
Data Backups In Terms of Data Residency
Nowadays, thinking about backups in terms of redundancy alone is old-fashioned. Along with the ‘what’ and ‘how’ approach, it’s vital to ask ‘where’. And it’s not a matter of GDPR or HIPAA requirements. Knowing about your backup location(s) can be a factor that distinguishes between mere compliance and a catastrophe.
After all, underneath every DevOps pipeline, CI/CD tool, and Git-based collaboration platform lies a deeper question few decision-makers ask: “Where exactly is this data stored, and is that even allowed?”
And yet, looking at the global regulatory landscape, the data residency concept is mission-critical. Fines for violating it are real. Besides, regulations are tightening, but backup practices are usually the weakest link in the compliance chain.
Data residency. How to understand the violation vector
Date residency refers to the physical or geographic location where data is stored. In many industries, such a location is non-negotiable. Financial and fintech organizations operating in the European Union that work with customer records must comply with the GDPR. It mandates that personal data must remain within the European Economic Area unless stringent transfer mechanisms are in place.

The graphic was created with the help of AI tools
Similar principles apply to Australia’s Privacy Act, Canada’s PIPEDA, and Brazil’s LGPD. It’s worth underlining that the United States brings its own set of headaches. HIPAA governs healthcare institutions in the U.S. It limits where protected health data can reside. Going further, government contractors are subject to frameworks (policies) like:
- FISMA
- DCID
- DoD Cloud Computing SRG
- FedRAMP.
U.S. financial companies are subject to and comply with GLBA and SEC storage rules. In each of the mentioned cases, knowing where data sits is as essential as knowing how it’s protected.
In short, all these regulations require strict control over sensitive data locations. That also includes backups and where they are housed.
Despite all the examples, backup solutions are rarely designed with these restrictions in mind. Many tools treat backup just as a mere disaster recovery mechanism. Their functionalities ignore the fact that the very act of duplicating data into another region may violate a specific policy.
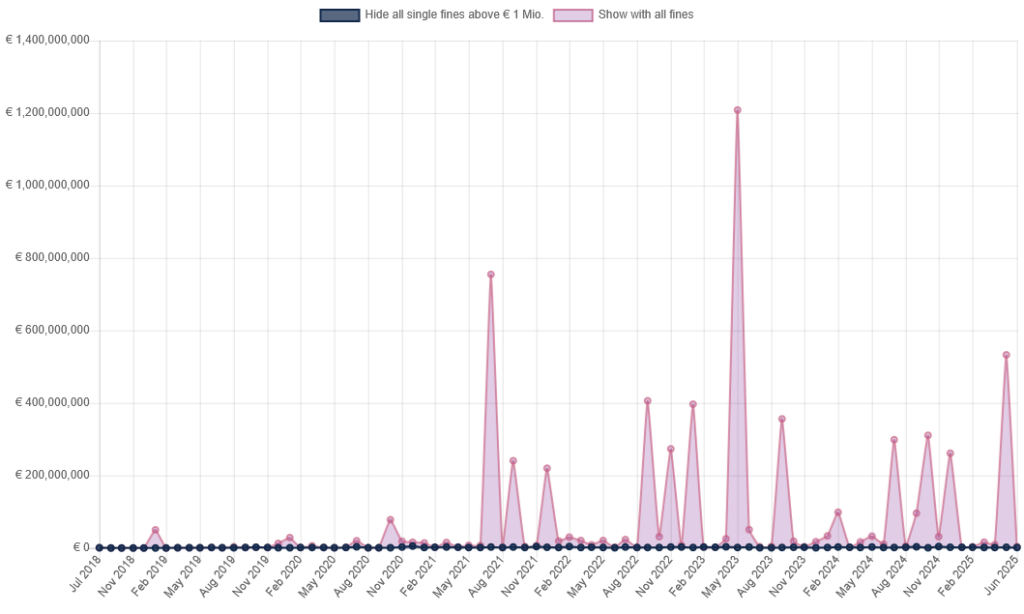
Sum of fines per month: Jul 2018 – Jun 2025 (non-cumulative). Source: GDPR Enforcement Tracker.
In 2023, more than €2 billion in GDPR-related fines were issued. A significant portion of these (€1.2 billion) fines stemmed from violations of cross-border data transfer regulations. Other hefty fines were also issued for non-compliance with data processing principles and security measures.
Fortunately, in 2024, GDPR fines (across Europe) totaled approximately €1.2 billion, making a 33% decrease. Nonetheless, it’s still a considerable number.
And it doesn’t matter whether the data is encrypted or if it’s never addressed. When it’s stored in an unapproved region, the violation is committed. And it’s considered a breach. End of story. That means compliance is location-aware.
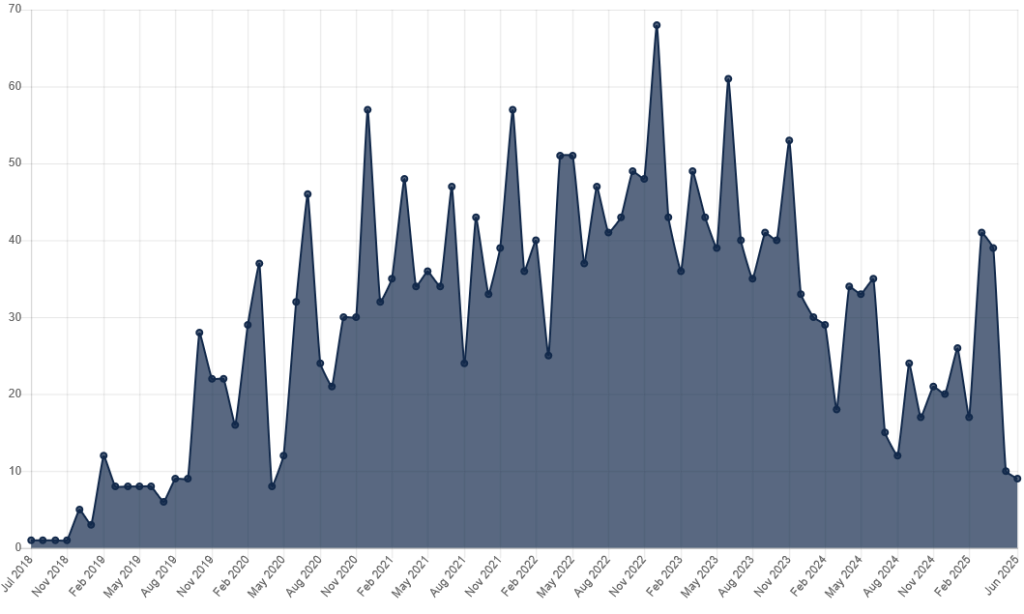
Number of fines per month: Jul 2018 – Jun 2025 (non-cumulative). Source: GDPR Enforcement Tracker.
GitProtect and its Residency – Control before compliance
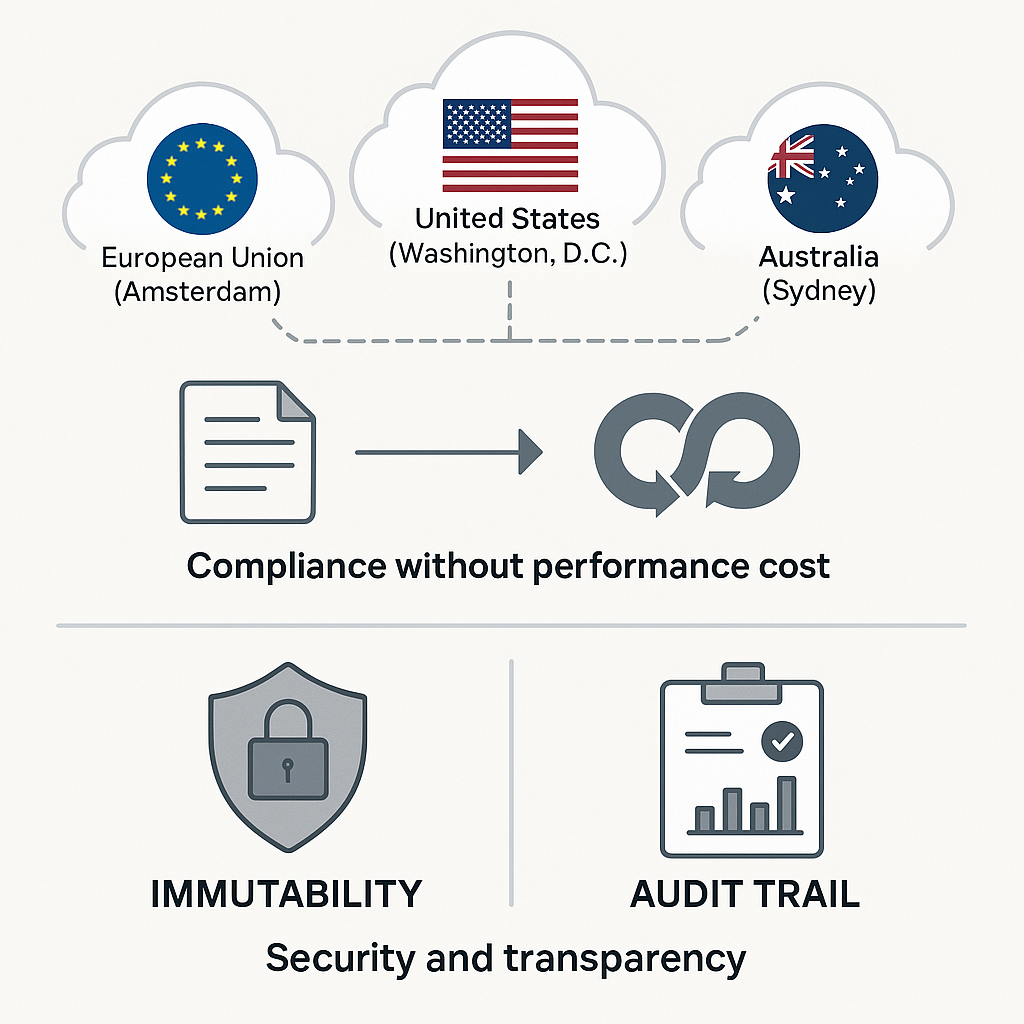
Here, GitProtect takes a fundamentally different approach. Rather than treating backup storage as a backend detail, it provides enterprises with complete control over data residency from day one. During deployment, organizations choose where their backups are stored.
Regional options include the following:
- European Union (Amsterdam)
- United States (Washington, D.C.)
- Asia-Pacific (APAC, Australia)
Of course, these are not just availability zones. Each of these is a compliance-aligned and enterprise-grade data center that meets a deep roster of security standards, requirements, and certifications:
| ISO 27001 | SOC 2 Type 2 |
| FISMA | DCID |
| DOD | HIPAA |
| LEED Gold | SSAE 16 |
| EN 1047-2 | EN 50600 |
| PCI DSS (Level 1) | |
Each regional facility provides physical security, fire suppression, network monitoring (24/7), and regular (routine) audits as a part of the operating baseline, not add-ons. These are all critical components for regulated industries.
For many companies, this cloud-first residency control is sufficient. A financial company, like a bank, may insist that all production and backup data remain within the EU’s legal perimeter. At the same time, a Boston-based biotech firm might anchor its storage exclusively in the United States to meet HIPAA or FDA requirements.
GitProtect’s managed regional sites make both strategies viable without dragging performance down or complicating recovery.
What stands out in practice is that compliance doesn’t come at the cost of efficiency. Keeping copies within the designated geography allows teams to then restore code repositories or CI/CD pipelines with minimal network latency.
It’s usually crucial in regulated industries. There, every hour of downtime becomes financial and reputational damage. In the meantime, storage expands elastically as projects grow, avoiding the hard ceilings and costly rearchitectures that often plague fixed-on-prem setups.
The security model goes deeper than a tick-box of “AES-256 encryption.” GitProtect adds immutability features that make backup data resistant to tampering or ransomware encryption. The system equips administrators with a continuous audit trail – where data resides, when it is moved, and how long it remains under retention. This transparency transforms data residency from a theoretical policy into something demonstrable in front of auditors or regulators.
The graphic was created with the help of AI tools
In other words, cloud-first residency control becomes not only a compliance safeguard but also a resilience booster.
Yet, regulatory compliance often demands more than choosing between pre-configured regions. Some organizations, particularly those in defense, energy, biotech, or critical infrastructure, require full custody over data storage and traffic.
Considering these and other cases, GitProtect brings a fully on-premise deployment model. That means backups can be performed inside the customer’s own infrastructure. Whether that’s:
- a locked physical data center
- a designated compliant cloud region
- a government-compliant Azure region (e.g., Azure Germany)
- an isolated AWS partition (e.g., AWS GovCloud).
GitProtect doesn’t compromise on functionality here. On-prem users still get the full site:
- granular restores
- immutable storage policies
- role-based access
- flexible storage targets (NAS, object storage, cold storage, tape, etc.)
- API control
- compliance grade reporting.
A great example of a multi-region, residency-conscious backup strategy is Red5. The company implemented GitProtect with a 3-2-1 architecture, using multiple, geographically separated storage locations to ensure both compliance and redundancy. Their setup reflects a real-world response to data sovereignty and disaster recovery requirements.
“Working through standard best practices and compliance caused us to re-evaluate
all of our backup methodologies.” – Mark Pace, CTO at Red5
Compliance-grade reporting, hybrid needs, and retention
When it comes to reporting, it’s not enough to be compliant. You need to prove it. If so, then you need a solution that provides automated, compliance-ready reports covering backup status, retention enforcement, storage location, and recovery validations.
The above is especially useful during audits or when responding to vendor or regulator questionnaires. It’s not about keeping IT happy, but shielding the business from avoidable risks.
There are also cases where organizations have hybrid needs. Enough to mention global DevOps teams that seek fast restores in-region and long-term storage elsewhere. The goal is to store primary backup copies in a compliant public cloud region while keeping secondary encrypted backups (AES-256) inside your own infrastructure.
Such a dual approach enables businesses to strike a balance between performance and governance without compromising either.
This is well illustrated by Ammagamma, an Italian data science company working under ISO 27001 standards. GitProtect’s detailed reporting and retention policies enabled them to document every backup and restore operation, a critical requirement during security audits. With an unlimited retention configuration, they could retain data for as long as ISO requirements or client policies demanded.
“I like very much the possibility to back up from one environment and restore the repo to another environment.” – Silvio Umberto Zanzi, IT Manager at Ammagamma
And here is one more thing. A frequently overlooked challenge in this domain is data retention. Some information (data) needs to be retained indefinitely. Not because it’s technically valuable, but because legal frameworks require it. And again, the GitProtect system doesn’t impose artificial limits here.
With unlimited retention, organizations can configure policies that align with their regulatory timelines, rather than their vendor’s pricing model. For example, if a given regulation requires 7 years of history or longer, GitProtect allows you to configure it accordingly.
Of course, GitProtect supports automated reports and mixed models, matching needs and challenges in full.
Conclusion
No matter how someone looks at it, at the end of the day, data residency is not a checkbox. It’s a lively, dynamic intersection of legal requirements, technical capabilities, and organizational accountability. Backups now are at the center of this challenge.
Because when a breach happens, regulators won’t just ask how fast you can recover. They’ll be interested in where your backups were stored, who had access, and whether your policy was enforceable. If you don’t know, you’re already in serious trouble.
And here’s the thing. GitProtect’s architecture, storage model, and compliance toolset are designed for precisely the reality we described so far. The tool meets the needs of modern businesses that can’t afford to treat data residency as someone else’s problem. If you have it, it’s yours.
And your backup had better prove it.
[FREE TRIAL] Ensure compliant backup and recovery of critical DevOps data with a 14-day trial 🚀
[CUSTOM DEMO] Let’s talk about how DevOps backup & DR software can help you mitigate the risks






