
The State of GitHub Threat Landscape for GitHub Admins – 2024 In Review
In 2024 threat actors were trying to abuse GitHub even more severely than before. There were detected thousands of “ghost accounts” spreading malware. Hackers were also trying to succeed in their malware campaigns using not only repositories but also comments.
Moreover, multiple organizations that store their source code on GitHub have experienced data leakage and data breaches. Among those companies are The New York Times, Mercedes Benz, Ultralitics, etc.
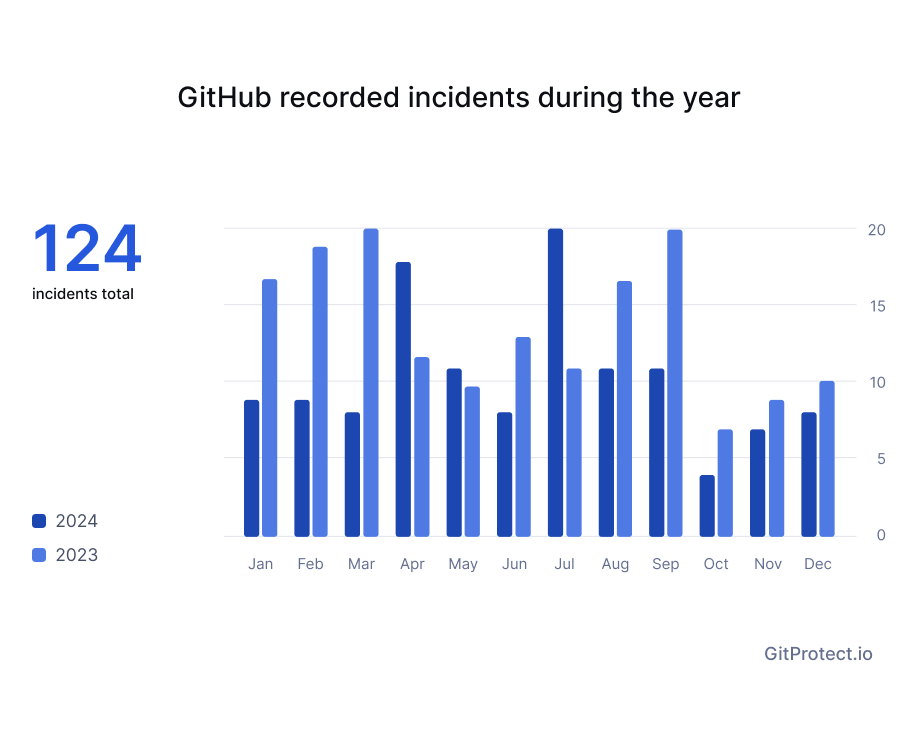
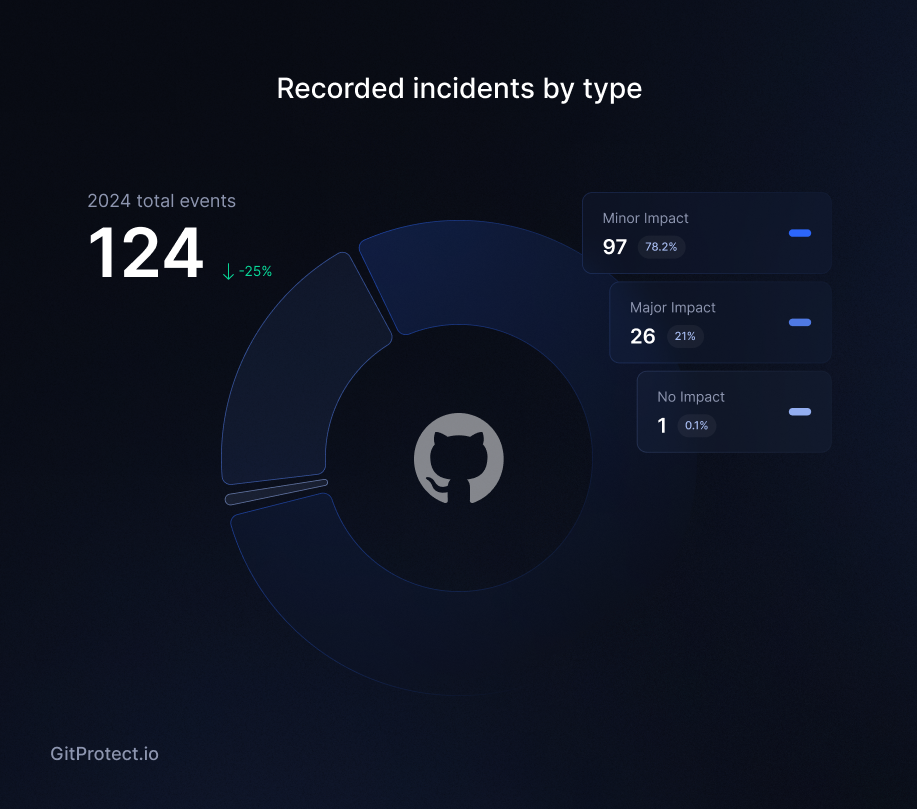
However, when it comes to the incidents that GitHub faced in 2024, its number reduced by about 25% with the total number of reported issues on GitHub Status of 124. Last year, the service provider experienced 165 incidents of different severity.
DECEMBER
GitHub Status info: 8 issues
🚨 Incidents that had a major impact – 2 incidents
⌛Total time of partial disruption – 59 minutes
⚠️ Incidents that had a minor impact – 6 incidents
⌛ Total time of degraded performance – 15 hours 7 minutes
In December, GitHub experienced 2 major incidents, causing around an hour of partial disruption. Additionally, there were 6 minor incidents that resulted in over 15 hours of degraded performance, primarily affecting GitHub Enterprise Cloud in the EU, Pull Requests, and Actions services.
3M+ fake “star” GitHub projects used to spread malware
GitHub is facing an issue with inauthentic “stars” used to inflate the popularity of scam and malware-distributing repositories, making them appear trustworthy to users.
A study by researchers from Socket, Carnegie Mellon University, and North Carolina State University State identified 4.5M+ suspected fake stars across 22,915 repositories, with many stemming from coordinated bot-like activity.
Using the tool StarScout, the team analyzed GitHub metadata and flagged repositories with suspicious patterns, reducing the list to 3.1 million fake stars involving 15,835 repositories. Approximately 91% of flagged repositories were deleted by October 2024, but fake star activity continues to rise, with significant spikes in 2024.
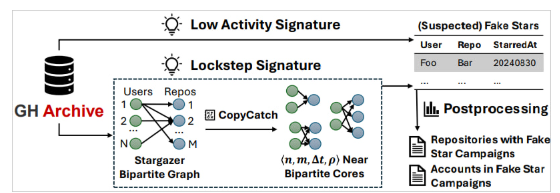
Source: Bleeping Computer – Arxiv.org
These fraudulent practices erode trust in GitHub and its projects, emphasizing the need for users to evaluate repositories carefully beyond their star count. GitHub is actively removing flagged repositories and accounts but remains challenged by ongoing malicious campaigns.
Software developers are targeted by the North Korean hackers
The North Korean “Contagious Interview” hacker campaign targets aimed at developers with fake job postings to distribute malware like BeaverTail and OtterCookie.
OtterCookie infects systems via loaders in Node.js projects, npm packages, or applications downloaded from any of GitHub or Bitbucket, later using Socket.IO WebSocket for command-and-control communications.
The malware’s functionalities include stealing crypto wallet keys, sensitive clipboard data, and performing reconnaissance with shell commands. This campaign highlights the attackers’ evolving techniques and emphasizes the need for developers to verify job-related information and scrutinize code from untrusted sources.
NjRat 2.3D Pro Edition might be actively exploited on GitHub
The discovery of NjRat 2.3D Professional Edition on GitHub rases significant concerns because of its advanced capabilities and ease of access to cybercriminals.
NjRat, a Remote Access Trojan active since 2012, enables attackers to steal credentials, log keystrokes, access webcams, and deploy additional malware. The latest version, which is publicly available on GitHub, introduces enhanced features for remote control and data theft. It even more increases its threat level. Open access on such platforms lowers barriers for threat actors, potentially leading to a surge in cyberattacks.
Thus, to eliminate the threat organizations must adopt robust cybersecurity measures, including endpoint protection, employee awareness, regular updates, and network monitoring, while platforms like GitHub need to improve their mechanisms to prevent hosting malicious software.
Major GitHub outage leaves thousands of developers locked out of their projects
On December 17th, more than 1,3K users in UK and 2K in the United States reported issues in GitHub services work, according to Downdetector.
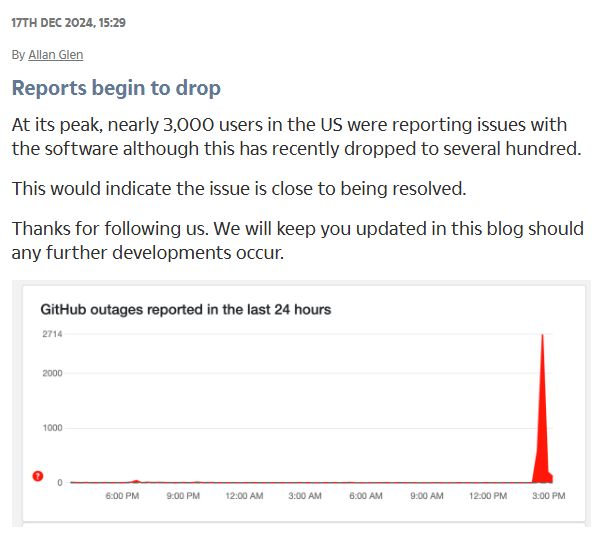
Source: The Sun
As GitHub later explained in its Status, “the increased error rate caused a broad impact across our services, such as the inability to log in, view a repository, open a pull request, and comment on issues”.
The reason of why “many users experienced intermittent errors and timeouts” when were trying to access GitHub took place due to planned maintenance that caused the live updates service to fail and overloaded web servers.
Hacker stole over 390K WordPress credentials through their malicious GitHub repo hosting PoC exploits
A malicious GitHub repository, now removed, enabled the exfiltration of 390K+ credentials, primarily targeting WordPress accounts, through a fake tool called “Yet Another WordPress Poster” (yawpp).
The repository, associated with a threat actor dubbed MUT-1244, also deployed malware via a rogue npm dependency and phishing emails. Victims included pentesters, security researchers, and malicious actors who inadvertently exposed sensitive data such as SSH private keys and AWS credentials. MUT-1244’s tactics include creating trojanized GitHub repositories hosting fake PoC exploit code and employing phishing emails to deliver payloads like cryptocurrency miners and data theft tools.
Such campaigns often exploit vulnerability disclosures, using fake GitHub profiles with AI-generated images to lure victims. The second-stage malware is distributed through multiple methods, including backdoored files, malicious PDFs, Python droppers, and npm packages. The attacks highlight the growing risks of compromised PoC repositories and phishing targeting the cybersecurity community.
The Hacker News / SC Media / HACKread
A compromised Ultralytics AI library – urgent update needed
There were found 2 compromised versions of the Python AI library Ultralytics (8.3.41 and 8.3.42) to contain a cryptocurrency miner, exploiting the build environment through a GitHub Actions script injection vulnerability.
The attack caused discrepancies between the source code on PyPI and the GitHub repository, with malicious pull requests originating from an account linked to the OpenIM SDK. The miner, identified as XMRig, triggered high CPU usage on macOS and Linux systems, but experts warn the attack could have been more severe if backdoors or RATs were planted.
“It seems that the malicious payload served was simply an XMRig miner, and that the malicious functionality was aimed at cryptocurrency mining..[]… But it is not hard to imagine what the potential impact and the damage could be if threat actors decided to plant more aggressive malware like backdoors or remote access trojans (RATs),” says a ReversingLabs engineer.
The compromised versions have been removed from PyPI, and a secure update has been released to fix the issue, with users strongly advised to upgrade immediately.
NOVEMBER
GitHub Status info: 7 incidents
🚨 Incidents that had a major impact – 1 incident
⌛ Total time of partial disruption – 1 hour 7 minutes
⚠️ Incidents that had a minor impact – 6 incidents
⌛ Total time of degraded performance – 12 hours 10 minutes
In November 2024, GitHub users might notice 7 incidents that the service provider experienced.
There was a major incident on November 19 lasted over an hour, delaying notifications due to a database issue and 6 minor incidents, totaling 12 hours and 10 minutes of degraded performance, included issues with Codespaces, GitHub Search, Copilot Chat, and merge queues.
Multiple GitHub projects are targeted with malicious commits
A number of GitHub projects, including EXO Labs, were targeted by malicious commits attempting to inject backdoors into repositories. One of such pull request disguised as an innocent code change used Unicode obfuscation to introduce a script designed to fetch and execute remote code, though the associated URL contained no payload.
The roots of the attack goes to accounts impersonating Texas-based security researcher and ethical hacker Mike Bell, who denied involvement, claiming it was a smear campaign.
Other open-source projects, like “yt-dlp,” faced similar attacks, with at least 18 malicious pull requests that wereidentified.
After this threat was identified, many impersonating accounts and associated commits were removed by GitHub. Tools like Presubmit’s AI Reviewer successfully flagged these threats during testing, emphasizing the importance of automated and human code reviews. This incident proves ongoing risks in open-source supply chains and the need for vigilant monitoring of all the contributions.
Hackers can execute malicious commands due to GitHub CLI RCE Vulnerability
A critical vulnerability in GitHub CLI, tracked as CVE-2024-32002 might allow an attacker to execute arbitrary code on a user’s system via remote code execution when interacting with malicious Codespace environments. The flaw, which was found in versions prior to 2.62.0, exploits how SSH connection details, including crafted usernames, are handled in commands like gh codespace ssh. Attackers can inject malicious SSH arguments through dev containers, potentially compromising sensitive data, installing malware, or enabling further network intrusion.
To mitigate the potential threats, users are urged to update to version 2.62.0 or later, use trusted dev containers, and avoid connecting to untrusted Codespaces to mitigate this risk.
GitHub developers are targeted by GoIssue
The GitLoker hacking group that has been hijacking GitHub repos for a while, introduced a new phishing tool, GoIssue, the aim of which is to extract GitHub user email addresses and automate phishing campaigns targeting developers and their organizations.
This tool enables large-scale credential theft, supply chain attacks, and source code breaches by using features like customizable email templates, email scraping, and token management.
Cybersecurity experts warn that Goissue’s automation and scalability might significantly increase the threat level, exploiting trust within the developer community to hijack repositories and compromise networks.
The Hacker News / Dark Reading / Security Week
OCTOBER
GitHub Status info: 4 incidents
🚨 Incidents that had a major impact – 1 incident
⌛ Total time of partial disruption – 7 hours 18 minutes
⚠️ Incidents that had a minor impact – 3 incidents
⌛ Total time of degraded performance – 11 hours 10 minutes
GitHub users might experience 4 incidents of different importance in October. The most notable of them lasted for over 7 hours and involved DNS infrastructure failures after a database migration, affecting such services as Copilot, Actions, customer migrations, support, and code search.
Cisco’s DevHub’s environment is hacked
Cisco confirmed that some files were stolen after a hacker, IntelBroker, claimed a breach involving GitHub and SOnarQube project, source code, credentials, confidential documents, certificates, API tokens, Jira tickets, encryption keys, AWS private buckets, and other data.
Though, Cisco’s investigation found no breach of its systems but revealed that the hacker exploited a public-facing DevHub environment used for customer resources. The company determined that only a small number of files were exposed, with no evidence so far of sensitive PII or financial data being included.
Public access to the affected website has since been disabled as the investigation continues. IntelBroker is known for targeting major organizations, though victims, including Deloitte, Microsoft, AT&T, Verizon, etc. often report limited impact from such incidents.
In October GitHub released security updates for Enterprise Server (GHES) to address multiple vulnerabilities, including a critical issue, tracked as CVE-2024-9487with th CVSS score of 9.5 out of the maximum of 10.
The vulnerability could allow attackers to bypass SAML SSO authentication and gain unauthorized access. This flaw was a regression from a previous patch for another severe vulnerability, CVE-2024-4985 with a severity of 10.0
Two additional issues were also fixed: an information disclosure vulnerability, tracked as CVE-2024-9539 with a CVSS score of 5.7 related to SVG metadata and sensitive data exposure in HTML forms within the management console. These vulnerabilities have been resolved in GHES versions 3.14.2, 3.13.5, 3.12.10, and 3.11.16. GitHub strongly advises organizations to update to the latest versions to mitigate security risks.
GitHub links are exploited in a new malware campaign targeted at the finance and insurance industries
According to the cybersecurity firm, Confense, cybercriminals created a new scheme to target finance and insurance companies. In this cyberattack campaign, they sent victims tax-themed phishing emails with trusted GitHub links to deliver the Remcos Remote Access Trojan (RAT), bypassing security measures. Attackers exploit legitimate repositories like UsTaxes and HMRC, uploading malicious files as comments and deleting them while keeping the malware link active. All of that makes the detection challenging.
“In this campaign, legitimate repositories such as the open-source tax filing software, UsTaxes, HMRC, and InlandRevenue were used instead of unknown, low-star repositories. Using trusted repositories to deliver malware is relatively new compared to threat actors creating their own malicious GitHub repositories. These malicious GitHub links can be associated with any repository that allows comments,” states Cofenser in its research.
This tactic, effective due to GitHub’s reputation as a trusted domain, represents a shift from traditional methods where hackers relied on their own repositories.
It only proves the fact that as the attacks grow more sophisticated, meaning that businesses in targeted industries must strengthen cybersecurity measures to safeguard against evolving threats.
The Hacker News / Entrepreneur / Dark Reading
SEPTEMBER
GitHub Status info: 11 incidents
🚨 Incidents that had a major impact – 3 incidents
⌛ Total time of partial disruption – 2 hours 36 minutes
⚠️ Incidents that had a minor impact – 7 incidents
⌛ Total time of degraded performance – 230 hours 30 minutes
⚙️ Operational issues – 1 incident
⌛ Total time of disruption – 8 minutes
In September 2024, GitHub experienced 11 incidents, which included 3 major disruptions totaling over 2 hours and 7 minor incidents causing 230+ hours of degraded performance.
The issues included Codespaces interruptions in Central India and network connectivity failures affecting Codespaces, degraded Actions and Pages services, Copilot degradation, and widespread delays in Issue, Pull Requests, and Webhook processing.
Attackers abuse GitHub repos to distribute the password-stealing malware
The threat actors built their phishing campaign by exploiting GitHub’s “Issues” feature. Thus, they managed to distribute the Lumma Stealer malware by tricking users into visiting a fake “GitHub Scanner” website.
How does it work? Threat actors open issues on open-source repositories, falsely claiming security vulnerabilities and directing users to counterfeit sites. The campaign’s credibility is enhanced by legitimate GitHub email notifications sent to repository contributors, making the alerts appear authentic. Upon visiting the fraudulent site, users encounter a fake CAPTCHA that covertly executes malicious JavaScript, which downloads and installs the Lumma Stealer malware. This malware steals credentials, authentication cookies, browsing history, cryptocurrency wallets, and sensitive files.
The attackers aim to compromise developers’ credentials, potentially modifying source code to execute supply chain attacks.
Thus, to mitigate the risks, users are advised to avoid interacting with suspicious links and report such issues to GitHub immediately.
Around 3K of GitHub accounts might be spreading a malware
Experts from Check Point Research found out that cybercriminals are leveraging ghost accounts on GitHub to distribute malware through a sophisticated distribution-as-a-service (DaaS) network called the Stargazers Ghost Network.
These accounts show normal activities to avoid detection while distributing malicious links via platforms like Discord, targeting users interested in boosting social media followers.
The network has hosted over 2,200 malicious repositories, spreading malware like Atlantida Stealer, which steals credentials, cryptocurrency wallets, and personal information, infecting over 1,3oo victims in just 4 days during a campaign. The scheme also generates income through dark web services like selling stars, followers, and trusted accounts, earning approximately $100,000.
GitHub has taken steps to disable these accounts, but researchers believe this is only the beginning, as similar operations likely span other platforms like YouTube, Instagram, and Facebook. Future campaigns may use AI-driven accounts to generate targeted, personalized phishing material, making malware distribution harder to detect. Check Point Research warns this marks a new era in cyber threats requiring heightened vigilance.
Security Intelligence / The Register
AUGUST
GitHub Status info: 11 incidents
🚨 Incidents that had a major impact – 1 incident
⌛ Total time of partial disruption – 36 minutes
⚠️ Incidents that had a minor impact – 10 incidents
⌛ Total time of degraded performance – 12 hours 2 minutes
In August 2024, GitHub experienced 11 incidents, including 1 major disruption where all GitHub services were inaccessible for more than 30 minutes. Between 23:02 UTC and 23:38 UTC on August 14th, GitHub users all over the world couldn’t access the service and were shown a picture of an angry pink unicorn while the service provider was downtime.
Source: Times Now World
According to GitHub Status, the incident happened “due to a configuration change that impacted traffic routing within our database infrastructure, resulting in critical services unexpectedly losing database connectivity. There was no data loss or corruption during this incident.”
The remaining 10 minor incidents that GitHub saw in August caused 12+ hours of degraded performance in Actions, Copilot outages that affected 25% of users, and elevated API error rates.
Hackers use GitHub comments to push malware
Another case of Lumma Stealer was reported by Bleeping Computer in late August. This time it was found that threat actors were abusing GitHub by posting fixes in project comments, distributing a password stealing malware, which steals credentials, cookies, cryptocurrency wallets, and sensitive files.
The bad actors have posted thousands of malicious comments, often containing links to password-protected archives with executables across GitHub projects. All of that is to trick users into downloading and running the malware. Over 29K of such comments were posted in just 3 days.
Though, GitHub immediately searched and deleted them, some of the users were fallen victim. The service provider advises the affected users to reset their passwords and migrate cryptocurrencies to secure wallets.
GitHub security flaw ArtiPACKED can allow a takeover of GitHub repos
Attackers can exploit ArtiPACKED, a detected attack vector in GitHub Actions artifacts, to take over GitHub repositories and also access the organization’s cloud environments.
The given vulnerability exploits misconfigurations and security flaws to expose sensitive tokens and compromise repositories and cloud environments. With its help threat actors can exploit leaked GitHub tokens, such as GITHUB_TOKEN and ACTIONS_RUNTIME_TOKEN, to gain unauthorized access, inject malicious code, and execute remote code. These artifacts, which store workflow data like builds and logs, are publicly accessible in open-source projects, making them a high-risk target for attackers. The issue is exacerbated by race conditions and improperly secured workflows, enabling attackers to replace artifacts or steal tokens during active CI/CD pipeline runs.
GitHub has classified the issue as informational, urging users to secure their artifacts and reevaluate usage, especially following the deprecation of Artifacts V3.
The Hacker News / Bleeping Computer / SC Media
Fake WinRar website delivers ransomware via GitHub
The cyber security researchers at Sonic Wall found out that threat actors can exploit fake websites, like a deceptive WinRar lookalike (win-rar[.]co), to distribute malware and steal personal data.
This typosquatting site hosts a malicious shell script, zx.ps1, which downloads additional malware components from a GitHub repository named “encrypthub.” The repository contains tools for ransomware, crypto mining, information theft, and shellcode injection, among other malicious capabilities, with components sending system data to a Telegram account.
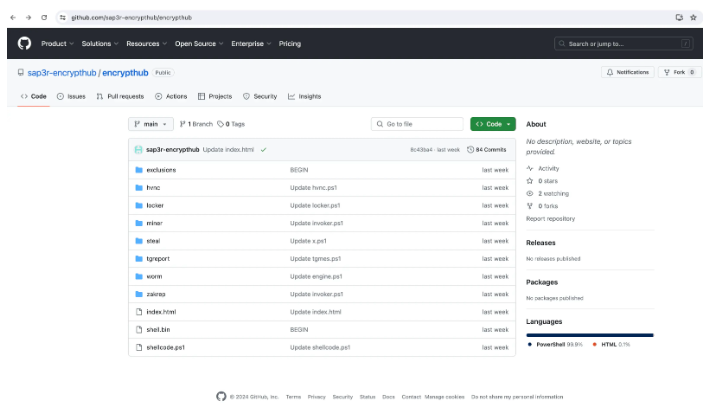
Source: Cybersecurity news ( Main malware project page hosted on GitHub)
While there haven’t been proven full-scale attacks using all components, its infrastructure reveals the potential for complex, multi-stage intrusions. Users are urged to verify software sources and exercise caution when downloading programs to mitigate such threats.
JULY
GitHub Status info: 20 incidents
🚨 Incidents that had a major impact – 3 incidents
⌛ Total time of partial disruption – 63 hours 58 minutes
⚠️ Incidents that had a minor impact – 17 incidents
⌛ Total time of degraded performance –
In July 2024, GitHub experienced 20 incidents, including 3 major disruptions totaling 63 hours and 58 minutes of partial service outages. The most significant major incidents included a 19-hour Copilot outage, a Copilot Chat disruption, and delayed webhook deliveries. Among the 17 minor incidents (totaling over 50 hours of degraded performance), notable issues included regional Codespaces and Actions delays, Copilot Chat timeouts, and GitHub documentation outages. A prolonged 29-hour degradation affected external identity linking, highlighting the impact of infrastructure and provider-related issues. These disruptions underscore the challenges of maintaining seamless service for a globally distributed platform.
Python’s core repos exposed by GitHub token leak
Cybersecurity researchers at JFrog detected a leaked GitHub token in a public Docker container on Docker Hub that could have granted elevated access to critical Python repositories, including PyPI and the Python Software Foundation.
If exploited, this token could have enabled a large-scale supply chain attack by injecting malicious code into Python packages or even the Python language itself. The token, tied to PyPI Admin Ee Durbin, was immediately revoked after responsible disclosure on June 28, 2024, with no evidence of exploitation in the wild.
The leak occurred due to a developer’s local misconfiguration while bypassing GitHub API rate limits, unintentionally leaving the token in the code.
Separately, Checkmarx identified malicious PyPI packages linked to a Telegram bot that exfiltrates sensitive data, showing the persistent risks of supply chain and information theft attacks.
JUNE
GitHub Status info: 8 issues
🚨 Incidents that had a major impact – 2 incidents
⌛ Total time of partial disruption – 3 hours 20 minutes
⚠️ Incidents that had a minor impact – 6 incidents
⌛ Total time of degraded performance – 26 hours 34 min
In June 2024, GitHub reported in its Status 8 incidents, including 2 major disruptions lasting a total of 3 hours and 20 minutes. These involved a migration service outage caused by invalid credentials and a degraded Issues service that hid project events on timelines.
Other 6 minor incidents, totaling 26 hours and 34 minutes, included delays in organization membership updates, regional Codespaces issues, and a prolonged Copilot Pull Request Summaries outage. Other minor disruptions affected migrations, Actions, and the Maven package registry.
A 270GB New York Times source code leaked
According to the message of the 4chan user, 270GB of internal New York Times data, including alleged source code for Wordle, internal communications, and sensitive authentication details from 5K GitHub repositories.
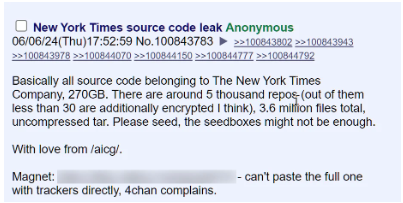
Source: Bleeping Computer
According to the readme file in the archive, the attacker managed to exploit the exposed GitHub token to access the New York Times’ GitHub repositories and steal the data.
The New York Times confirmed a January 2024 incident where credentials to a third-party code platform were inadvertently exposed but stated no unauthorized access to their systems or operational impacts occurred. They emphasized that appropriate measures were taken at the time and that their security includes ongoing monitoring for anomalies.
“The underlying event related to the recent online posting of Times information occurred in January 2024, when a credential to a cloud-based third-party code platform was inadvertently made available,” says Charlie Stadtlander, New York Times managing director for external communications, newsroom, and opinion. “The issue was quickly identified, and we took appropriate measures in response at the time. There is no indication of unauthorized access to Times-owned systems nor impact to our operations related to this event. Our security measures include continuous monitoring for anomalous activity.” – The New York Times
Information Week / Bleeping Computer
GitHub, npm, and jsDelivr code repos compromised with trojanized jQuery packages
Threat actors have been distributing trojanized versions of jQuery through npm, GitHub, and jsDelivr in a complex and persistent supply chain attack targeting website form data. The attack involved 68 manually crafted packages published over nearly a month, with malicious code hidden in the seldom-used “end” function of jQuery, which is called by the popular “fadeTo” function. These trojanized packages exfiltrate data to a remote URL and are hosted on a GitHub repository linked to the account “indexsc,” with additional scripts using jsDelivr to appear legitimate and evade firewalls.
This attack highlights a growing sophistication in supply chain threats, with tailored manual efforts replacing automated tactics to exploit widely trusted platforms.
GitHub repositories wiped in Gitlocker ransomware attacks
In their attacks, Gitlocker, a threat actor, targets GitHub repositories and wipes their content to ask for a ransom.
In their malicious schemes, a threat actor steals the victim’s GitHub data, creates a backup and deletes the user’s data. Then, they rename the repo, add a README.me file and reach out to the victim on Telegram to demand a ransom.
“I hope this message finds you well. This is an urgent notice to inform you that your data has been compromised, and we have secured a backup,” the ransom message may state.
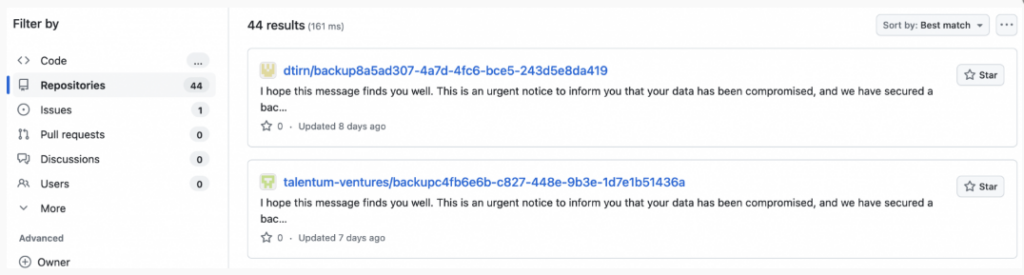
Source: Bleeping Computer
According to Bleeping Computer, dozens of GitHub repositories were compromised. GitHub advances its users to follow security best practices, including rotating their passwords, adding new SSH keys, modifying team members, having a backup, etc.
MAY
GitHub Status info: 11 issues
⚠️ Incidents that had a minor impact – 11 incidents
⌛ Total time of degraded performance – 41 hours 48 minutes
GitHub experienced 11 incidents in May 2024. The total time of degraded performance compounded over 40 hours. Issues ranged from service disruptions affecting Copilot, Codespaces, and Actions to prolonged outages rendering Jupyter Notebooks and creating VMs in Azure.
Critical GHES vulnerability can allow an attacker to bypass authentication
GitHub patched a high-severity vulnerability, tracked as CVE-2024-4985 with the highest possible CVSS score of 10, which might allow a threat actor to bypass the authentication protection. The vulnerability was detected in GitHub Enterprise Server versions prior to 3.13.0.
“On instances that use SAML single sign-on (SSO) authentication with the optional encrypted assertions feature, an attacker could forge a SAML response to provision and/or gain access to a user with administrator privileges,” GitHub communicated in its advisory.
To mitigate the risks, GitHub recommends the organizations that use the affected versions update their instances to the latest version of GHES.
The Hacker News / The Register
GitHub data breach affects fintech company
Iress, a financial services software firm, confirmed in May that there was an unauthorized access to its GitHub user space that resulted in stolen credentials being used to access its OneVue production environment, which contains client data.
While initially stating no client data was compromised, the firm now acknowledges the potential data exposure and is investigating the extent and nature of the breach.
“Investigations have substantially progressed across Iress’ other business lines, and at this time, we have found no evidence that the remainder of Iress’ production environment, software or client data has otherwise been compromised,” the fintech company stated.
Iress has stressed that the issue is isolated to the OneVue business and that no evidence suggests other parts of its production environment or client software were affected. The company has implemented stronger security protocols and emphasized that there is no anticipated disruption to its operations or client services.
Over $300M was stolen from the crypto exchange DMM
North Korean-linked hackers stole 4,502.9 Bitcoin (at the time of the hack it completed around $305M!) from the Japanese crypto exchange DMM, leveraging a sophisticated social engineering attack.
In the mutual investigation of the FBI and NPA of Japan, they found out that the TraderTraitor group impersonated a recruiter on LinkedIn, targeting an employee at Ginco, a crypto wallet company. The hacker tricked the employee into running malicious code disguised as a pre-employment test, compromising their GitHub account and gaining access to sensitive systems.
In May, the group exploited this access to manipulate a legitimate transaction request, transferring 4,502.9 Bitcoin to wallets they controlled. The FBI and its international partners continue efforts to expose and counter North Korea’s cyber operations to fund its regime.
APRIL
GitHub Status info: 18 issues
🚨 Incidents that had a major impact – 5 incidents
⌛ Total time of partial disruption – 77 hours 59 minutes
⚠️ Incidents that had a minor impact – 13 incidents
⌛ Total time of degraded performance – 132 hours 23 minutes
In April 2024, GitHub reported 18 issues, including 5 major incidents totaling around 78 hours of partial disruptions, and 13 minor incidents with over 132 hours of degraded performance.
The incidents included delays in pull request operations, degraded Codespaces creation, and intermittent failures in GitHub Actions and NPM package downloads.
Acuity’s GitHub repos were breached leaking non-sensitive govt data
A tech consulting firm and a federal contractor affiliated with the US government agencies, Acuity, confirmed a breach of its GitHub repositories, involving the theft of outdated and non-sensitive data.
The breach was allegedly carried out by threat actors, including IntelBroker, who exploited a vulnerability in Acuity’s Tekton CI/CD server to steal credentials and access private repositories.
“After conducting our own analysis and following a third-party cybersecurity expert investigation, Acuity has seen no evidence of impact on any of our clients’ sensitive data. In addition to cooperating with law enforcement, Acuity takes the security of its customers’ data seriously and is implementing appropriate measures to secure its operations further.”
Source: Bleeping Computer – Acuity’s official statement
While Acuity stated that no sensitive client data was impacted, IntelBroker has leaked records purportedly containing information related to State Department, Justice Department, DHS, and FBI employees. Moreover, the hacker claims to have stolen classified Five Eyes intelligence documents.
The breach, part of a broader campaign targeting multiple U.S. agencies since December, remains under investigation, with Acuity implementing additional security measures and cooperating with law enforcement.
MARCH
GitHub Status info: 8 issues
🚨 Incidents that had a major impact – 2 incidents
⌛ Total time of partial disruption – 2 hours 45 minutes
⚠️ Incidents that had a minor impact – 6 incidents
⌛ Total time of degraded performance – 10 hours 39 minutes
In its Status for March, GitHub experienced 8 issues, including 2 major incidents with over 2 hours of partial disruptions, primarily caused by authentication service degradation and permissions regression.
Also, there were 6 minor incidents totaling 10+ of degraded performance, affecting services like Pull Requests, Actions, and Copilot, with delays and elevated error rates peaking at 45% for some features.
The software documentation platform is breached
Mintlify, a software documentation platform that assists developers in creating their documentation via accessing their customers’ GitHub repositories, including AI, database, and fintech companies, experienced a security breach that exposed the GitHub tokens of 91 customers, potentially compromising private repositories.
The vulnerability, attributed to a flaw in its system, allowed attackers to gain unauthorized access using admin tokens, though there is no evidence of widespread access to customer repositories. Mintlify has revoked all GitHub token access, patched the vulnerability, implemented enhanced security measures, and advised users to change passwords, enable two-factor authentication, and review API key permissions.
The company continues to work with GitHub, customers, and third-party cybersecurity vendors to investigate and prevent future incidents.
“The users have been notified, and we’re working with GitHub to identify whether the tokens were used to access private repositories,” stated in the company’s advisory.
FEBRUARY
GitHub Status info: 9 issues
🚨 Incidents that had a major impact – 2 incidents
⌛ Total time of partial disruption – 2 hours 2 minutes
⚠️ Incidents that had a minor impact – 7 incidents
⌛ Total time of degraded performance – 12 hours 18 minutes
In February, GitHub faced 9 issues, including 2 major incidents with about 2 hours of partial disruptions, primarily impacting GitHub Packages, Webhooks, and Actions.
What’s more, there were 7 minor incidents totaling around 12 hours of degraded performance, affecting services like Copilot, Git Operations, and dynamic content loading, with delays and intermittent errors reported across various functionalities.
JANUARY
GitHub Status info: 9 issues
🚨 Incidents that had a major impact – 4 incidents
⌛ Total time of partial disruption – 7 hours 7 minutes
⚠️ Incidents that had a minor impact – 5 incidents
⌛ Total time of degraded performance – 99 hours 36 minutes
In its Status for January 2024, GitHub reported 9 incidents, including 4 major ones causing around 7 hours of partial disruption, impacting services like Codespaces, live updates, and backend latency.
Another 5 issues were minor incidents that resulted in over 99 hours of degraded performance, with issues like delayed audit logs, avatar image failures, and port forwarding problems in Codespaces. Despite these challenges, the disruptions were mitigated through routing adjustments and system updates.
A leaked GitHub token triggers Mercedes Source Code exposure
Due to a mishandled GitHub token, Mercedes-Benz source code was exposed to the public. A Mercedes-Benz employee leaked a GitHub token in their personal repository, granting unrestricted access to all source code on the company’s GitHub Enterprise server.
The breach, which occurred on September 29, 2023, was discovered only on January 11, 2024, with the token being revoked two weeks later after RedHunt Labs alerted Mercedes. During the exposure, attackers could have accessed critical information such as API keys, design documents, database credentials, and other sensitive data, potentially causing financial, legal, and reputational damage.
“ We can confirm that source code containing an internal access token was published on a public GitHub repository by human error. This token gave access to a certain number of repositories, but not to the entire source code hosted at the Internal GitHub Enterprise Server. We have revoked the respective token and removed the public repository immediately. Customer data was not affected as our current analysis shows. We will continue to analyse this case according to our normal processes.” – Mercedes-Benz
This incident underscores the severe risks associated with mishandled access tokens and highlights the need for stringent security protocols.
Bleeping Computer / Security Week
High-severity vulnerability cases GitHub to rotate its keys
After patching a critical vulnerability tracked as CVE-2024-0200 with a CVSS score of 7.2 out of 10, GitHub rotates its keys.
A security flaw that GitHub in December 2023 allowed attackers with organization owner roles to access credentials within production containers via environment variables. The issue was reported through GitHub’s Bug Bounty Program and promptly fixed, with credentials being rotated as a precaution.
GitHub confirmed no evidence of prior exploitation, attributing this confidence to the issue’s uniqueness and internal telemetry.
However, the service provider reported that the customers using specific keys, such as GitHub Actions or Dependabot encryption keys, must import new public keys. Moreover, regular updates to public keys from the API are recommended for seamless future key changes.
GitHub also addressed another vulnerability tracked as CVE-2024-0507, allowing privilege escalation through a Management Console editor role.
These incidents highlight GitHub’s proactive approach to securing its platform, following previous key rotation and credential revocation cases earlier in the year.
Takeaway
There were numerous incidents reported of how attackers abuse GitHub in their malicious schemes. Among the top malware that they were trying to spread using GitHub, were BeaverTail, GoIssue, NjRat, Lumma Stealer, etc. However, GitHub was successful in its tries to stop malware distribution by deleting malicious accounts, repositories, and comments.
In 2024 GitHub experienced 124 incidents of different severity, which included partial disruptions, degraded service, and even an outage during which GitHub users couldn’t access the service for over 30 minutes. Of other incidents, there were 26 incidents of partial disruption, totaling over 134 hours of it, and 97 cases of degraded performance with summed up time of issues counted for over 669 hours (which is more than 80 working days!).
Though GitHub takes all the necessary measures to provide safe and secure service, it is also the user’s responsibility to take care of their data. Among the security best practices are periodic rotation of keys, regular repository scans, updates of the instance should GitHub release new patches, backup, and DR procedures.
GitProtect backup and DR software for GitHub is a safety net that ensures that in case of an outage, ransomware attack, or any other service disruption, your organization can resume work immediately eliminating data loss and ensuring piece of mind.
[FREE TRIAL] Ensure compliant GitLab backup and recovery with a 14-day trial🚀
[CUSTOM DEMO] Let’s talk about how backup & DR software for GitLab can help you mitigate the risks






