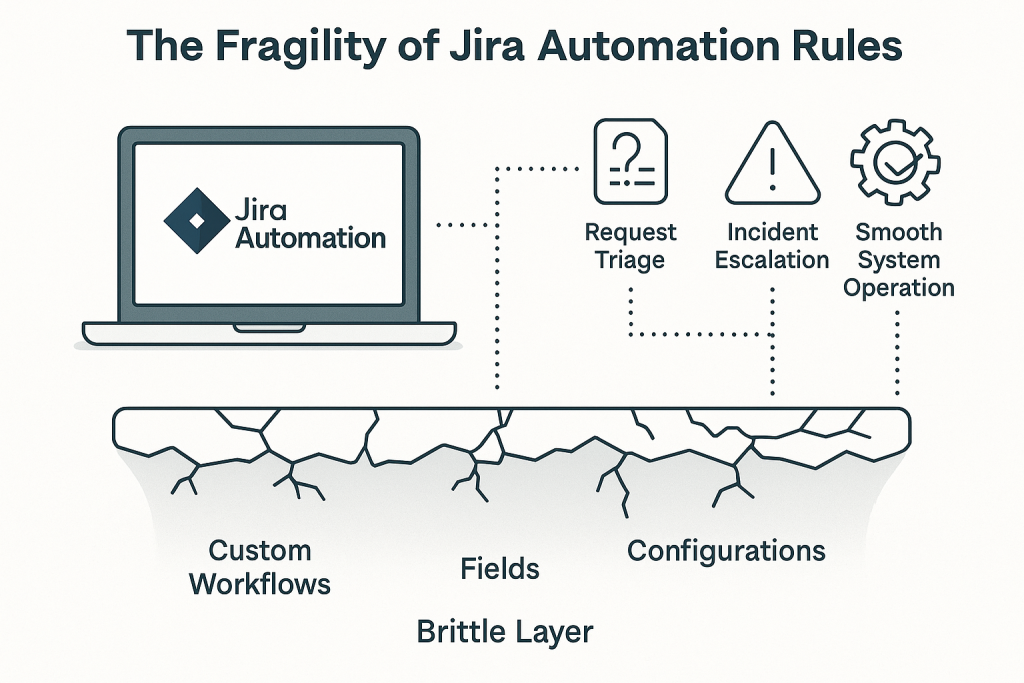
It’s no news that Jira Automation Rules (JAR) sit at the center of how teams choose to streamline work. They triage requests and escalate incidents. At the same time, they keep systems running smoothly without requiring human intervention. For teams managing ITSM, DevOps, and cross-functional service operations, these rules are operational logic with many conveniences.
The problem occurs when they disappear. In that case, the business doesn’t slow down. It just stalls. An additional challenge with Jira Automation Rules is that they’re fragile. Besides, they’re not automatically backed up. They exist in the same brittle layer as custom workflows, fields, and configurations. If so, then a single misclick, API mishap, or migration glitch can wipe out hours – if not weeks – of logic engineering.
Missing rule, missing pipeline. When automation is a blind spot
Let’s imagine an enterprise-scale digital services firm found itself blindsided. The company relied on Jira Service Management and Bitbucket to orchestrate both internal workflows and external support pipelines. Its Jira instance had grown into a complex, tightly interconnected control system.
Hundreds of Jira Automation Rules were used to auto-assign tickets, trigger CI/CD events, and escalate SLA-breaching cases, with zero manual intervention. One Monday morning, however, a global rule vanished. There was no confirmation, audit trail, and thus, no restore option.
And it wasn’t the first time either. Sometime earlier, part of the company’s automation rules had stopped executing silently (degraded rule performance). The team hadn’t expected complete disappearance. The deletion went unnoticed until hours later. Exactly when DevOps escalations stopped propagating, and SLA alerts failed to trigger.
The queue ballooned. Teams went silent while incidents sat unresolved. All because of a single rule, which had taken down a day’s worth of service continuity.
The context. A fragile system with no safety net
The company’s management didn’t need a postmortem to realize the deeper issue. The automation logic, the very rules keeping Jira functional, had no recovery strategy. Their tickets and project data were replicated regularly, but the automation layer was left exposed. This case, however, wasn’t unique.
According to GitProtect’s 2024 threat report, Jira experienced 130+ incidents of various impacts, with at least six documented disruptions in Jira Automation Rules taking place in 2024 (~25 hours of some disruption). And there was nothing theoretical about them. They included:
- a nine-hour outage in September due to missing automation rules
- smart values failing to populate during API triggers
- configuration discrepancies in rule execution logic
- automation triggers failing silently for over an hour.
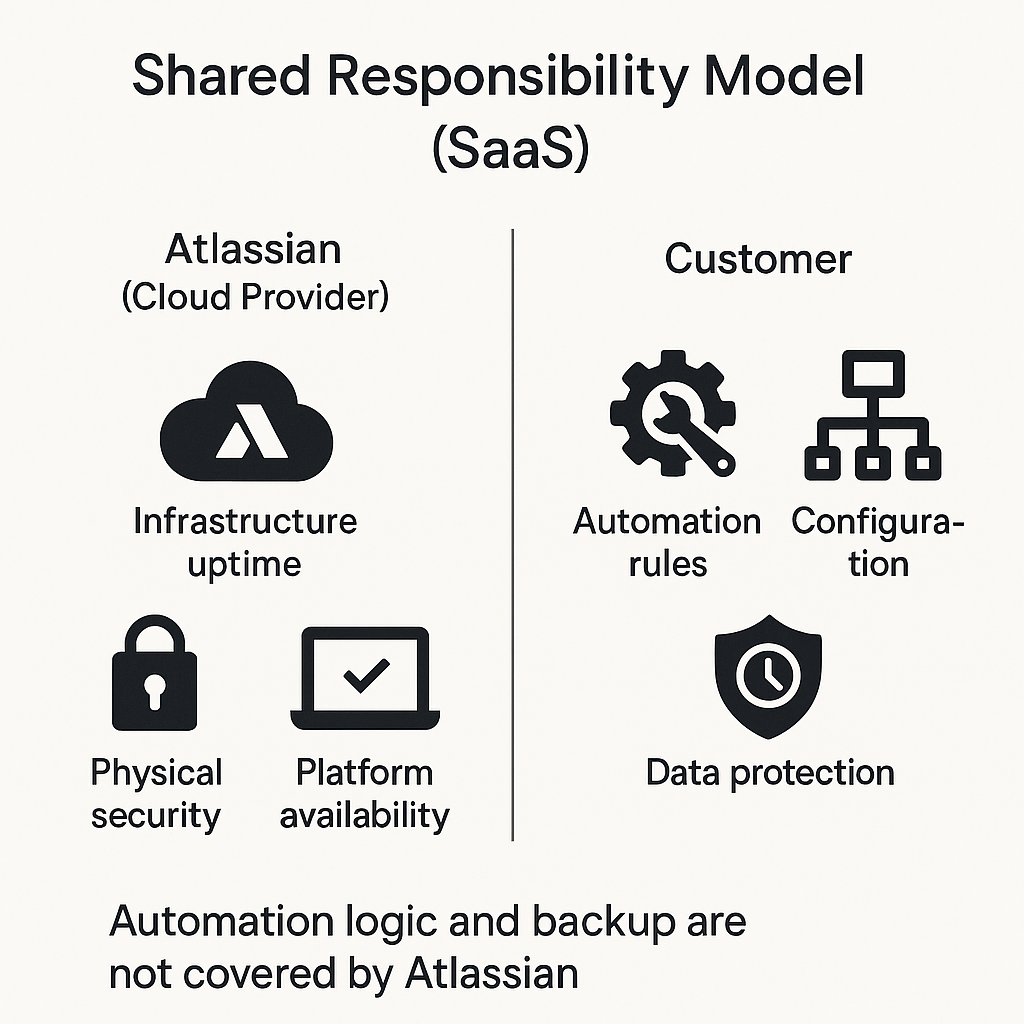
The threads aren’t just operational either. Jira’s automation layer has become a vulnerability surface – from accidental deletions to ransomware propagation via misconfigured webhooks. And what’s crucial, since Atlassian operates on a Shared Responsibility Model, safeguarding this logic is a customer’s duty only.
Unfortunately, many IT experts still absurdly assume that if they are a service client, they don’t have to worry about it.
Early attempts. API scripts, manual exports, and false confidence
Following the disruption, the engineering team attempted to craft its own safety net. They tested scheduled reports through Jira’s REST API. Then they tried to use in-house Python scripts to scrape rule configurations and store them locally. They even assigned a team lead to periodically export rule definitions via the Jira UI. The assumption was that a manual process, however crude, would suffice. Each effort failed (in a different way).
- The scripts missed dependencies between global and project-specific rules.
- Manual exports were outdated the moment new triggers were added.
- During a ransomware simulation, none of the stored data could be reimported in context without heavy rework.
Making it short: the team had files, not backups.
The turning point. Rethinking what “backup” really means
After the deletion crisis, management acted. The CIO ordered a reevaluation of the company’s Jira disaster recovery readiness with special emphasis on automation logic. The aim was to restore any automation rule – global or local – to its exact configuration. That included any moment in time with the ability to test it before going live.
This ruled out manual methods. The team wanted a point-in-time restore, granular recovery, and the ability to validate restored rules in staging before pushing them into production. Any solution without that level of control was considered a liability.
The solution. Automatic backup that matches the stakes
The company’s eyes were on GitProtect backup & Disaster Recovery for Jira. After testing multiple backup platforms and speaking with other Atlassian users, the team implemented GitProtect for their Jira environment. The goal was to protect it from itself.
GitProtect provided what the firm’s DIY efforts couldn’t.
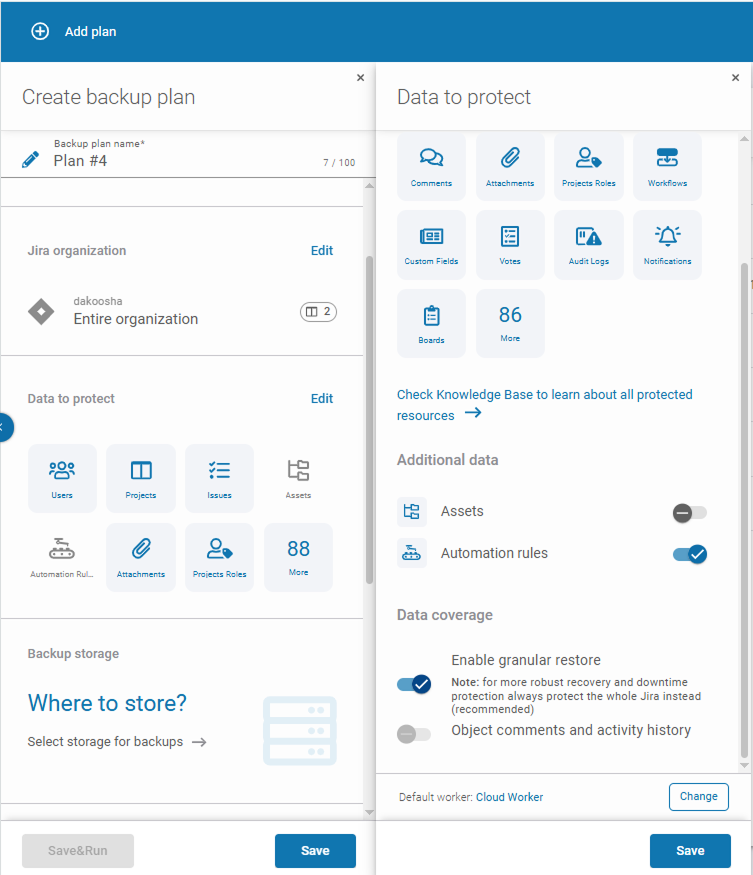
- Scheduled, automated backups of Jira (including Jira Automation Rules), both global and project-specific.
- Retention policies that preserve historical versions without manual cleanups.
- Immutable storage that guarantees ransomware can’t overwrite or encrypt backups.
- Disaster Recovery capabilities, including cross-project restores and sandbox validation.
- Point-in-time restore, allowing recovery of specific rules from a precise moment.
- Metadata intelligence that lets admins selectively restore broken automation without
disrupting active tickets or workflows.
The most important thing is that the solution covers Jira Software, Jira Service Management, and Bitbucket. In turn, it provided the team with a complete ecosystem safety layer without requiring them to jump between tools.
The outcome. Recovery according to plans
Weeks after deployment, the team ran a dry-run simulation. A mid-level rule was intentionally deleted from a high-volume project. Within minutes, GitProtect’s interface allowed the IT to locate a previous version of their Jira instance and restore it in full context without overwriting current data or triggering duplicate events.
More simulations followed:
- a full project restore
- a cross-service recovery
- a rule rollback after a misconfigured edit.
Each time, the recovery was simple and successful. None required script adjustments, and none triggered user confusion. Mondays were no longer feared.

A small example of GitProtect’s capabilities.
Backup and disaster recovery best practices for Jira Automation Rules
Considering the above, it’s necessary to understand that backup is a process, not a simple checkbox. For Jira Automation Rules, the process must reflect production-grade maturity. Primarily, when used for ITSM, DevOps orchestration, and SLA enforcement.
The following checklist shaped the firm’s internal policy and reflects GitProtect’s capabilities.
- Automated backup policies.
- Retention policies aligned with compliance obligations.
- Restore previews in staging before applying changes to live systems.
- Ability to restore rules with full metadata, without overwriting other configurations.
- Immutable backups stored in secure, access-controlled environments.
- Unified protection across Jira Software, Jira Service Management,
and Bitbucket. - Alerts and logging are integrated with SIEM for compliance traceability.
Final thought
Jira itself is a robust platform. But no system, however mature, is immune to the consequences of ungoverned complexity. As the company scales, the automation layer often evolves faster than oversight can keep up. Rules tend to accumulate, dependencies multiply, and what was once clear, traceable workflows become a dense web of interlocking triggers and silent assumptions.
And that is where fragility begins. It’s not from flaws in the software, but from misplaced confidence in the permanence of logic that remains invisible until it falls.
What this company discovered is painfully simple. Automation is infrastructure – not just an app (add-on) or time-saving luxury. It’s the logic that defines how:
- teams communicate
- incidents escalate
- customers get served.
And like all infrastructure, it must be protected, versioned, and restorable. Not only when the lights are on, but especially when everything breaks.
Of course, backups aren’t a tool to admire when things are going correctly. Along with GitProtect, a verified and proven backup and disaster recovery system, backups are the only thing standing between chaos and continuity when nothing works as expected.
For Jira Automation Rules — just like for source code, access controls, or configuration files — recoverability is the last line of defense. All the more so when any other assumption fails. And failing to back up automation is not just a risk, but a design flaw.
[FREE TRIAL] Ensure compliant DevOps backup and recovery of critical Jira data with a 14-day trial 🚀
[CUSTOM DEMO] Let’s talk about how backup & DR software for Jira can help you mitigate the risks