
Ransomware and Healthcare: How To Defend Against Evolving Cyber Threats
Given today’s reality of cyber security, healthcare organizations are always at risk of getting attacked. A Sophos‘s study outlines that out of the surveyed organizations, 59% have been impacted by ransomware attacks in 2024. What is more – only 22% have actually fully recovered in less than a week. However, for 37% of those institutions, it took over a month to recover. This is why it is crucial to adhere to regulatory frameworks and keep your data secured to the highest standard. To illustrate the seriousness of these threats, out of 2.8 billion malware attacks, 20% were actually ransomware.
To get more insight, take a look at how serious ransomware attacks were in 2024:

Source: 2024 DevOps Unwrapped
Healthcare organizations are vulnerable and often targeted by cybercriminals. Why? Well, they handle a lot of sensitive data and usually are one of the fundamental services necessary for a society to function properly. This is a perfect scenario for a cybercriminal to cause damage, so it is essential to implement reliable security strategies.
Why are healthcare organizations an easy target for ransomware attacks?
Healthcare institutions are at a significant risk of being attacked by ransomware due to several reasons. The industry deals with a large amount of protected health information (PHI), which is a very lucrative area to target for cyber criminals, and then demand ransom. Vulnerabilities and sensitive areas that could be exploited include:
- Valuable or sensitive data, such as national insurance numbers, social security numbers, or medical histories.
- Healthcare services are an essential utility on which societies depend and require urgent assistance. Knowing this, an attacker can leverage this sense of urgency to force an organization to pay ransom because otherwise, patients or other related entities could be impacted and at risk.
- Human error is a key vulnerability. Things like improper training, lack of awareness, and not following security protocols all pose a risk of a cyber attack.
- Lack of adequate funding is another issue. Underfunded organizations using outdated software or systems in general, simply cannot keep up with the rising cyber security threats. Limited abilities in terms of implementing industry-standard security measures are a serious vulnerability.
- While compliance is great for security as it ensures that an organization’s data is secured, it can also take lots of time and effort for a healthcare organization to go through all appropriate processes.
Most common entry points and causes of ransomware in the healthcare industry
It’s essential to address the entry points and vulnerable spots that cyber criminals exploit to breach data. These vary from simple phishing emails and lack of HIPAA compliance to unpatched systems or improper backup capabilities. Secure your data because all an attacker really needs is a single vulnerable entry point.
Phishing attacks
This is the most common entry point for ransomware attacks. Over 90% of all cyberattacks against healthcare institutions are phishing scams. These are usually in the form of an email or a text message and rely on social engineering tactics in order to trick people. Oftentimes, emails impersonate a trusted individual. Phishing simply exploits human vulnerabilities by preying on characteristics such as fear, urgency, or curiosity. Now, there are phishing attacks made specifically for stealing credentials, so once an attacker gets a hold of those, they can gain unauthorized access.
Improper authentication and access management
Healthcare entities should have proper authentication procedures in place, especially with such sensitive data as in the healthcare industry. Do not allow weak passwords, keep the network secure, and implement multi-factor authentication (MFA). This is the first point of entry to data, therefore, it is essential to keep the authentication procedures secure to prevent cyber criminals from stealing credentials.
Overly excessive access permissions can create holes in cyber defenses. It is important to implement Role-Based Access Controls (RBAC) and adhere to the least privilege principle. Revoking access to unused accounts is another thing to pay attention to. Only give access permissions that are necessary for an employee to complete their tasks. It is advisable to monitor the given access and regularly update it.
Lack of proper backup & recovery capabilities
An attacker can rely on the fact that there are no proper backup capabilities implemented into an organization, or even a lack of swift recovery/restore strategies. An attacker steals the data knowing there are no backup copies and therefore (most likely) no reliable recovery solution, and simply demands a ransom.
Unpatched software
Leaving software updates or patches to the last minute is a bad idea for several reasons. Attackers using ransomware will exploit any vulnerabilities in the software to gain access to data. Healthcare professionals must keep in mind that both known and unknown vulnerabilities can be exploited by the threat actor – therefore, just because you cannot spot a security hole in your cyber defenses, it does not mean that there aren’t any vulnerabilities.
Known cybercriminal ransomware groups
To raise awareness, it is important to know the ransomware groups affecting the healthcare industry. The large-scale operations of these groups show the need for better security of computer systems, medical devices, and more serious security rules. While there are many criminal organizations to look out for, we point out the most popular ones below.
LockBit
This ransomware group first appeared on Russian cybercrime forums in January 2020. As of now, LockBit is huge despite many attempts to dismantle it and was responsible for 9.4% of all ransomware attacks back in 2023. This group operates under a Ransomware as a Service (RaaS) model and recruits individuals to carry out attacks. This keeps everything decentralized but still effective.
LockBit 3.0 has attacked 68 healthcare organizations in 2023. The organized effort by law enforcement suggests the seriousness of the threat that this ransomware group poses to healthcare organizations (the group is still operational despite efforts).
BlackCat (ALPHV)
This cyber gang first emerged in November 2021. In February 2024, the U.S. Department of State announced a 10 million dollar reward for any information that could lead to dismantling this organization. In 2023, BlackCat was responsible for 61 attacks on healthcare organizations.
CL0P Ransomware Gang (aka TA505)
CL0P ransomware is operated by TA505, which has been active since 2014. Back in May 2023, the group started exploiting zero-day exploits in MOVEit Transfer. It is outlined that the group is responsible for mass attacks on over 130 organizations, including health and human services, by exfiltrating data from the GoAnywhere MFT. This group remains active despite efforts to destroy it.
Real world examples of ransomware affecting healthcare institutions
The first example is New York Blood Center Enterprises. Their IT systems were hit with ransomware on 26th January 2025, and they were forced to take some of the systems offline. At least 8 different operating divisions were affected. Since 3rd February 2025, all activities have resumed, although it has been stated that some manual processes are still in place, wait times are longer, and inbound calling is disrupted at two different divisions (Memorial Blood Centers, and Nebraska Community Blood Bank).
Another notable instance is Frederick Health Hospital and Emergency Department. It is stated that their IT systems were affected by ransomware on the 25th of January 2025. The institution claims to remain operational, apart from Frederick Health Village Laboratory – which is temporarily closed. The work to restore their systems is now underway, and law enforcement has been notified too.
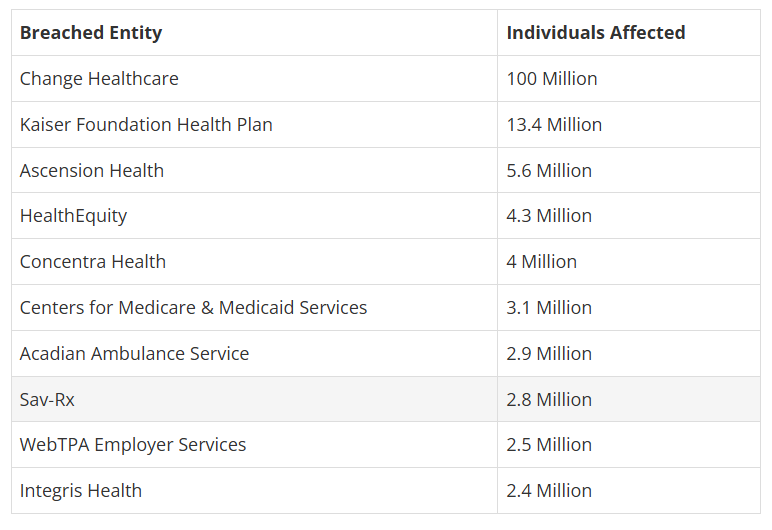
Largest data breaches
This is only for this year, and… it is only February. A 2024 study by Microsoft has outlined that almost 400 US healthcare organizations were attacked using ransomware, with an average payment amounting to $900K. This is a rather worrying trend calling for more awareness regarding proper cyber security practices. Take a look at 10 largest U.S. health data breaches in 2024 – as outlined by the U.S. Dept. of Health and Human Services:
The cause, effect, and how to prevent
Researchers point to several aspects when it comes to the question of “why” is the healthcare sector being targeted with ransomware. Well, here are the main ones:
- The healthcare sector is a critical service and its unavailability can lead to putting human life in danger. Cybercriminals believe such institutions are more likely to pay ransom in order to secure critical business continuity and also maintain public trust – as healthcare data is rather valuable.
- The COVID-19 outbreak further expanded the usage of virtual care technologies, leading to even more extensive networks of vendors, partners, and suppliers being relied on for simple daily tasks. Due to this fact, the attack surface is now much larger for a threat actor.
- Another aspect is the fact that healthcare institutions often rely on outdated, legacy systems. Such systems do not have proper cybersecurity measures and protocols within them and therefore put data security at risk.
Healthcare providers need to look out for industry standards and relevant regulations in the healthcare industry to keep patient records secure. One of them is the Health Insurance Portability and Accountability Act (HIPAA) – let’s break it down in the following paragraph.
HIPAA compliance
The main reason why HIPAA should be outlined in more detail is due to the fact that it is one of the most known and respectable regulatory frameworks for the healthcare industry. The Health Insurance Portability and Accountability Act (HIPAA) is a framework made to protect sensitive patient data.
HIPAA certificate
We specifically outline HIPAA regulations because being HIPAA compliant is an industry standard for healthcare providers. Unsecured protected health information is a violation of HIPAA compliance and furthermore your organization will struggle to pass relevant risk assessments. The HIPAA regulation is a standard for the protection of certain health information. What is more, there is the Security Rule that sets similar standards for health-related data protection but the HIPAA Security Rule applies to data that is held or during transfer in an electronic form.
Make sure that HIPAA certification requirements are clearly understood to secure data and avoid legal fees. As you may be aware, HIPAA certification requirements include backup along with disaster recovery capabilities as outlined in Art. VI:
“Administrative procedures – documented, formal practices to manage the execution and selection of security measures to protect data and to manage the conduct of personnel to protect data, i.e. audits, training, disaster recovery.”
Source: Art. VI. Security Requirements, HIPAA
However, that’s not all. Other relevant industry frameworks include:
- NIST,
- HIPAA (The Health Insurance Portability and Accountability Act),
- CIS,
- COBIT,
- ISO/IEC 27001,
- HITRUST/CSF,
- QSR,
- PCI DSS
- SOC 2 type II
Best practices for compliance & security in the healthcare sector
Start off by adopting zero-trust architecture – no individual in or outside the organization is trusted with access to data by default. At the end of the day we are discussing protected health information, so breach notification rules may be a good idea. Such a breach notification rule should be thoroughly examined and communicated to employees. Healthcare entities should cover multi-factor authentication (MFA) for all users, implement role-based access control – based on job requirements, and adhere to the principle of least privilege.
RPO and RTO
Next, you need to calculate your RPO (Recovery Point Objective) and RTO (Recovery Time Objective). The former details how much data can be lost in the face of a security breach. The letter outlines the maximum time that can be taken for systems to be restored following an outage. Make sure to frequently test and adjust your backup and recovery strategies so that they reflect your RPO & RTO metrics.
Identify vulnerabilities
In order to stay prepared and protected from potential data breaches, you need to stay up to date with the arising cyber security threats. Moreover, it is important to carry out a risk assessment as well as a vulnerability analysis, to spot any potential security holes or threats that have been overlooked.
Test, monitor, and report
The implemented security procedures need to be reviewed and tested regularly and thoroughly to guarantee their effectiveness. In addition, appropriate monitoring as well as reporting mechanisms should be in place to ensure full visibility over processes taking place and be notified of any relevant security issues in a timely manner.
Of course, it is necessary to undergo audits and aim for your organization to stay in accordance with relevant regulatory compliance. These include things like the physical site audit, security standards audit, and device audit.
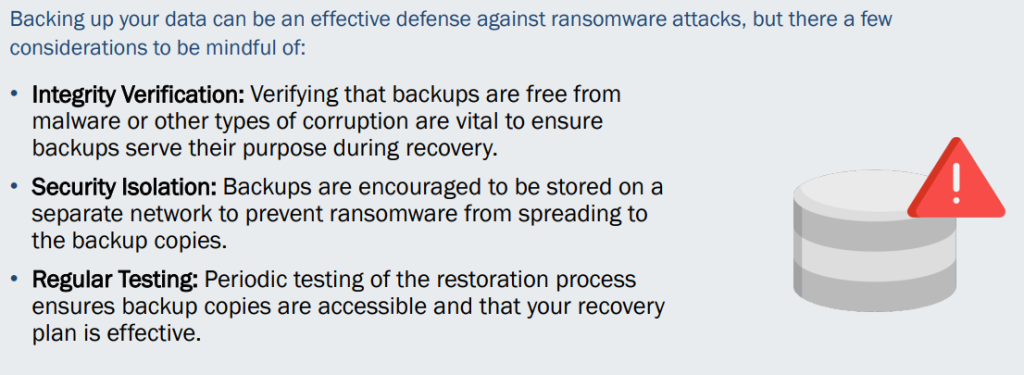
Complete backup & DR solution
For complete cyber security, it is essential to address data backup and recovery in healthcare. Not only will it boost your data protection but it is a general best practice to improve cyber defenses, as well as certain regulations requiring healthcare organizations to implement complete third party backup & DR solutions to maintain compliance.
Source: Ransomware & Healthcare
Make sure backups are in an immutable format, replication is in place, backups are encrypted, and the restore & recovery processes accommodate all of your needs as well as guarantee compliance.
Educate your team
Last but not least, training staff is another critical aspect of healthcare cybersecurity. The human factor is still a large vulnerability when it comes to cyber-attacks. It is important to communicate all relevant cyber security information, such as healthcare laws, to all employees, train for phishing awareness, and make sure to have proper drills in case any security incidents take place. Moreover, make sure to have HIPAA compliance training in place in order for your healthcare organizations to be HIPAA certified.
Conclusion
To sum up, healthcare providers are often targeted by cybercriminals through the use of ransomware. Data breaches are common nowadays but they are a huge threat to human life when it comes to the healthcare industry.
Due to the nature of the healthcare sector, threat actors often take advantage of the fact that human lives can be at stake, and therefore, organizations are more likely to pay ransom. That is why compliance with regulatory frameworks and robust backup, along with disaster recovery, is a necessity. This is not just to keep patient data protected (such as medical records) but also to prevent any downtime and ensure there is no risk to human life. Therefore, it is crucial to introduce proper backup processes, HIPAA training, along with physical safeguards.
[FREE TRIAL] Ensure compliant DevOps backup and recovery with a 14-day trial 🚀
[CUSTOM DEMO] Let’s talk about how backup & DR software for DevOps can help you mitigate the risks in healthcare






