
Top Questions CISOs Should Ask: How To Guide The Development Of A Secure DevSecOps Strategy
With the threat landscape being on the rise, CISOs need to be much more attentive while building the organization’s security strategy. Constantly arising vulnerabilities, ransomware attacks, critical workflows, outages – all of that require CISOs to stay up to date to security issues and keep their finger on the pulse to change their security strategy once the prerequisites pop up.
🔎 We’ve been tracking GitHub, GitLab, and Atlassian -related incidents for the latest few years… Check the threat landscape of 2022 and 2023:
📌 GitLab Vulnerabilities and security incidents: 2023 in review
📌 Infamous GitHub-related incidents and threats: 2023 in review
📌 Atlassian security incidents: 2023 in review
📌 Ultimate review of the most infamous GitHub-related security incidents in 2022
📌 2022 in a nutshell: Atlassian outages and vulnerabilities
Well, in this blog post we are going to cover the main questions CISOs should ask themselves while building their DevSecOps strategy. So, let’s jump to the core topic…
Questions CISOs should answer to develop a secure DevSecOps strategy
Of course depending on the industry the organization operates in, those questions may slightly differ. Thus, for example, in the most regulated industries, like finance and backing, healthcare, insurance, and energy sector, which require a more secure approach to data protection, you may need to add more questions related to compliance and security audits. However, let’s try to stick to the core questions.
What are our organization’s security goals and objectives?
Probably, it should be the first question a CISO should ask himself when he starts building or rebuilding the company’s DevSecOps strategy to mitigate cyber risks. Why? Because defining clear security goals and objectives should become the basis of an effective DevSecOps strategy. These goals will serve as the guidance that aligns security initiatives and the overall business objectives. Thus, your team will be able to ensure that every step they take in the development process contributes to a secure and resilient environment. For example, let’s look at some objectives your organization may have:
- Security goals should support business broader objectives. It means that if customers’ trust and data protection is the company’s top priority, the company may focus on achieving industry certifications like ISO 27001, DORA, NIS 2, or maintaining security compliance with data privacy regulations like GDPR.
- KPIs should help the organizations track the effectiveness of security measures it adopts. These key performance indicators may include, for example, the number of vulnerabilities the security team detects and remediates, the time the company needs to respond to security incidents, and the percentage of apps passing security tests before deployment.
- Continuous improvement should be part of your security strategy. It means that your security goals and objectives should include provisions for regular reviews and updates to align with DevOps security practices to ensure that they can help you notice emerging threats and vulnerabilities on time to mitigate the risks.
🔖 Case Study
Company introduction? Let’s imagine, that you work in a financial institution that processes sensitive financial transactions for millions of users.
What’s the company’s objective? To provide seamless and secure digital operations, and protect its critical customers’ data.
What security goals and objectives should you set?
– Achieve compliance with PCI-DSS, GDPR, ISO 27001, SOC 2, and upcoming DORA regulation.
– Reduce Incident response time to 3 hours, and achieve minimal RPO and RTO objectives to be able to restore its critical data fast in case of an incident, by adopting backup and Disaster Recovery practices.
– Implement automated security testing into their CI/CD pipeline to identify and fix vulnerabilities early in the development lifecycle, which will help reduce the risk of security issues in production.
Outcome? By setting these specific goals and objectives, the company will not only align with its security efforts to meet its business objectives, but also will establish clear metrics to measure the efficiency of its security strategy. This approach will help the company ensure that security is an integral part of its development process, which leads to a more secure and reliable product for its customers.
What organization’s critical data we need to protect?
To ensure a comprehensive security and data protection, it’s important for an organization to understand which data is critical for its business. Such data can encompass all the information essential for the operation, reputation, and security of the organization. These data is possible to divide into a few categories:
| Data | Reasons to protect | Use Case |
| Intellectual propertydata | To maintain a competitiveness and prevent unauthorized use or theft you need to properly protect the company’s assets – Source code, proprietary software, designs, patents, trade secrets. | A tech company that develops cutting edge software. Thus, its IP are source code, algorithms, and design documents. To protect them, it should have robust access controls, secure code repositories, backup, etc. |
| Customer data | To maintain customers’ trust and comply with privacy regulations (GDPR, CCPA, etc.), it’s important to protect regulated type of data, including personally identifiable information, financial information, and transaction history. | An e-commerce company that collects and stores customer data, including names, addresses, credit card details, purchase history, etc. To protect such data, the company should implement encryption, access controls, and regular audits to detect and mitigate vulnerabilities. |
| Financial data | To prevent unauthorized access or tampering with fin data that lead to significant financial loss and legal repercussions. | A financial services company that manages vast amounts of fin data, including client portfolios and transaction records. To protect this data, the company should have advanced encryption mechanisms, 2FA or MFA, backup, continuous monitoring to detect and respond fast to unauthorized access attempts. |
| Operational data | To maintain smooth running of business operations and prevent disruptions. | A manufacturing company that relies on production schedules and detailed supply chain information to operate efficiently. To protect its data, the organization should implement secure communication, regular data backups and DR technologies to ensure its business continuity. |
| Employee data | To prevent unauthorized access to employee data that can lead to identity theft and legal issues. | A multinational corporation that manages extensive employee data in different regions. To protect the data, the organization should have secure HR management systems, encrypted storage, backup, and stringent access controls. |
How should we integrate security into our development pipeline?
It’s not a secret (or maybe it is!) that integrating security into the development pipeline is a fundamental practice in DevSecOps. In this case, it works as a proactive measure, as you embed security at every stage of the software development lifecycle.
It can help you to identify and mitigate vulnerabilities earlier, which reduces the risk of security breaches. At the same time, it can help your organization deliver secure and reliable software. Let’s look at the actions that organizations can use to integrate security into their development pipeline:
- shift security left, which allows to detect and resolve vulnerabilities before they become more complex and costly to fix,
- automate security testing to have a real-time feedback on security issues,
- implement secure coding practices to minimize vulnerabilities,
- use Infrastructure as Code to make sure that security configurations are consistently applied across all DevOps and business environments,
- have regular security reviews and audits,
- ensure that you have continuous monitoring and feedback,
- improve collaboration between development, security and operation teams.
What incident response and recovery plans should our organization have?
Your organization should be ready for any event of failure, whether it’s an outage, ransomware attack, data breach or data leak. To prepare for that you need to assume and outline all the actions your team should take to eliminate the consequences of an incident, how to communicate about the event, and, of course, ensure fast restore of business continuity as fast as possible.
Well, let’s look at the components of a comprehensive incident response and recovery plans:
- establish an incident response team, defining who is responsible for coordinating the response to the security incident and ensuring that all the necessary actions are taken;
- develop an incident response plan, which should outline the procedures and steps your organization should follow when a security incident occurs;
- implement incident detection and monitoring, for example, SIEM systems, IDC, and network monitoring tools;
- define incident classification and prioritization to see which incident require immediate attention and which are less critical;
- develop a communication plan to inform about a security incident;
- implement a reliable backup and Disaster Recovery plan to make sure that you can resume your workflow continuity fast and eliminate data loss;
Learn more about the best practices for building a reliable DR strategy in our dedicated series of articles:
📌 GitHub Disaster Recovery and GitHub Restore – Scenarios & Use Cases
📌 GitLab Restore And Disaster Recovery – How To Eliminate Data Loss
📌 Jira Restore And Disaster Recovery: Scenarios & Use Cases To Build Your DR Strategy
📌 Disaster Recovery: Bitbucket Ecosystem – What Are The Best Scenarios & Use Cases To Build Uninterrupted Workflow
- conduct regular trainings and simulations to ensure that your IRT is familiar with the incident response procedures;
- have post-incident reviews to analyze what incident response practices worked well and which need improvement.

How can we ensure compliance with regulatory requirements?
As we already mentioned, compliance with regulatory requirements is one of the goals that the organization may have (especially if we speak about highly-regulated industries!). Regulatory compliance involves adhering to laws, security regulations and guidelines, and some specifications relevant to organization’s business processes. What happens if an organization fails to meet compliance? Non-compliance can lead to penalties, legal issues, damage to an organization’s reputation.
So, to become compliant with strict regulations, you need to develop a comprehensive approach to ensuring compliance with regulatory requirements. It may include:
- Figuring out and understanding which regulations are relevant to your industry and what are their requirements (a lot of legal documentation reading!)
Example: A healthcare company that operates in the USA. It must comply with at least HIPAA, HITECH act, GDPR, CCPA, HITRUST CSF to protect its patient data. Thus, the company need to understand the specific requirements for data encryption, access controls, and audit trails.
- Conduct regular compliance audits to identify compliance gaps and ensure that all your processes and systems align to regulatory requirements.
- Implement security controls, including evaluating access controls, encryption, intrusion detection systems, and regular security updates.
- Develop and enforce policies and procedures that will outline how your organization complies with regulatory requirements.
- Educate your employees on compliance so that everyone in your organization understands his/her role in maintaining compliance.
- Use compliance management tools to automate and streamline the process of ensuring regulatory compliance.
- Monitor changes in regulations as they can change from time to time.
- Organize a compliance committee within your organization who can oversee all compliance-related activities within your organization.
Backup as part of your compliance strategy
Your DevSecOps strategy should align with compliance regulations, which ensures your data integrity and availability. Among other security measures, backup is one of the crucial aspects. It can help you guarantee data availability and recoverability from any point in time.
GitProtect.io backup and Disaster Recovery software for DevOps tools can help you on your way to compliance, as it allows you to keep your data in different storage locations (both cloud and local), follow the 3-2-1 backup rule, encrypt your data in flight and at rest with your own encryption key, and restore your data in any event of disaster – whether it’s a service or infrastructure outage, ransomware attack, human error, or any other event of failure. Moreover, with the GitProtect.io management console you can easily see whether your backup processes are compliant.
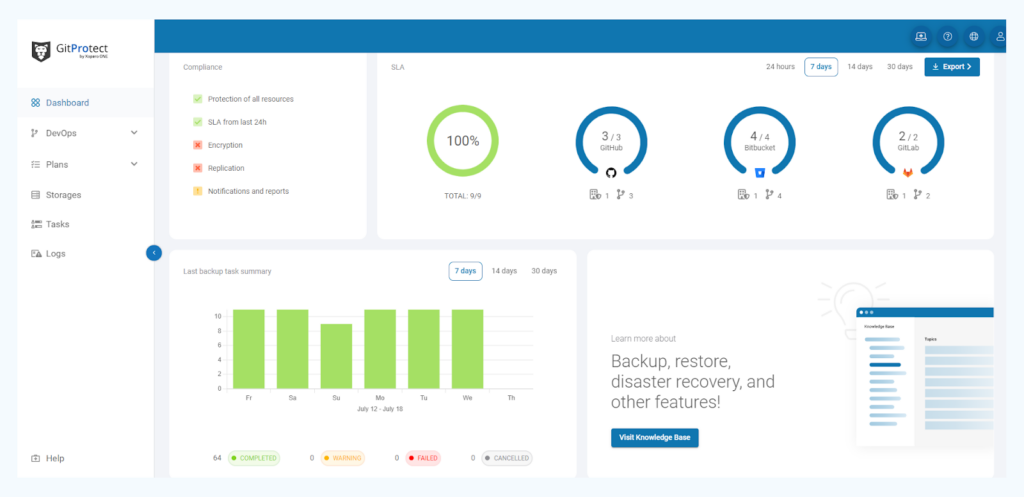
Check out how GitProtect.io backup solution helped it customers to meet compliance regulations:
“GitProtect.io’s robust features, coupled with GDPR and ISO27000 compliance, provide us with peace of mind regarding the integrity and confidentiality of our projects.”
Denis Stepanenko, Solutions Architect at Easytrip
🔎 Learn how Easytrip ensures its ISO27K compliant Bitbucket backup with GitProtect
“With GitProtect.io we were able to bring all our Git repositories into backup compliance with the use of a single tool.”
Mark Pace, CTO at Red5
🔎 Read more on how Red5 adopted GitProtect backups for GitHub and Jira to meet its compliance
[FREE TRIAL] Ensure compliant DevOps backup and recovery with a 14-day trial🚀
[CUSTOM DEMO] Let’s talk on how backup & DR software for DevOps can help you mitigate the risks






