DevSecOps – Way to Improve Source Code Protection, Quality, Visibility, Monitoring, and Compliance
Last Updated on March 4, 2024
Automation is the key! It’s our mantra. It facilitates and speeds up many elements in our projects, especially repetitive aspects. Of course, it is impossible to automate everything, but I am convinced that in any IT project there would be something that a human is still doing today, although we could delegate these tasks to the machine.
There are two main advantages of automation:
- speed – a machine will do something much faster than a human
- and the correctness of operation – if an automatic process performs, for example, a backup of our code, no matter what, a program will always do it in the same way and will not make a mistake.
Each of us knows and cares about such things as quality, compliance, or code protection. It is necessary and expected. However, for various reasons, not all of us automate these activities. DevSecOps may be the answer to these problems.
What is DevSecOps
Let’s mix Security with DevOps. We can do that to increase the speed and frequency of software releases without increasing risk by compromising control. DevSecOps teams are able to detect vulnerabilities much faster than separate teams responsible only for Security. Above all, our entire process is safer, thanks to the fact that the people responsible for it – DevOps Engineers – also have knowledge in the field of security.
It is a kind of evolution in the organization’s security strategy. The sooner we obtain the appropriate level of security for our software, the faster (and cheaper) we will be able to deploy it. And this is possible thanks to automation in the continuous delivery of secure software, without creating bottlenecks at the end of such a cycle.
Let me quote a Manifesto from the page devsecops.org:
“By developing security as code, we will strive to create awesome products and services, provide insights directly to developers, and generally favor iteration over trying to always come up with the best answer before a deployment. We will operate like developers to make security and compliance available to be consumed as services. We will unlock and unblock new paths to help others see their ideas become a reality.”
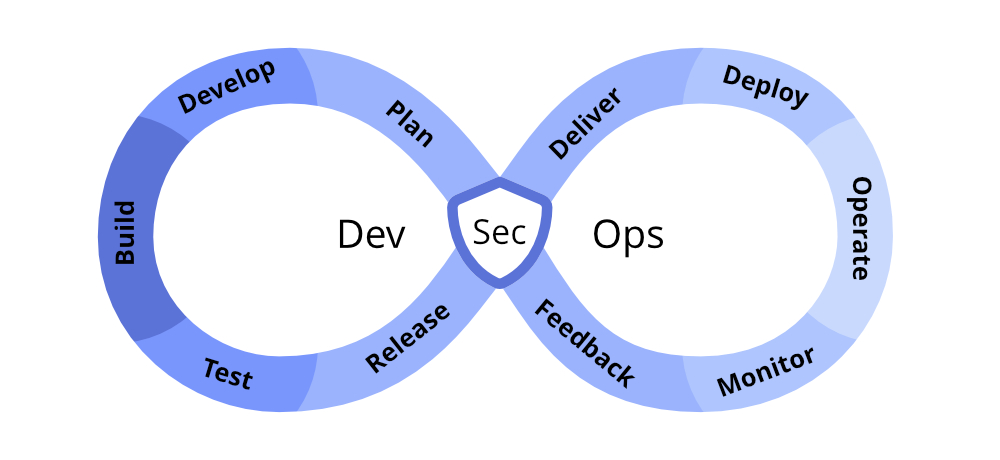
And here you can see it in the graphical form:
Source code protection
To achieve the highest possible level of security, we must take it into account from the very beginning of the software development cycle. Already at the design level, we should take into account our security and compliance policies. Then, during the development phase, the code must be constantly scanned and tested to make sure what is being produced meets our expectations. There is a similar mechanism in the 1-10-100 rule (costs of prevention – correction – failure), i.e. an apparently additional cost at an early stage, it is profitable in the long term. This is because we do not bear the cost of any corrections or errors that hinder the use of our software. We avoid these costs in the further stages because our solutions are safer and the number of errors is reduced.
Are you switching to a DevSecOps operation model? Remember to secure your code with the first professional GitHub, Bitbucket, GitLab, and Jira backup.
JAs IBM experts note, this approach is also beneficial in the case of the risk of an attack on our systems when some vulnerabilities are discovered:
This, surely, is not all. DevSecOps gives us many benefits in many fields.
We can of course integrate some cybersecurity tests together with other tests (e.g. integration tests) within our CI/CD pipelines. At any stage of code development. And as I mentioned at the beginning of this article – automation allows us to make a repeatable and adaptive process. And this guarantees the consistency of the operation of security mechanisms for the entire organization.
Continuous security monitoring
It is a good practice to track all vulnerabilities in one system, just like regular errors. Thanks to this, we have them all in one place and we can solve them and follow them in accordance with the already implemented process. It is worth highlighting here 4 steps to achieve the correct level of monitoring:
Application/API
Automation of error detection, distinguishing in which application, environment, container, or API the problem was detected. Use of self-reporting tools.
Custom code vulnerabilities
Software monitoring for vulnerabilities in the whole development process and beyond. For example, it might be a miss-sharing of some secrets or something like that. By the way, you can learn more about how to safely store secrets in GitHub in one of our past posts.
Open-source vulnerabilities and license issues
Critical topics when using external solutions. There is always a risk that something might be wrong with open-source libraries, we have to be prepared for it and we have to constantly monitor it.
Runtime exploit prevention
We also need to monitor our running applications, even if we do not change anything in them. There are situations when certain vulnerabilities come out after a long time, and a quick reaction can save us. An example is a famous situation with the Apache Log4j2 library from 2021.
As you can see, DevSecOps touches on many aspects. And although it requires both time and money, it is a cost-effective way to protect our software. With all steps in place, we can achieve a proper level of consistency, transparency, and also our whole security would be scalable and reusable throughout the whole company.
Conclusion
As Johann Wolfgang von Goethe said, “He who moves not forward, goes backward”. And it fits perfectly in the IT world. We must constantly develop, constantly chase trends or create them ourselves. What is the norm today will be obsolete tomorrow. DevSecOps is the way to improve source code protection, quality, visibility, monitoring, and compliance. And at the end of the day, those improvements can really boost our software delivery capabilities.