
Security Compliance Best Practices
In view of the constantly emerging threats, more and more companies are understanding that they need to level up their responses to risks and adopt more strategic compliance operations, leaving checkbox compliance behind.
According to the 2024 IT Risk and Comliance Benchmark Report, the number of companies that have started paying more attention to security risks and tied them to compliance activities has risen by 80%. However, the number of those companies that have already done this is still low – only 18%. However, what’s positive: their number is constantly growing.
To meet the Security Compliance standards, organizations should develop effective security compliance management and define the security policies they need to comply with. It will help to ensure that compliance violations are resolved. Among the most regulated industries are healthcare organizations, insurance, pharmaceutical, energy, telecommunications, and financial institutions, which are often victims to cyber threats and multiple data security threats.
Why do you need Security Compliance?
There are many reasons why compliance is critical. It’s important for the security of sensitive information, mitigating risks, meeting regulatory obligations, building trust and reputation, and staying ahead of your competition.
Moreover, achieving regulatory compliance is one of the most important aspects when it comes to the cost of security breaches. If the company isn’t compliant with strict security practices and standards, its expenses in the event of data breaches can be much higher. For example, according to IBM’s Cost of a Data Breach Report 2023 report, the average cost of data breaches of a compliant company was USD 5.65 million, while non-compliant organizations had to spend around USD 2.3 million more after being fined for security incidents.
It can be explained by the fact that non-compliant organizations can face fines for security breaches and lawsuits, and their reputational damage can be higher as well.
What Security laws and industry standards does your organization need to comply with?
Well, let’s look at the most popular security frameworks that companies from different industries may need to be compliant with:
NIST Compliance Standards
NIST, developed by the USA, contains more than 1,300 standard reference documents. However, it’s the NIST 800 series that includes the majority of compliance frameworks. Among the most popular, we can mention:
- NIST 800-53, which is mainly oriented at governmental institutions, including federal information systems, agencies, and associated government departments. The framework aims to provide a foundation of guiding principles, tactics, technologies, and security controls that support any business operations and cybersecurity needs and priorities.
- Like NIST 800-53, NIST 800-171 is a framework that provides requirements for safeguarding the confidentiality of controlled unclassified information. The only difference is that NIST 800-171 is oriented toward federal agencies that work with non-governmental organizations.
- NIST 800-161, which is aimed at enhancing Software Supply Chain Security.
- NIST Privacy Framework, which is intended to assist businesses in identifying and managing privacy risks, so that they can build innovative services and products while safeguarding individuals’ privacy.
NIST Cybersecurity Framework (CSF) 2.0
Recognized as the most commonly used compliance framework year-over-year (according to the 2024 IT Risk and Comliance Benchmark Report), NIST CSF is developed for individual businesses and other organizations to assess security risks they face.
The NIST CSF is founded on 6 main functions – Govern, Identify, Protect, Detect, Respond, and Recover. In turn, those functions are subdivided into another 23 categories and 108 subcategories, each of which resonates with specific sections of other information security standards, including ISO 27001, NIST SP 800-53, etc.
The framework lays out a structured approach to help companies evaluate and improve their overall security posture, focusing on continuous monitoring, risk management, and regular assessments.
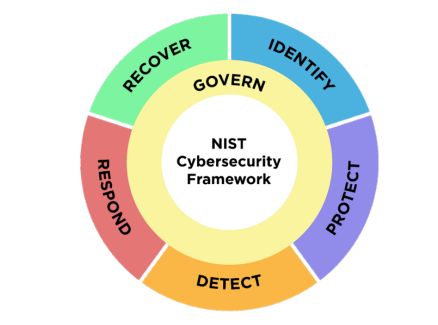
Source: The NIST Cybersecurity Framework
- Within Govern, the framework recognizes that “the organization’s cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored.”
- Identify means that the organization understands the current cybersecurity risks it may face.
- Under Protect, the NIST CSF requires the company to understand its organization’s cybersecurity risks.
- Within the Detect function, companies agree that they will do their best to find and analyze possible cybersecurity attacks and compromises.
- According to Respond, organizations agree that “actions regarding a detected cybersecurity incident are taken.”
- In accordance with Recover, organizations should guarantee that “assets and operations affected by a cybersecurity incident are restored.”
ISO 27001
Also known as ISO/IEC 27001, the data security framework outlines the requirements for building, monitoring, and improving an information security management system (ISMS), including financial data, intellectual property, customer details, employee records, etc.
To become certified within ISO 27001, organizations should follow international standards for Confidence, Integrity, and Availability. What’s more, they need to guarantee their own and their customers’ data safety. Thus, they need to address such important elements as Organizational context, Scope, Leadership, Planning, Support, Operations, Performance evaluation, and Improvement.
📎 Check GitProtect.io’s way to become ISO 27001 certified: ISO 27001 certification – GitProtect’s by Xopero Software ISO 27001 audit process explained
GDPR
The General Data Protection Regulation (GDPR), enacted by the European Union, is a legal framework that sets out instructions for collecting and processing personal data. The GDPR’s compliance monitoring statutes center around personal data processing, holding companies responsible for how they respect individual rights, gather lawful consent, and establish proper data handling mechanisms. Though, General Data Protection Regulation is widely used in Europe, organizations outside the EU that process data belonging to EU citizens still need to follow that protocol.
Within GDPR, organizations should handle personal data in a way that prevents unauthorized data collection, processing personal data, loss, or damage. Failing to achieve compliance may result in fines of up to € 20M or 4% of the company’s yearly income.
SOC Certifications
Compliance with SOC Certifications assumes that a service provider has passed third-party audits and operates within certain security protocols. There are several levels of SOC compliance:
- SOC 1, which is mainly concentrated on financial controls;
- SOC 2 Type I and Type II, which is based on 5 main principles of availability, security, processing integrity, confidentiality, and privacy of customer data;
- and SOC 3, which has the same trust pillars as SOC 2, including security, availability, processing integrity, privacy, and confidentiality, and which results are tailored for a general audience.
Find out more about SOC 2 Audits on GitProtect.io’s way to compliance:
📌 GitProtect passes certification for SOC 2 Type I
📌 GitProtect passes certification for SOC 2 Type II
HIPAA
The US Health Insurance Portability and Accountability Act (HIPAA) ensures that healthcare providers guarantee the confidentiality and security of digital health information and protect healthcare-sensitive data during storage and transmission. Moreover, under HIPAA, healthcare providers are required to take reasonable precautions against any threats, data security breaches, and improper use of health data.
Penalties for breaking HIPAA regulations might reach up to $50K, as well as imprisonment of up to 1 year.
NIS2 Directive
On December 14, 2022, the European Parliament published in its Official Journal Directive (EU) 2022/2555, also known as NIS2. According to the legislative act, all member states must guarantee that organizations take appropriate operational, technical, and organizational measures, based on an all-hazards approach, to address cybersecurity risks of network and information systems. Thus, the requirements shall include at least the following measures to deal with security concerns:
- guidelines for information system security and risk assessments;
- managing incidents;
- business continuity, including crisis management, backup procedures, and Disaster Recovery;
- supply chain security;
- security during the creation, acquisition, and maintenance of networks and information systems, including vulnerability management and disclosure;
- guidelines and practices for assessing cybersecurity risk management strategies and their efficiency;
- cybersecurity employee training and fundamental cyber hygiene procedures;
- guidelines and data handling practices for using encryption and cryptography;
- asset management, access control guidelines, and HR security;
- implementation of security measures such as 2FA or multi-factor authentication, and secure communication.
DORA
Other EU regulatory requirements are laid out in the Digital Operational Resilience Act, which is mainly aimed at solving the issue with the EU financial regulation. Within DORA, organizations must comply with regulatory requirements for detection, protection, containment, recovery, and repair competence against ICT-related incidents. This regulation sets rules on ICT risk management, operational resilience testing, incident reporting, and ICT third-party risk management and monitoring.
DORA entered into force on the 17th of January 2025, so companies already have to adapt their internal security policies and regulations within it.
Other security compliance frameworks
Among other security regulations that your business may need to comply with we should name: CCPA / CCPA, CIS Critical Security Controls, HITRUST that is aimed at helping organizations from various industries (especially when it comes to healthcare) manage data, compliance, and information risks effectively, PCI DSS, FISMA, FedRAMP, DCID, ISO 50001, and DOD standard.
Best Practices for Security Compliance
To comply with all the mentioned industry regulations and security standards, companies should do their best to develop effective security strategies as part of their internal cybersecurity program. Thus, among the best practices around security and compliance, we mention: the development and implementation of a robust risk assessment plan, powerful security controls, comprehensive backup and Disaster Recovery policies, the promotion of communication between teams, and security compliance automation. Employee training and continuous monitoring are also part of a well-formed cybersecurity program.
So, let’s look at those requirements in more detail.
A risk assessment plan: how to develop one?
Proactive measures are always the best way to address threats. If you adequately understand your weaknesses and can quickly identify vulnerabilities that your business may face, you can go one step ahead before a security risk strikes.
Conducting risk assessments can help your organization meet compliance regulations and fortify your organization from potential security incidents. To develop your own risk assessment plan, you should identify:
- what type of sensitive data you operate and where you store it,
- all possible threats to the sensitive data you handle,
- what or who can be harmed if there is a security incident (e.g, data breaches),
After figuring out all compliance gaps, you should record your findings. Don’t forget to review and update your risk assessment plan regularly to make sure you always have a valid and fast incident response tactic.
Implementing security controls to protect sensitive data
Security should always be in the first place. Compliance is only a set of regulations and rules on how to manage your organization’s security. Thus, your main goal should always be data protection that aligns with Compliance regulations.
Moreover, even if you follow the most secure compliance regulations, your organization can still experience security incidents. Let’s just remember the Okta case, when it suffered a hacker attack on its GitHub repositories.
What to learn more about data breaches, cyber attacks, and other incidents related to the DevOps stack? Check GitProtect’s CISO’s guide to DevOps threats.
Well, when you define your security controls, you should pay attention to:
- level of encryption for your business data,
- network access and identity controls,
- access permissions and role-based access controls,
- third-party tools access controls,
- firewalls and router management,
- ransomware protection measures,
- 2FA or MFA,
- incident response plan,
- constant monitoring and reporting,
- RTOs and RPOs.
Backup and Disaster Recovery Strategy: what should you include?
Backup is one of the main requirements to meet Compliance requirements, as it guarantees that the company can recover its data from any point in time, ensuring business continuity and operational efficiency. The possibility of following the 3-2-1 backup rule, replication between storage instances, long-term retention, and in-flight and at-rest encryption are among the backup best practices that can help organizations mitigate the negative effects of cybersecurity incidents, human errors, infrastructure outages, or other disasters that can lead to data loss.
What’s more, comprehensive backup software can help organizations with fast recovery in case of a failure, as it provides different restore options, including point-in-time restore, the possibility to restore to the company’s local device, to the same or new repository or organization account, granular recovery, or cross-over recovery to another Git hosting service, e.g. form Bitbucket to GitHub, GitLab, or Azure DevOps). In this case, businesses will be able to respond to any disaster scenario.
Automation: how does it make compliance processes efficient?
There are a lot of automated compliance management tools that aim at helping organizations save time in communicating that they meet strict security frameworks. Such tools assist in classifying the company’s data, provide real-time alerts, and have report capabilities to demonstrate that the organization follows the compliance requirements and that its risk mitigation controls are effective.
Educate your team about security compliance
Not all members of the organization’s team may understand the importance of your security compliance program. It’s obvious that IT or security and compliance teams are aware of the compliance regulations their company follows and act in accordance with security protocols. But what about non-security teammates? They may not know how to protect sensitive data or how to report security concerns if they stumble upon some. That’s why an organization should build adequate communication between all members of the team so that every employee understands well how to act within the security compliance framework.
☂️ Cyber insurance is your way to extra safety
Getting insurance against cyberthreats is what many organizations today consider. Interestingl, insurers, similarly to regulations, demand evidence of concrete safeguards. Read on to explore how data protection can affect both premiums and eligibility.
Conclusion – GitProtect.io backups & DR as a Compliance measure
All organizations, no matter what industry they operate in – healthcare, banking, IT, energy, etc. – need to follow different data protection best practices and security compliance protocols. Among numerous security measures and regulatory requirements, backup stands as one of the most critical aspects of all security policies and data collection laws. Why is it so? It guarantees data availability, accessibility, and recoverability from any point in time.
“GitProtect’s support for compliance standards and regulations has simplified our adherence to industry standards and legal requirements.” — says Kubilay Verboom, Cloud Engineer at SUE, one of the largest organizations that provides Cloud Native Solutions in Europe.
Read the full story on how SUE adopted GitProtect backups for the GitLab environment to guarantee its Disaster Recovery
Using GitProtect.io backup and DR software for DevOps tools, organizations can meet security compliance requirements. Moreover, it will help them enhance their DevOps security measures and help compliance teams stay in control. Thanks to Gitprotect.io’s data-driven dashboards, daily reporting, SLA, and Compliance reports, organizations can easily prove that their data is safe and they can restore it in any event of failure.
[FREE TRIAL] Try GitProtect.io’s DevOps backup for a 14-day trial to see how it can help your organization ensure security compliance
[LIVE CUSTOM DEMO] See in practice how GitProtect.io backup and DR software works – let’s discuss your needs within compliance requirements
The article was originally published on March 27th, 2024






