
Data Protection And Backup Predictions For 2025 and beyond
No matter how businesses look at it, the importance of data protection and backup in IT strategies will grow in upcoming years. These aspects have become vital to every business venture and are driven by increasing cyber threats and stringent regulatory requirements.
According to Gartner’s predictions, around 75% of enterprises will rely more on SaaS (Software-as-a-service) application backups. By 2028, they are expected to be a critical requirement for business ventures. Interestingly, Gartner points out that in 2024, companies’ percentage was only 15%.
Data security in SaaS applications
Recently, SaaS-based apps have supported businesses in enhanced deployments. The data generated and processed by the described applications is expected to be part of the fastest-growing business information sets by 2030.
Again, based on Gartner’s forecast, global spending on SaaS products was set to increase by 20% and reach $247.2 billion. Such an upward trend will likely continue, and companies will spend around $300 billion worldwide in 2025.
It derives from a well-known fact. Robust backup and recovery procedures are vital for safeguarding critical enterprise data, given the potential for IT failures.
As companies rely more on SaaS technologies, the need to protect data and make it recoverable is unavoidable.
“As product leaders, our mission is to ensure that backup solutions go beyond recovery—they become an integral part of a business’s resilience strategy, enabling organizations to grow with confidence in an increasingly data-driven world.”
Ostap Zaishlyi, Chief Product Officer, ActivityTimeline
In fact, it’s indispensable when you consider cyber attacks, potential human error(s), and vendor mishaps to which the SaaS data is vulnerable.
That, in turn, leads to higher adoption of BaaS (Backup-as-a-Service) solutions.
BaaS as a part of data protection
BaaS capabilities became essential for protecting information (against any data breach or security gaps) within cloud workloads and maintaining operational continuity.
75% of large enterprises will adopt BaaS alongside on-premises tools by 2028.
That also means that in 2025, businesses will be forced to pay more attention to the Shared Responsibility Model‘s specifics. Maintaining and keeping datasets safe (any security breach) requires companies to evaluate their data protection measures, including various service vendors in that field.
Customer is responsible for implementing and maintaining privacy protections and security measures for components that the Customer provides and controls. And that’s what you call a crucial reason for backup vendor diversification.
– Excerpt from GitLab’s subscription agreement
It is estimated that 60% of companies incorrectly assume that their SaaS providers are solely responsible for data protection.
That’s one of the reasons why third-party software (like GitProtect.io) may be considered comprehensive data security tools if the safety measures are insufficient. The latter may relate to limited API-based data access and recovery options.
With the explosive growth of cloud services and microservices architectures, API security will become a top priority. Attackers will target APIs as weak links in the security chain, leading organizations to adopt specialized tools to secure these crucial connections.
– Gary Miliefsky, Cyber Defense Magazine
That will also raise significant questions about adequate data protection (data breaches) and disturb support for third-party solutions for backups. Additionally, in 2025, businesses will still face a lack of industry standardization in that area.
Industry standards (sic!) for security
In 2024, the market got ISO/IEC 27040:2024 recommendations for backup systems and storage security. Although it can be considered a step forward, it’s still a guide (in 30% of requirements) with 220 discrete recommendations.
The market can also utilize NIST SP 800-209: Security Guideline for Storage Infrastructure. The document provides suggestions and guides for deploying, configuring, and operating storage resources.
However, financial institutions in Europe take a step further. The Regulation (EU) 2022/2552 framework, called the Digital Operational Resilience Act (DORA), shapes how entities above secure their data storage and backup solutions. The main goal is data protection against unauthorized access, loss, or corruption.
According to the Continuity Software survey, the internally mandated standards for storage, data protection, and backup systems include:
- NIST 800-53 (49%)
- PCI DSS (44%)
- CIS (33%)
- ISO/IEC 27000 series (30%)
However, following the survey, in 2025, among the top configuration challenges that IT storage teams will face are:
- hardware detection or software reaching end-of-support (65%)
- detecting deviations from ransomware protection best practices and vendor’s hardening guidelines (53%)
- on-demand configuration compliance evidence reporting (53%)
- benchmarking security posture score against industry peers (44%).
Service providers will be forced to raise their security and operational standards to meet increased customer expectations and comply with regulations like GDPR, DORA, and CCPA.
Theo Zafirakos, Cyber Risk and Information Security Expert at Fortra
Source: Cyber Defense Magazine
According to Gartner experts, to effectively safeguard SaaS-related app data in the near future, companies should bring more attention to:

Otherwise, businesses will have to face threatening data loss statistics. Various estimations show that 70% of organizations experienced data loss in SaaS apps in 2024.
How much data for protection in 2025
From a general perspective, data protection and recovery strategies are bound to broadly understood cybersecurity in the cloud and on-premise environments. This is even more significant as global data volume is growing incredibly fast.
The amount of data worldwide (global data storage) will probably exceed 175 zettabytes by 2025. According to Cybersecurity Ventures’ predictions, it could even exceed 200 zettabytes. Interestingly, almost 30% of the described datasphere will contain real-time data.
Furthermore, ABI Research suggests that the manufacturing industry will generate 4.4 zettabytes (ZB) of data annually, close to the total amount of data that mobile users will create worldwide.
Around 100 zettabytes will be stored in the cloud. That includes:
- vendor-operated public and social media firms
- clouds owned by governments
- private clouds provided by mid-size and large corporations
- cloud storage providers, including S3 solutions.
Don’t focus on big data; focus on the data that’s big.
– D. Reinsel, J. Gantz, J. Rydning, Data Age 2025
Nonetheless, data growth is not only about volume. The information set expansion also involves increasing complexity, immediacy, and frequency.
That makes the IT sector to put more resources into creating a more sophisticated approach to:
- storing data
- processing
- using the data for actionable insights.
Of course, the sheer volume alone raises challenges, increasing:
- cloud consumption, including information considered unnecessary
- storage costs
- data security with privacy infringement
- the requirement for detailed data analysis tools and techniques.
Researchers suggest that 29 million active software developers were employed in 2024. However, Developer Nation estimates that 45 million software developers will be hired worldwide by 2030.
In 2025, they will participate in writing and securing 338 billion code lines.
”Everyone on the development team should think about making sure the product is secure – and know it will be ready to help the customer, whether banking, manufacturing, industrial, or medical, ward off an attack.
– J. Boehm, J. Fuchs-Souchon, B. Klein, W. Salmanian, McKinsey & Company Insights
DevOps backup and disaster recovery – highly dedicated software
DevOps is a booming field with a high demand for skilled professionals. The US Bureau of Labor Statistics predicts a 22% growth in software developer jobs, including DevOps, from 2020 to 2030. The Grand View Research Inc. predicts that the global DevOps market will reach $37.25 billion by 2030, growing at a 16.8% annual rate.
In the upcoming years, developers and operations teams must collaborate more closely to ensure the security of the entire software development lifecycle – from code writing to deployment. The reason is simple. While DevOps accelerates software development, it introduces security risks at the same time.
“It’s not everywhere, and almost nothing covers part of the DevOps like developer workstations and IDEs and testing frameworks and plugins. I mean, there’s a universe of code that nobody’s monitoring, and most organizations are not really thinking about this problem.”
– Jeff Williams, CO-founder and CTO, Contrast Security
Source: Dark Reading
That’s why the DevSecOps approach should and will address the threat by integrating security into the entire development lifecycle.
Just to mention that in 2023, the number of events with the most significant negative impact on DevOps ventures did not exceed 14% – which was relatively good news:
- GitHub – 13.94%
- Bitbucket – 8.33%
- GitLab – 7.89%
- Jira – 4%.
However, most issues caused components to malfunction, leading to reduced performance. Fortunately, none of the popular DevOps providers experienced downtime.
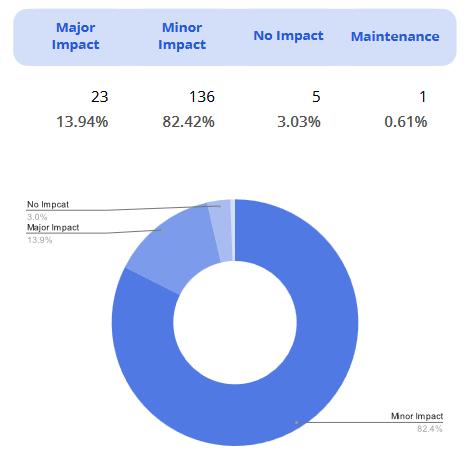
and their impact on customer operations.
Source: The State of DevOps Threats Report
In 2025 and later, due to the increasingly frequent threats and attacks on DevOps tools, there will be an increasing need to distinguish secure third-party backup solution(s) specializing in securing DevOps data from the general group of tools.
That is all the more so when DevOps resources (GitHub, GitLab, Bitbucket, Jira, etc.) contain a lot of vital repository data, including forked projects.
In addition, despite the widespread adoption of cloud-native technologies by 87% of companies, 59% remain unaware of the associated security risks. This lack of understanding has led to a rise in security incidents, including network breaches, API vulnerabilities, and misconfigurations, as evidenced by the Venafi 2023 survey.
In other words, education and training for DevOps teams will become increasingly necessary in the near future.
“Almost every security company offers automation in some form, and yet nobody is using it. Security teams should know that it’s okay to use automation to either block things that should be blocked, or to auto-remediate when you find something that contains vulnerabilities.”
– Laurent Gil, CPO, Cast AI
Source: Dark Reading
Organizations following DevOps principles and practices report a 208-fold increase in code deployments and a 2,604-fold faster lead time for changes. This translates to accelerated time-to-market (TTM), higher software quality, and, finally, fast-growing customer satisfaction.
That’s why, looking at 2025 and beyond, the DevOps market can expect:
- the growing development of AIOps (Artificial Intelligence for DevOps)
- DevSecOps being an undisputable part of the software development lifecycle
- GitOps teams fostering IaC ventures and faster deployments
- fast development of serverless computing.
Cloud and on-premise data repatriations
Gartner predicts cloud-based services will grow – spending will be over $723.4 billion in 2025. At the same time, cloud services will experience significant growth, with all segments projected to expand by double digits.
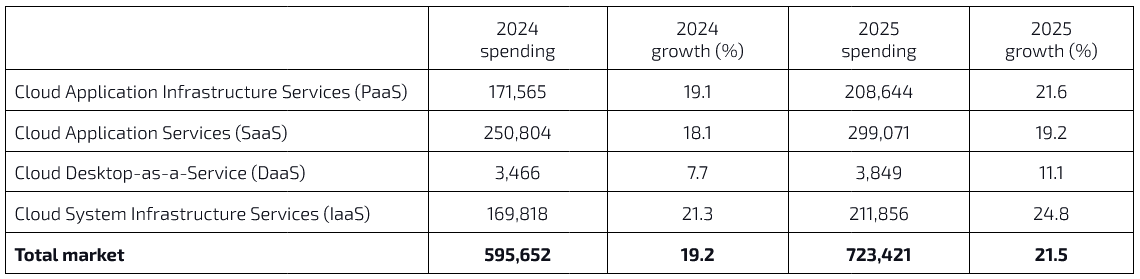
Interestingly, by 2027, most organizations 90%) are expected to embrace hybrid cloud solutions. Cyber Security Magazine described it as a “repatriation of data from the public cloud to on-premise.”
In practice, firms are expected to move their workloads from public clouds to on-premise for better cost management and efficiency.
Organizations that previously shifted to the public cloud now realize that a hybrid approach is more advantageous for achieving cloud economics.
– A. Spiteri, Australian Cybersecurity Magazine
In fact, they can now utilize and manage on-premises infrastructure using the same tools and automation processes previously exclusive to public cloud environments.
At the same time, companies are shifting towards hybrid and multi-cloud models, following evolving data privacy laws, strategies, and regulatory changes. That also includes market uncertainties.
Such a change aims to improve data accessibility, scalability, and sovereignty.
Cloud use cases continue to expand, with an increasing focus on distributed, hybrid, cloud-native, and multi-cloud environments supported by a cross-cloud framework. As a result, the public cloud services market will grow by 21.5% in 2025.
– Sid Nag, Vice President at Analyst, Gartner
It’s hard to deny that this approach poses risks like data loss and corruption. Information security and integrity concerns will lead many businesses to online vendors offering mature data resilience within their backup and recovery solutions.
Dark data as a part of sensitive data security risks
Along with the growing volume of data, troubles related to so-called “dark data” will follow. Based on the Manufacturing Leadership Council, the vast majority of global stored data will be information that is not actively processed, for example:
- log files – system and server logs
- previous employee data
- email correspondence
- surveillance video footage
- presentations, notes
- raw survey information
- financial documents
Various sources estimate that by 2025, 175 ZB of data will be generated each year globally. At the same time, less than 1% of this amount will be analyzed and processed for different purposes. The rest remain stored in databases or data warehouses.
That means, during the upcoming years, IT teams in companies and organizations will face multiple challenges, among others:
Lack of storage
Firms will deal with expenses related to storage space required to keep large volumes of unstructured or unused data.
Keep data secured
Storing sensitive data for extended periods poses risks. Identifying and removing unnecessary data (dark data) helps protect crucial information and ensures compliance with data protection regulations.
However, that requires more resources, tools, and expertise.
Troubles with accessing data
Dark data is challenging due to its unstructured nature and scattered location across various systems. This makes it hard to find and access a given information (and analyze it).
Privacy concerns
Working with dark data raises privacy concerns, as it may contain sensitive information that needs further protection.
DID YOU KNOW?
The GitProtect backup and restore system can help you meet the NIST Cybersecurity Framework regarding Protect and Recover requirements. Using GitProtect.io, you can:
– automate all DevOps stack backups
– connect any storage for replication (!)
– utilize Instant Remediation Center service (backup assurance with notifications, audit-ready SLA reporting, and visual stats)
– rely on unlimited retention for compliance.
Cybersecurity and costs regarding data protection
Considering the above information, the business also follows IT-related costs. Gartner (quoted by CRN) predicts that IT spending worldwide will reach $5.74 trillion in 2025. IT services will become the largest tech market (by sales), and businesses will spend around $1.74 trillion on IT services next year.
According to Gartner, data center systems will become the fastest-growing tech sector with $367 billion in global spending. Regarding the latter, other fastest-growing IT markets in 2025 will be:
- communication services ($1.59 trillion)
- software ($1.24 trillion)
- devices ($806 billion).
Based on the Verified Market Report prediction, the data backup software market will grow to over $25 billion by 2030, with a CAGR of 10% from 2024 to 2030.
On the other hand, according to IndustryARC forecast (2024-2030), the market will reach $22 billion in 2030 at a CAGR of 10.2%.
99% of IT decision-makers state they have a backup strategy. And yet, 26% of them couldn’t fully restore their data when recovering from backups.
– Survey by Apricorn
Undoubtedly, backup and data protection teams and the whole IT sector will constantly face challenges related to cyber threats.
The latter is evolving rapidly, from ransomware attacks using “double extorsion” tactics to AI-driven attacks affecting defenses and even human senses.
Cybercrime Magazine projects that cybercrime will cost a staggering $10.5 trillion annually by 2025, with a 15% yearly increase.
Simultaneously, global cybersecurity spending will reach at least $1.75 trillion by 2025. Following (among other sources) Splashtop’s prediction in that field, it’s worth underlining a few cybersecurity trends predicted for 2025.
Continuous Data Protection
Continuous Data Protection (CDP) is a growing trend. It offers real-time backup and recovery capabilities. Unlike traditional backups, CDP captures every data change, minimizing data loss to minutes or even seconds. That means CDP provides a more granular and up-to-date recovery approach, perfect for businesses with stringent recovery time and point objectives.
DID YOU KNOW?
Using the GitProtect.io backup and restore solution allows you to achieve the 10-minute Recovery Time Objective (RTO) working with S3 storages.
Utilizing AI for advanced threat intelligence
In 2025, AI will revolutionize cybersecurity by enabling real-time threat detection, predictive analytics, and automated incident response. These will empower businesses to combat sophisticated cyberattacks proactively and gain a competitive edge.
By 2025, AI-driven threat detection is set to enhance data protection, offering smarter, faster responses to threats. Zero-trust security is becoming essential, ensuring stricter access controls and encrypted backups.
Trung Le, Chief Security Officer (CSO) of DevSamurai
It’s vital as AI development introduces new coding and data handling methods. That creates a complex and much bigger attack surface that many DevOps teams may not be fully prepared to address. And the potential threats are still growing, for example:
- model poisoning (malicious data in training datasets)
- adversarial attacks (security breaches through incorrect decisions from harmful input)
- model extraction (AI model stealing)
- model inversion attacks (reconstructed sensitive training from model’s outputs)
- prompt injection
- AI supply chain attacks and others (codes and vulnerabilities introduced into AI frameworks or libraries).
In addition, the global market must be prepared for unknown dangers and methods of data theft and the compromise of crucial IT systems.
Zero-Trust architecture adoption
Due to the increasing complexity of modern cyber threats, the Zero-Trust approach will be a crucial cybersecurity strategy. Businesses will mitigate risks associated with remote work and hybrid environments by implementing least privilege access and micro-segmentation.
Zero-trust’s emphasis on continuous verification and robust access controls will protect sensitive data and IT systems against insider threat risks.
Supply chain attacks resilience
Supply chain cyberattacks will remain a significant threat in 2025. That means attackers will still target third-party vendors to compromise larger organizations.
As a countermeasure, businesses must strengthen supply chain security by vetting vendors, conducting risk assessments, and enhancing monitoring. Additionally, developing contingency plans and diversifying suppliers will help mitigate potential impacts.
Data protection via CaaS (Cybersecurity-as-a-Service)
In 2025, Cybersecurity-as-a-Service (CaaS) will become increasingly popular as businesses seek scalable, on-demand security solutions.
CaaS providers offer various services, including threat detection, vulnerability assessments, and compliance monitoring, often powered by AI. These solutions are particularly beneficial for smaller businesses without dedicated security teams.
Deepfakes detection and mitigation
Due to advancements in AI, deepfakes will become a more significant threat in 2025. Businesses will look for a proper detection solution, train employees to identify them, and establish protocols for verifying content authenticity.
By proactively addressing this issue, organizations will be able to protect their digital assets and maintain credibility.
Cloud security as a priority for data protection in 2025
Cloud security will be paramount in 2025. Firms may be forced to:
- adopt multi-cloud strategies
- implement strong encryption
- prioritize compliance and regular audits.
This way, they can benefit from cloud computing capabilities while minimizing vulnerabilities.
Conclusion
Data protection and backup are set to transform significantly in 2025 and beyond, driven by exponential data growth, evolving cyber threats, and regulatory pressures.
Gartner’s predictions emphasize the rising reliance on SaaS and BaaS solutions while hybrid and multi-cloud strategies gain traction for balancing scalability and efficiency.
DevOps backup is an accelerating trend in SaaS. Well over 300 billion lines of code, forecasted in 2025, is a vital part of companies’ activities and crucial Intellectual Property. These require well-designed protection, including third-party tools for GitOps teams conducting and securing data backups.
Challenges such as dark data, lack of backup standardization, and AI-driven cyberattacks demand proactive measures, including advanced analytics, Zero-Trust architectures, and Cybersecurity-as-a-Service (CaaS).
With IT spending projected to exceed $5.74 trillion in 2025, investing in resilient and innovative data security will be crucial. Organizations must treat backup and data protection as a strategic priority to ensure resilience and maintain a competitive edge.
[FREE TRIAL] Ensure compliant GitHub backup and recovery with a 14-day trial 🚀
[CUSTOM DEMO] Let’s talk about how backup & DR software for GitHub can help you mitigate the risks






