
GitHub Recovery Code
Each of us knows that the security of our data is extremely important. And even critical, especially if these data are not only photos from our vacation (although we would not want anyone to access them either) but e.g. business data or the source code of a commercial application. But what does that really mean?
How to secure an account
The standard method of securing an account on various portals is the login-password pair. And it’s ok, something like a lockable door – we need to know which door and which key we need, so not everyone will be able to enter. However, is it solid protection? Of course not and fortunately there are better ones that guarantee us a greater level of security.
Let’s get down to business in order not to play in generalities. GitHub cares about our security and allows us to secure our account in several ways:
- username and password with 2FA (two-factor authentication),
- personal access token,
- SSH key.
Asking yourself how to manage GitHub backup? Secure your source code with the first professional DevOps backup on the market.
Which method is your best option
I would like to highlight the one that uses 2FA in particular. It is a safe solution because even if someone learns our password, they will still need our device (usually a smartphone or other verified device) with an application that generates a one-time password code. Alternatively, such a code can be sent via SMS, anyway, this is an extra level of security.
Does it guarantee 100% security? Of course not. Since someone learned our password, we were probably the target of the attack, and in such a situation our smartphone could also be attacked in order to restore access and read the expected code.
Or we just lost or damaged our mobile device and we are simply unable to generate such a code. What then? GitHub recovery codes come to the rescue.
What are GitHub recovery codes?
These are special codes that we can (and must) save when we set up 2FA. If you lose access to your two-factor authentication credentials, you can use them to regain access to your GitHub account. It is also worth being aware that we need to know our password to use this option. But usually, this is not a problem, because we either just know them or we can easily recover them having access to the email. This mechanism is one of the GitHub account recovery methods.
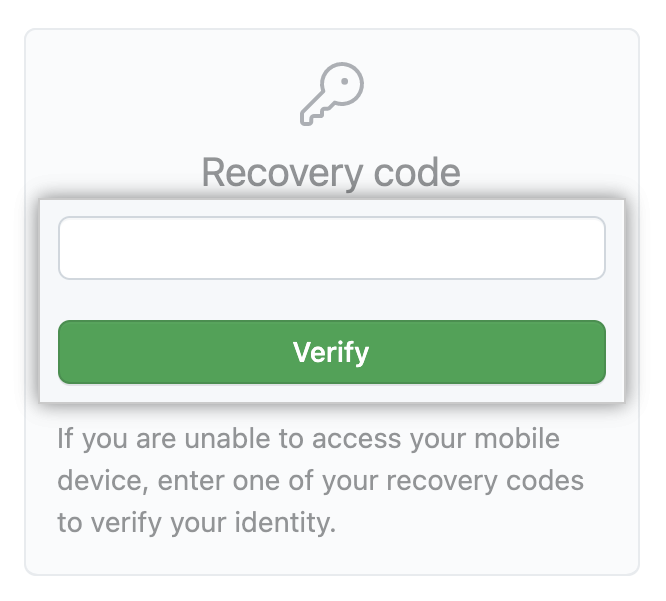
Anyway, on trying to log in, we must select the “Use a recovery code or request a reset” option, then enter one of our codes and confirm with the “Verify” button, as in the pictures below:
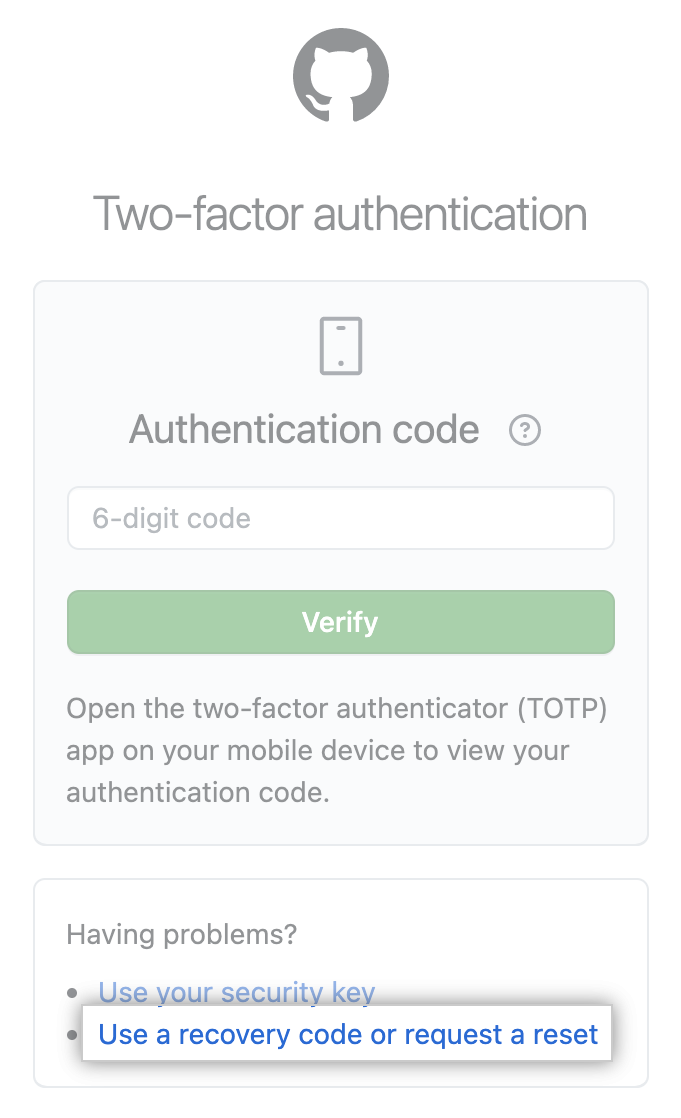
As you can see, this is an easy-to-use mechanism, as long as we know our codes. The GitHub interface allows us to easily see, download or print our codes, depending on how and where we want to store them, for example in some password manager. We can also generate a new set of codes at any time if the previous one has already been used or we have lost it.
GitHub meets our expectations and allows us to use a fingerprint-style Security Key, with a technology called WebAuthn. Here we can use a physical security key over USB or NFC, or even facial recognition if needed. We can add a security key at any time in the settings panel as a secondary authentication method.
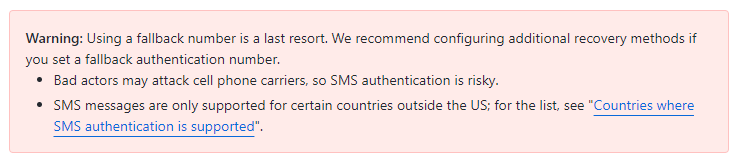
We also have the option to provide an additional fallback number to receive SMS with the recovery code, but it is not recommended. In the GitHub documentation we can see the following note:
“Where are my recovery codes?”
On various forums or portals, we can find entries about GitHub lost recovery codes or that the codes are not working. These are not isolated cases, but the problem is usually (or always) not with GitHub itself but with the way people use it. We need to remember a few things to use this functionality:
- Enter one code at time. A set of recovery codes contains more than one code. A single code is 10 alphanumeric characters in such format: xxxxx-yyyyy.
- Try using a different code as each code is single-use only.
- Check you’re using the right set of codes. When 2FA is reconfigured or when you choose to regenerate them, a new set of codes are created which invalidates the previous set.
At the end of the day, GitHub offers us the last resort method in case we don’t have valid recovery codes. We may receive a one-time password sent to our verified email address to begin the verification process and regain access to our account. It may take a few days, as the requests would be manually checked, but eventually, we can regain access to our account. Of course, we can try to use standard 2FA or recovery codes during that time if we regain access to them, but we are talking about the edge case, so it may cost us a few days of no access.
As you can see, the GitHub recovery codes mechanism is a fairly safe tool, but it puts us at risk if we misuse it. Also, as usual in the field of security – the weakest part is the human being. Could GitHub forget recovery codes? I do not think so. But you can, so pay close attention when using this feature.
You may find this topic interesting: git clone with SSH key. For many security experts, SSH is a golden standard, hence it’s worth implementing it into your git operations. Using SSH keys you can limit the risk of data interception by unauthorized persons. Another benefit is…
Frequently Asked Questions
How to recover a deleted GitHub account?
A deleted GitHub account cannot be fully recovered. Once it’s canceled, the account’s data, repos, and contributions are permanently removed. However, if the account deletion was recent, it may be worth contacting GitHub Support immediately, though recovery is not guaranteed.
GitHub is very strict about account deletion to protect user privacy and security.
Another case is if you have your own backup strategy applied to your GitHub account – it may be a backup script or professional backup and (disaster) recovery software, like GitProtect.io. In this situation, you can retrieve your data from the latest backup copy or any other point in time.
How do I authenticate GitHub without a password?
Using OAuth, SSH keys, or GitHub Personal Access Tokens (PAT) allows you to authenticate on GitHub without a password.
- OAuth is often used by apps, allowing access with permissions.
- SSH keys are ideal for command-line Git interactions, offering strong encryption.
- PATs are commonly used as a secure alternative to passwords. You generate each PAT in account settings, granting specific permissions to replace passwords in Git operations.
What is the 2FA verification code?
The 2FA (Two-Factor Authentication) verification code is a temporary, six-digit code generated by an authenticator app (e.g., Google Authenticator, Authy) linked to your GitHub account.
GitHub requires this additional code alongside your password to ensure secure access.
How long does GitHub keep data?
GitHub retains data as long as the account is active or by GitHub’s Data Retention Policy. After deletion, user data is removed (in general), but backups and archival copies may persist for a limited period as part of GitHub’s data retention practices.
Does GitHub Copilot collect your code?
GitHub Copilot does not explicitly collect code from private repositories. However, it uses data from a vast range of public repositories on GitHub for its training model.
When Copilot is enabled, it might process context from the code users are actively working on to provide relevant suggestions. Nonetheless, GitHub assures users that Copilot does not store or collect specific code content from private projects.
Does GitHub keep backups?
GitHub maintains regular backups of user data to ensure reliability and recovery in case of data loss or disaster. These backups are part of GitHub’s data resilience practices. However, they resemble more an autosave feature than a backup in its core meaning. The reason is GitHub stores the latest (the most recent) codes and files. That doesn’t include all the versions and earlier edits.
It’s also part of GitHub’s Shared Responsibility Model (SRM), which states that the user is responsible for the data (on his account). That means users should also consider maintaining local or third-party backups (S3-compatible storage, for example) for additional security.
What do I do if my authenticator code is not working?
If your authenticator code is not working, follow a few simple steps.
Check the device’s time settings
In other words, ensure your phone’s time is synced with the network automatically.
Use a recovery code
If you saved a recovery code during the 2FA setup, you can use it to regain access.
Try a different 2FA method
Use SMS or other backup 2FA options.
Contact GitHub support
Reach out to GitHub Support for assistance when none of the options work.






