
The Importance Of Verifying Your GitHub Environment’s Security Controls
Security is a top priority of every company. It’s not surprising… Source code, the most critical asset of any organization, should be under reliable protection… especially in view of constantly arising threats. Ransomware, infrastructure outages, vulnerabilities, and other threats can strike your GitHub repository at any time.
Organizations, especially those that operate in the most regulated industries, can face a few main challenges regarding their GitHub data protection. The first one, we have already mentioned – it’s the value of their data stored in the repositories; the second one is their ability to forecast any event of failure and take proactive measures to make sure that their data is available and recoverable in any event of failure.
What should a reliable GitHub security strategy include? Of course, here we should start with the backup of your critical GitHub infrastructure, as it will not only help you meet security compliance requirements, but also it will help you fulfill your Shared Responsibility obligations. Then, you shouldn’t store your credentials in GitHub, you should regularly scan your repositories, and always assess your access controls – so that only necessary permissions are given to each of your team members, etc.
Here are more tips on building your GitHub security strategy:
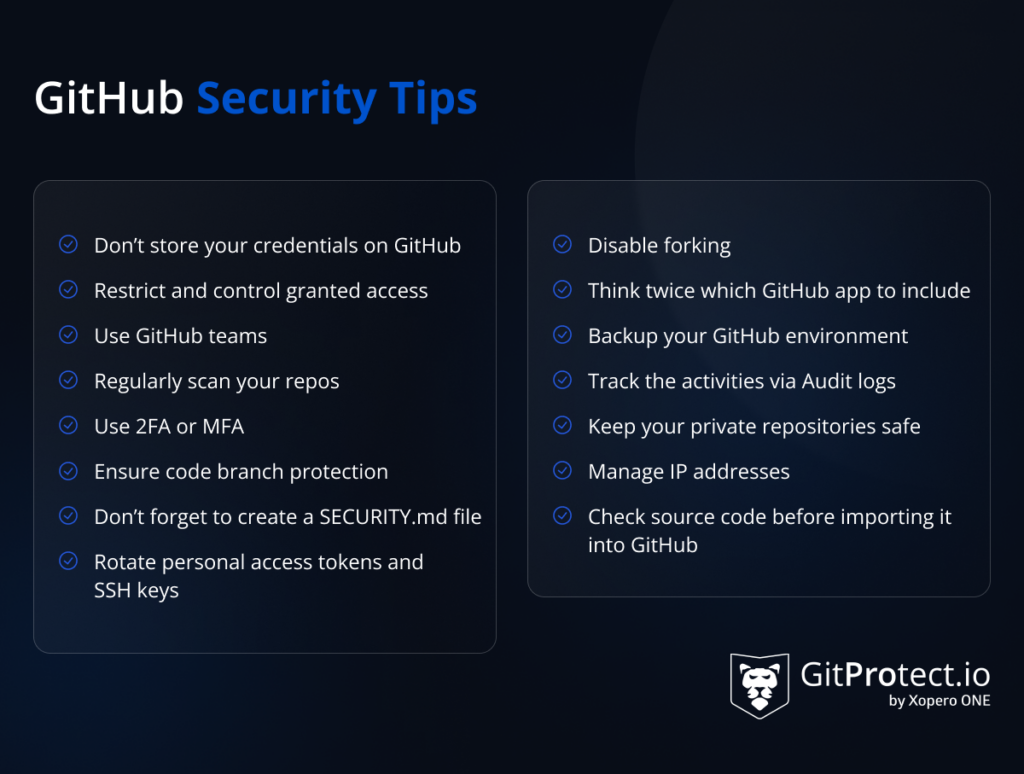
Well, the main topic of this article is the importance of verifying the security controls of your GitHub environment. So, why is it so critical?
Reason # 1 – Your GitHub source code data is valuable
Do you think that you are the only one who values your organization’s data? Let us surprise you – you’re not. There are other parties that are interested in your source code data. First, your customers. It doesn’t matter what industry you operate in – automotive, legal, healthcare, etc., you have your loyal customers who value your product and are interested in its security, reliability, availability, and the proper value of their personal data.
Then, there are bad actors who are always looking for a possibility to access your organization’s data and get a chance to enjoy lucrative paydays if their tries are successful.
Need an example? The 2024 Mercedes-Benz source code exposure, when a mishandled GitHub token and human error could open the door to the possibility of unauthorized data access, service disruption, intellectual property theft, and more.
Or, let’s remember about the 2022 Toyota Motor Corporation case. When the company warned its customers that their personal information – email addresses and management numbers – might have been exposed as the access key had been publicly available on GitHub for almost 5 years.
Here is a case from the finance industry: in January of 2024 Binance said about GitHub data leak and unauthorized upload of a “significant risk to Binance” data, which might cause “severe financial harm” and could potentially harm or confuse the company’s users.
And there are some other cases like that. Don’t take our words for granted – check out our State of DevOps Threats report, where we have covered the GitHub, GitLab, and Atlassian-related issues that could threaten your data and the best practices to prepare your organization for any possible event of failure.
Reason # 2 – It’s a regulation
A few phrases – Security Compliance and the Shared Responsibility Model. Let’s start with the first one – security compliance. In fact, there are some international, national, and state regulations that mandate you to protect your data. Of course, those regulations vary from industry to industry. Thus, for example, if you operate in a financial sector, you will need to comply with GDPR, SOX, GLBA, PCI DSS, FINRA, MiFID II, and other regulations. If your organization relates to the software development industry, you will need to meet the requirements of GDPR, CCPA, HIPAA, SOC 2, PCI DSS, ISO 27001, FedRAMP, and others.
So, once your organization understands which compliance protocols it should prioritize, you will need to focus on implementing security measures to meet those regulations. So to say, you will need to follow the security compliance best practices, which include backup and Disaster Recovery, automation, risk assessment plans, and robust security controls.
Another aspect that we mentioned is the GitHub Shared Responsibility Model. If you think that GitHub is fully responsible for the security of the data you keep in your GitHub account, you’re wrong. GitHub, as any other SaaS provider, operates within the Shared Responsibility Model which clearly defines the obligations of both parties.
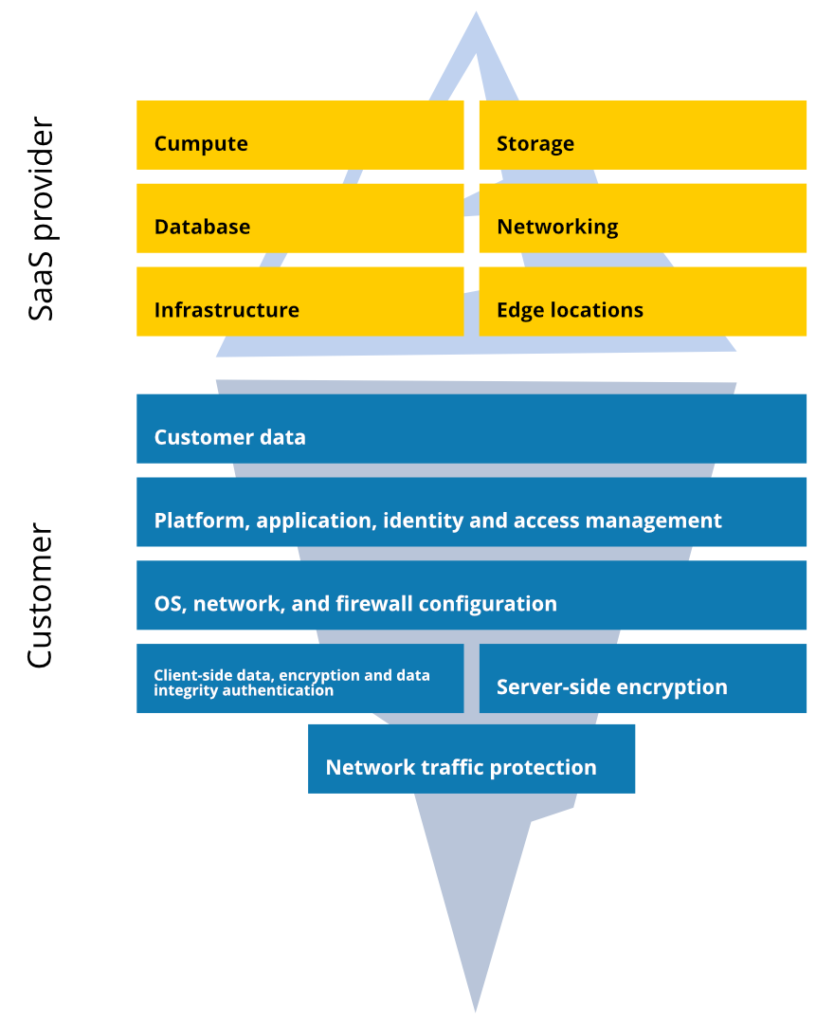
Thus, within it, GitHub is responsible for the smooth running of its operations and the security of the entire platform, but you, as a user, are responsible for the security of the data you keep in your GitHub account, and access management to your account.
Here is what is stated in the GitHub Terms of Service:
“You understand and agree that we will not be liable to you or any third party for any loss of profits, use, goodwill, or data, or for any incidental, indirect, special, consequential or exemplary damages…”
Find out more about the Shared Responsibility Model in our dedicated video:
Reason # 3 – Customers’ trust and reputation
High-profile data breaches may easily undermine an enterprise’s reputation or erode customers’ trust. Moreover, depending on the data your company leaked or even lost, your organization may face financial losses and compliance violation fines.
Thus, it’s important to build a DevOps data protection strategy effectively, forecasting any potential data corruption or data loss scenario.
Security measures GitProtect.io provides
The majority of compliance regulations require organizations to have their critical data accessible and available. Thus, backup and Disaster Recovery features are a must-have to guarantee data recoverability in any event of failure.
With GitProtect.io backup and Disaster Recovery software for GitHub, organizations can have peace of mind that they will be able to restore their critical GitHub data in case of a ransomware attack, infrastructure outage, etc., eliminating data loss and ensuring business continuity.
Thanks to the GitProtect.io multi-storage functionality, you can keep your data in a few storage locations and meet the 3-2-1 backup rule. Moreover, with ransomware-proof technologies, best-in-class remediation controls, and every-scenario-ready Disaster Recovery, the backup solution may empower your DevOps team with the necessary security tools to deal with secure and immediate GitHub data restore.
[FREE TRIAL] Ensure compliant DevOps backup and recovery with a 14-day trial🚀
[CUSTOM DEMO] Let’s talk on how backup & DR software for DevOps can help you mitigate the risks







